Reviewing Proxy logs
The Proxy logs are where admins go to review all user activity (events/logs/etc) in all protected applications associated with inline access control and DLP policies.
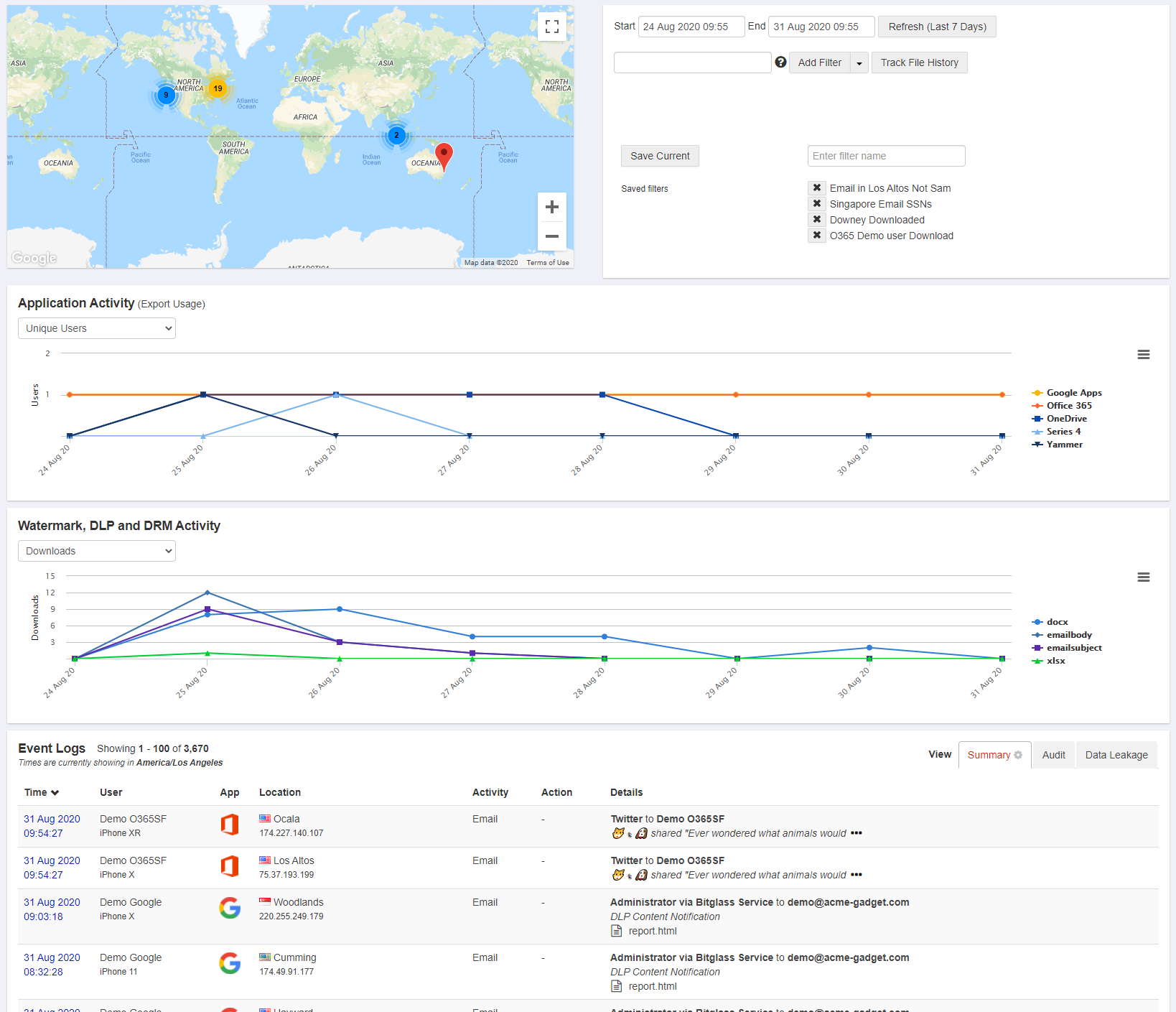
The Proxy logs can be found under and are broken down into four cards providing a holistic and highly customizable view of user's proxy activity.
Note: Review the Data Retention Policy to learn about how long data is retained and displayed in the Proxy Logs.