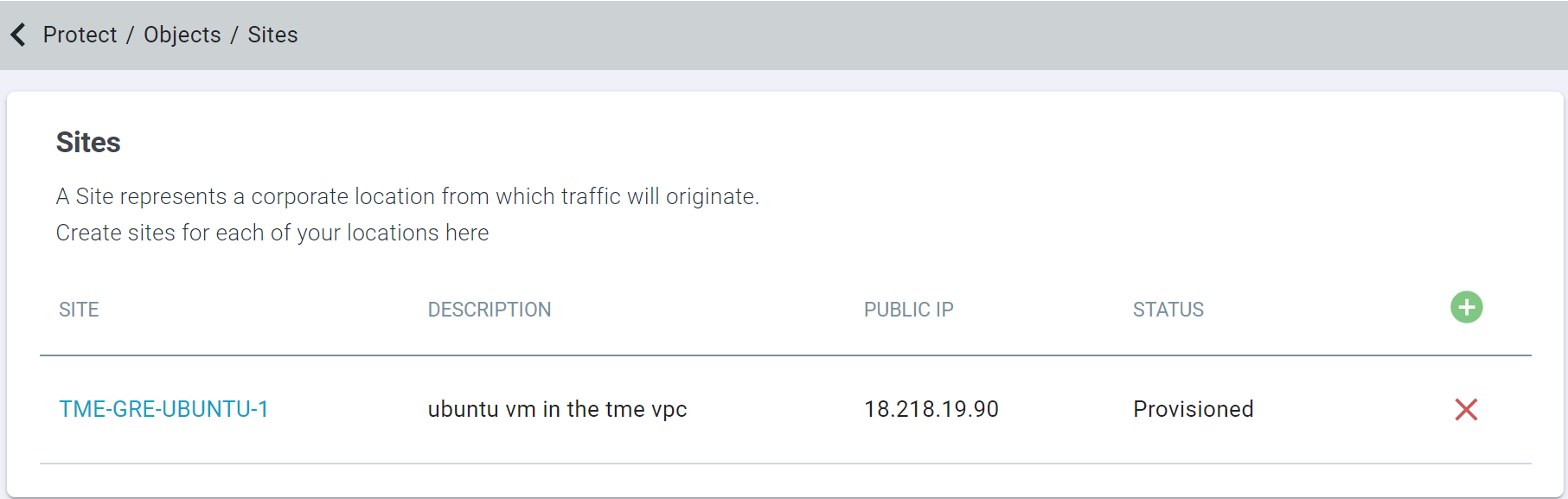
A Site represents a corporate location from which traffic will originate. While creating Site, you can configure either GRE or IPsec tunnel through which traffic should be sent over to cloud and create or add subnets groups within the site.
Steps
- Navigate to Protect > Objects > Sites.
- On the Sites page, click the green plus icon.
-
On the General tab:
-
Enter a unique Name of the Site.

- Select the appropriate TimeZone of the corporate IP location.
- Enter Description for the Site.
-
Select the Tunnel option as the Type of the site.
Available options are:
- Tunnel (default) - Select Tunnel if you want to create GRE or IPSec tunnels so that web traffic from the site is
forwarded to Cloud SWG via tunnels.Note: When Type is set to Tunnel, then the Tunnel tab is available.
- Explicit Proxy - Select Explicit Proxy if you want to forward the web traffic from the site to Cloud SWG using a PAC file.
- None - Select None if the Site is with an on-premise proxy that sends traffic direct to the internet (without sending it to the Cloud SWG).
Note:- The Type cannot be changed once a Site is created. You can delete and create new site with correct Type.
- Based on the Type selected, available options under the Agent Overrides tab vary.
- Tunnel (default) - Select Tunnel if you want to create GRE or IPSec tunnels so that web traffic from the site is
forwarded to Cloud SWG via tunnels.
-
Enter the Public IP address of the site.
Forcepoint ONE SSE validates the IP address to make sure that the value is actually an IP address and is not a duplicate of another site with same IP address that is already created.
Note: You can enter a Dynamic IP address, IP address that was assigned dynamically by any one of the ISPs connected to the site, in the Site's Public IP field on the General tab. This Dynamic IP address can change over time and is simply used as a tag to match any Location Policies for the site on the Protect > Policies page. -
Set the Identify Coordinates to Automatic to identify the location of the site based on entered IP address when you click
Detect Location.
