Before configuring any connection policies, it is important to review the Bypass and Exclusion Controls and Bypass Domains, Host IPs or Subnets for SmartEdge Agent and Bypass Domains, Host IPs or Subnets for Cloud SWG.
This will walk you through setting up the agent or Cloud SWG to either proxy all traffic or just specific traffic. Customers who proxy all traffic might need to configure exceptions based on variables such as groups, device, host app, category, etc.
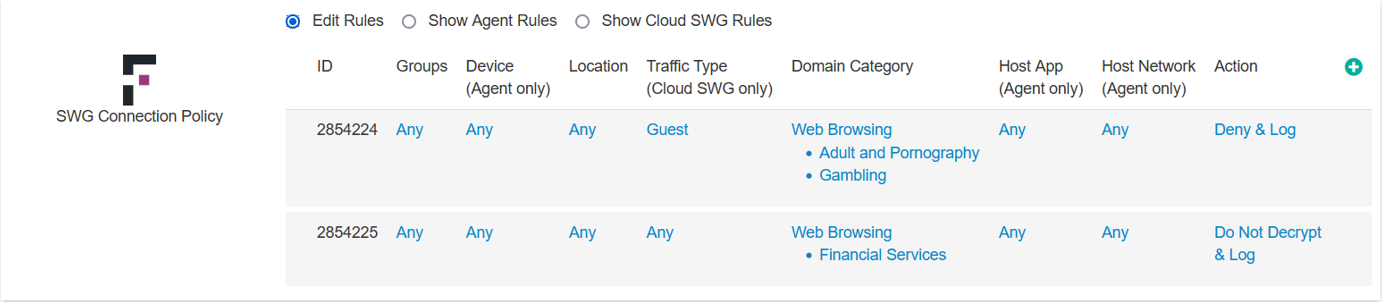
- On IoT and Embedded devices, SSL decryption cannot be performed as CA certificate cannot be installed. Therefore, Traffic-Type based connection policy must be used to perform web filtering.
- The SWG Connection Policy is enforced when the SmartEdge agent is placed in the Managed App traffic only mode.
You can select one of the following options to filter the rules and make sure if the rules are configured correctly for Agent and Cloud SWG:
- Edit Rules display all columns and permit you create, edit and delete the rules. By default, this option is selected.
- Show Agent Rules display rules that are applicable only for SmartEdge Agent, that is hides Cloud SWG only column. You can only view rules when you select this option.
- Show Cloud SWG Rules display rules that are applicable only for Cloud SWG, that is hides Agent only columns. You can only view rules when you select this option.
If no connection policy rules are configured, then the implicit policy automatically continues evaluation to the authentication and content policies.
You can configure a number of variables and apply an exception action to prevent Forcepoint ONE SSE from proxying traffic:
- Groups: Select the user/groups you want to apply to.
- Device (Agent only): Select the managed devices (via Device Profile in or Client Cert you want the policy to apply to.
- Location: You can restrict or control where a user is accessing the website or application from (either geographic location or IP).
- Traffic Type (Cloud SWG only): Select the traffic type on which policy should be applied.
- Domain Category: You can select the web app category via our category list or a configured custom url category in page.
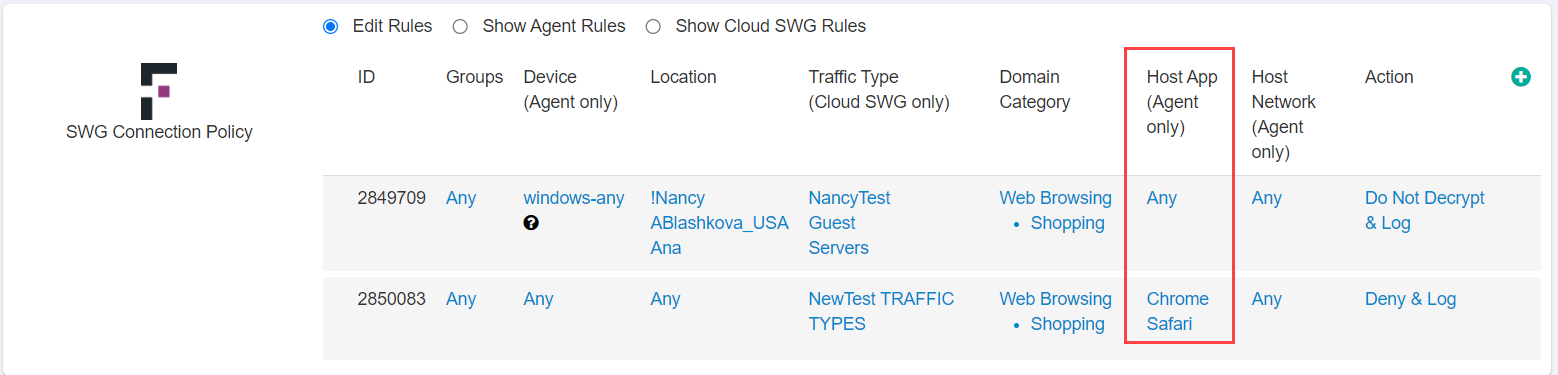
- Host App (Agent only): Unique contextual variable to connection policies, can select the specific host app that is allowed the bypass (selecting a specific web browser or chat app).
- Host Network (Agent only): Can be configured to identify when users are on the corporate network to allow the bypass.
- Action: Can choose Do Not Decrypt to bypass the proxy and traffic direct to the destination or Deny to deny access outright
based on the configured variables above. Can also choose to generate a log when the policy is triggered.Note: For the Cloud SWG, when the SWG Connection Policy is set to Deny & Log for a particular domain category, then the website displays This site can't be reached error while accessing it.