The Location field displays the location name of the entered IP address to which your web content will be localized.
-
If Forcepoint ONE SSE is unable to identify the correct location or did not display the location of the entered IP address, then:
- Set the Identify Coordinates to Manual.
- Select the applicable Localization Country to which your web content should be localized.
Cloud SWG uses an egress IP address corresponding to the Localization Country selected to send proxied traffic to its destination. If the selected localization country is not available, the country of the Cloud SWG datacenter processing the traffic will be used instead. To know about the supported localization countries list, refer to Cloud SWG vPoP IP addresses.
Note: For existing Sites, where the Localization Country was not available for selection, is set so that you can select Localization Country later.
-
Enter a unique Name of the Site.
-
On the Tunnels tab, create tunnels to route the traffic from site to Forcepoint ONE SSE cloud:
-
Select the Type of tunnel through which traffic will flow from the Site to the Forcepoint ONE SSE cloud.
- GRE - Select GRE option to route the traffic from the Site to the Forcepoint ONE SSE cloud via GRE tunnel.
- IPsec - Select IPsec option to route the traffic from the Site to the Forcepoint ONE SSE cloud via IPsec tunnel.
- None - A transition from GRE to IPsec or vice versa requires switching to None and saving first.
Note: A transition from GRE to IPsec or vice versa requires switching to None and saving first. -
To create a GRE tunnel, follow the steps below:
- Select the Type as GRE.
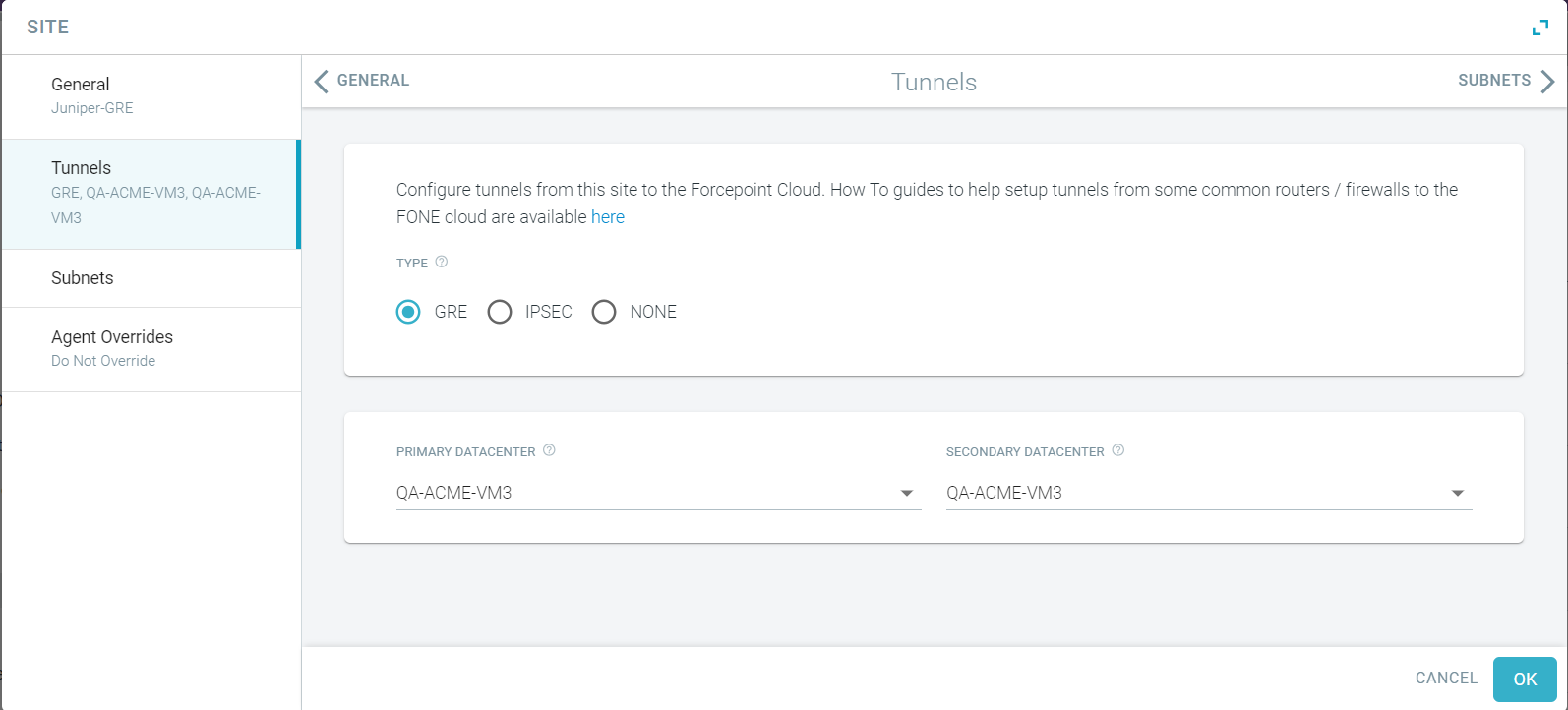
- Select the datacenter where the primary tunnel from the site is terminated.
- Select the datacenter where the secondary tunnel from the site is terminated.
Select a datacenter that is in a different Region or Zone than the Primary Datacenter. If you do not want to assign secondary datacenter, then select None from the Secondary Datacenter drop-down list.
- Select the Type as GRE.
-
To create an IPsec Tunnel, follow the steps below:
- Select the Type as IPsec.
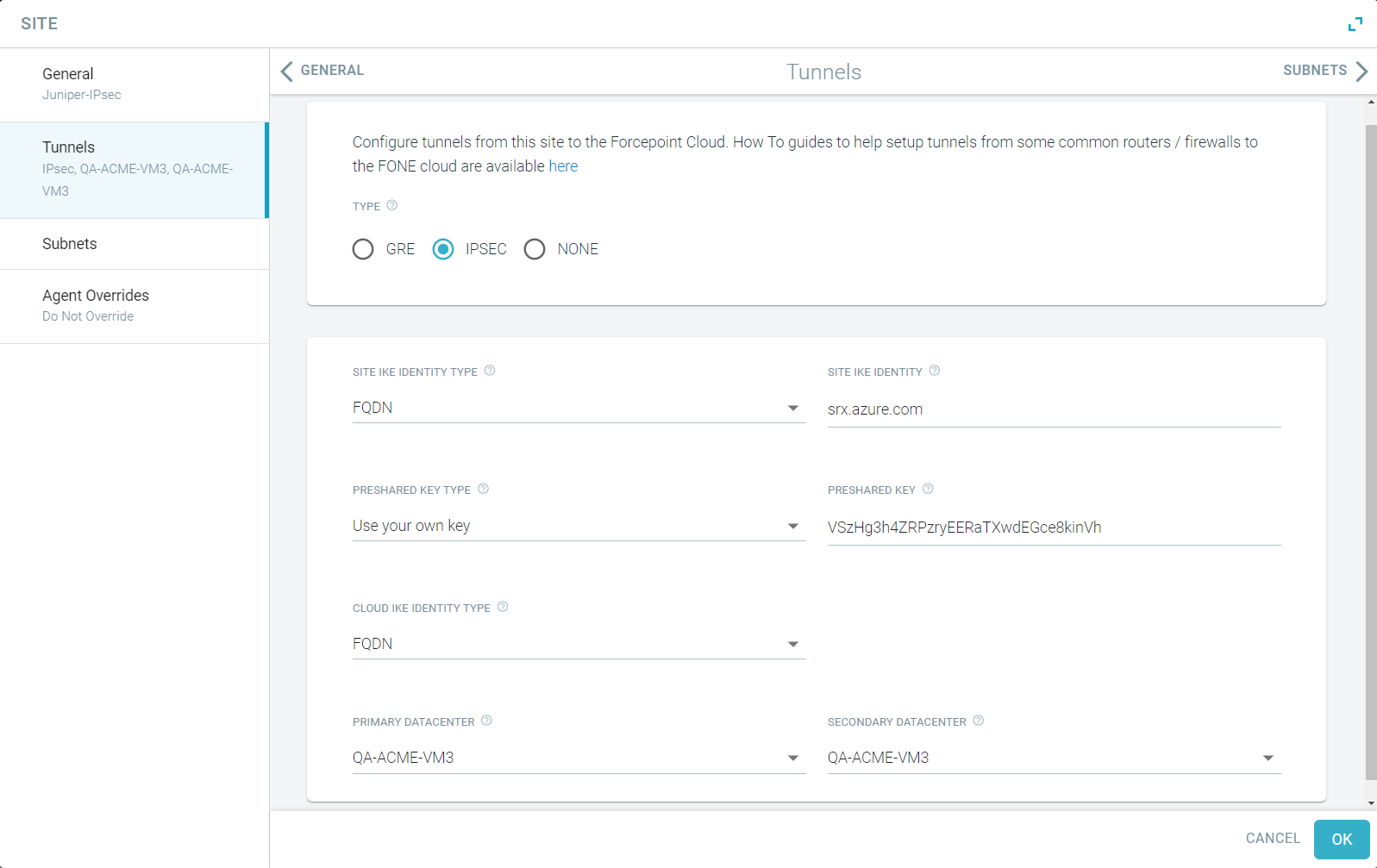
- Select whether the Site uses its Public IP address or a FQDN from the Site IKE Identity Type.
- Enter either public IP address or a FQDN of the site in the Site IKE Identity as per the Site IKE Identity Type
selection.Note: When the Site IKE Identity Type is set to FQDN, then you can enter a Dynamic IP address, IP address that was assigned dynamically by any one of the ISPs connected to the site, in the Site's Public IP field on the General tab. This Dynamic IP address can change over time and is simply used as a tag to match any Location Policies for the site on the Protect > Policies page.
- Select whether you will Use your own key or an Auto-generated key from the Preshared Key Type.
- Enter the Preshared Key configured on the site router or firewall.
OR
Click Generate Key to auto-generated key and use the key while configuring the site router or firewall.
Note: The Preshared Key is case sensitive and must be minimum 8 characters long. - Select whether the Site uses Cloud Public IP address or Cloud FQDN as IKE ID from Cloud IKE Identity
Type.
By default, FQDN is selected.
- Select the datacenter where the primary tunnel from the site is terminated.
- Select the datacenter where the secondary tunnel from the site is terminated.
Select a datacenter that is in a different Region or Zone than the Primary Datacenter. If you do not want to assign secondary datacenter, then select None from the Secondary Datacenter drop-down list.
- Select the Type as IPsec.
-
Select the Type of tunnel through which traffic will flow from the Site to the Forcepoint ONE SSE cloud.
-
On the Subnets tab, define subnets or reuse the configured subnets within the site:
Subnets are unique within a site. However, in large cookie cutter network deployments, the same subnet may be used in multiple sites. Combination of Site and Subnet is globally unique.Note: Subnets should be defined when Site Type = Tunnel. Subnets do not have to be defined when Site Type = Explicit Proxy as the cloud does not have visibility into internal IP addresses.
-
To add Subnet(s) defined in Protect > Objects > Custom Locations page:
- Click the green plus icon.
A Subnet appears.
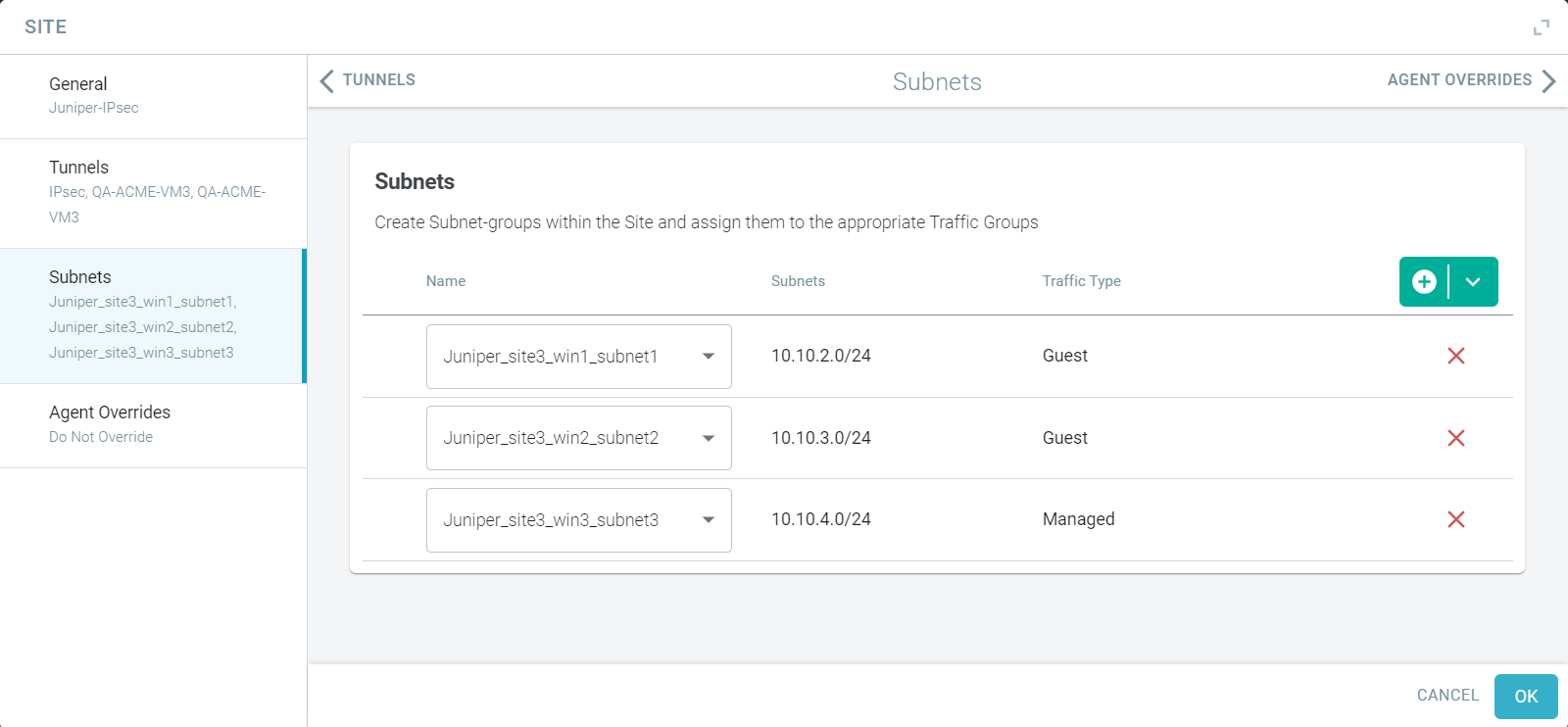
- From the Name drop-down list, select the applicable subnet.
The details of selected subnet appears.
You can add as many subnets as required.
- Click the green plus icon.
-
To create a new subnet for the site:
- Click
 and select Create
New.
and select Create
New.Create Subnet dialog opens.
- Enter a unique Name of the location for easy identification.
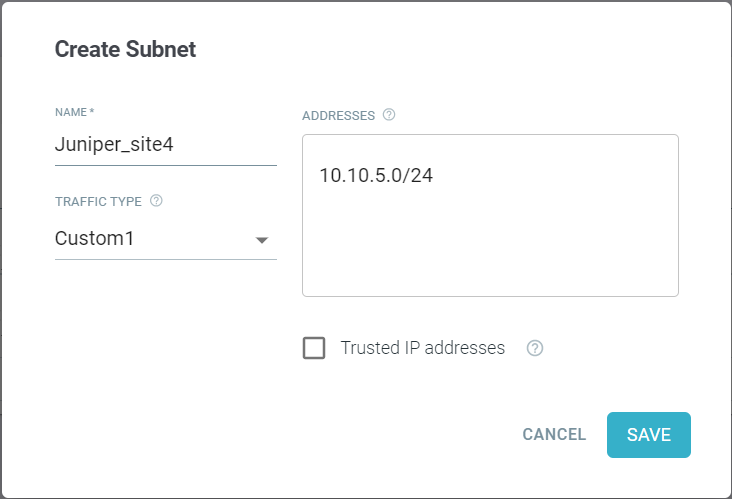
- Select the Traffic Type for the subnet addresses in the custom location.
- Enter the IP Address one per line in CIDR notation.
Custom locations should be external internet facing addresses and can be an IP address, subnets, or ranges on individual lines.
- Leave the Trusted IP addresses checkbox unchecked.
- To save the custom location details, click Save.
- Click
-
To add Subnet(s) defined in Protect > Objects > Custom Locations page:
-
On the Agent Overrides tab, define what should the SmartEdge agent do when it arrives at a site (office location) that has transparent proxy
configured.
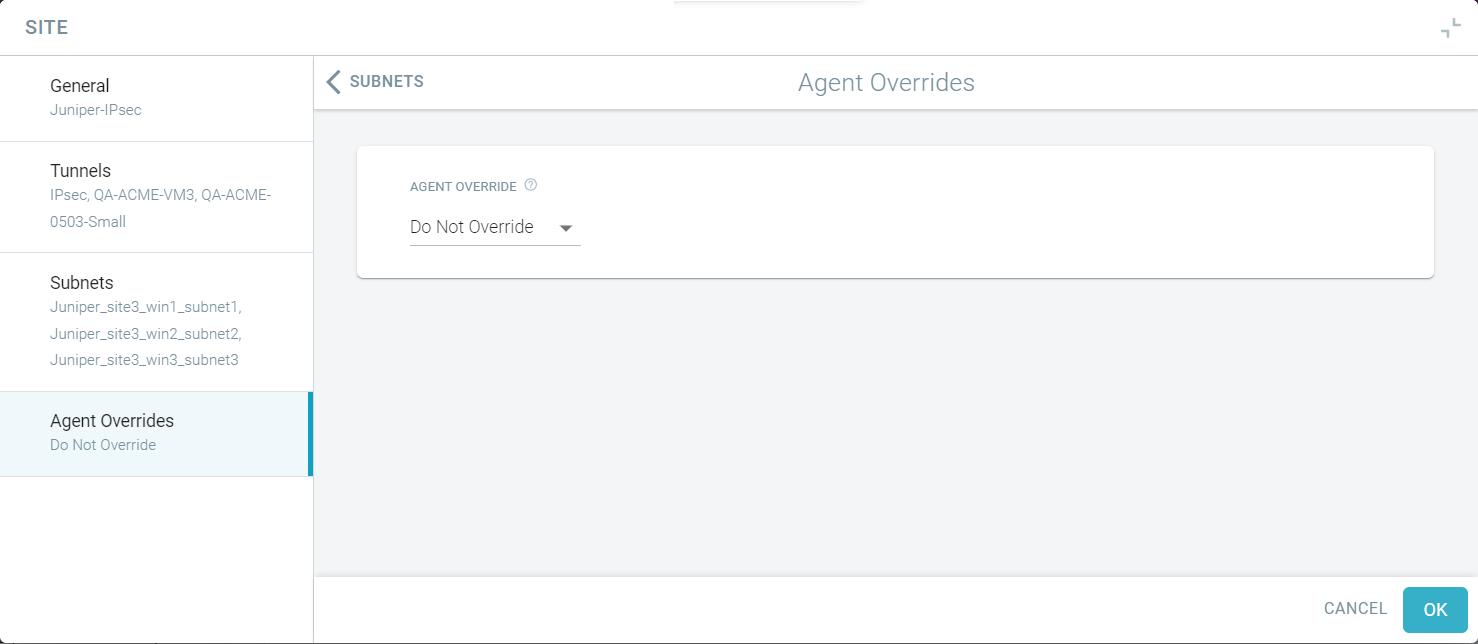
Note: If Set PAC is unchecked on the Protect > Forward Proxy > SmartEdge Proxy page or on the Analyze > Devices > SmartEdge Agent > Details page, then the user device with the SmartEdge agent will ignore the Agent Override setting and will not set the system proxy.From the Agent Override drop-down, select the desired behavior of the SmartEdge agent 2.1.0 or latest version when it is at the site:
- Do not override (default) - Selecting the Do not override option enables the SmartEdge agent to operate as it does at remote location. To make sure the SmartEdge agent filters the web traffic correctly, you should enable access to port 80 and 443 to the entire internet.
- Do not set PAC - Selecting the Do not set PAC option disables the SmartEdge agent from setting the PAC when at the site so that the Admin can setup their own PAC file using other mechanisms.
Note:- For the older versions of SmartEdge agent (previous to 2.1.0), the SmartEdge agent will behave as if Agent Override is set to Do not override irrespective of what behavior you have selected.
- Available options vary based on the Type selected on the General tab.
-
To configure a site with selected information, click OK.
As soon as the Site is created, the status of Site will be Configuring. After some time, the status of the Site gets changes to Provisioned or Failed.
Note: Tunnel typically takes approximately three minutes for it to be Provisioned.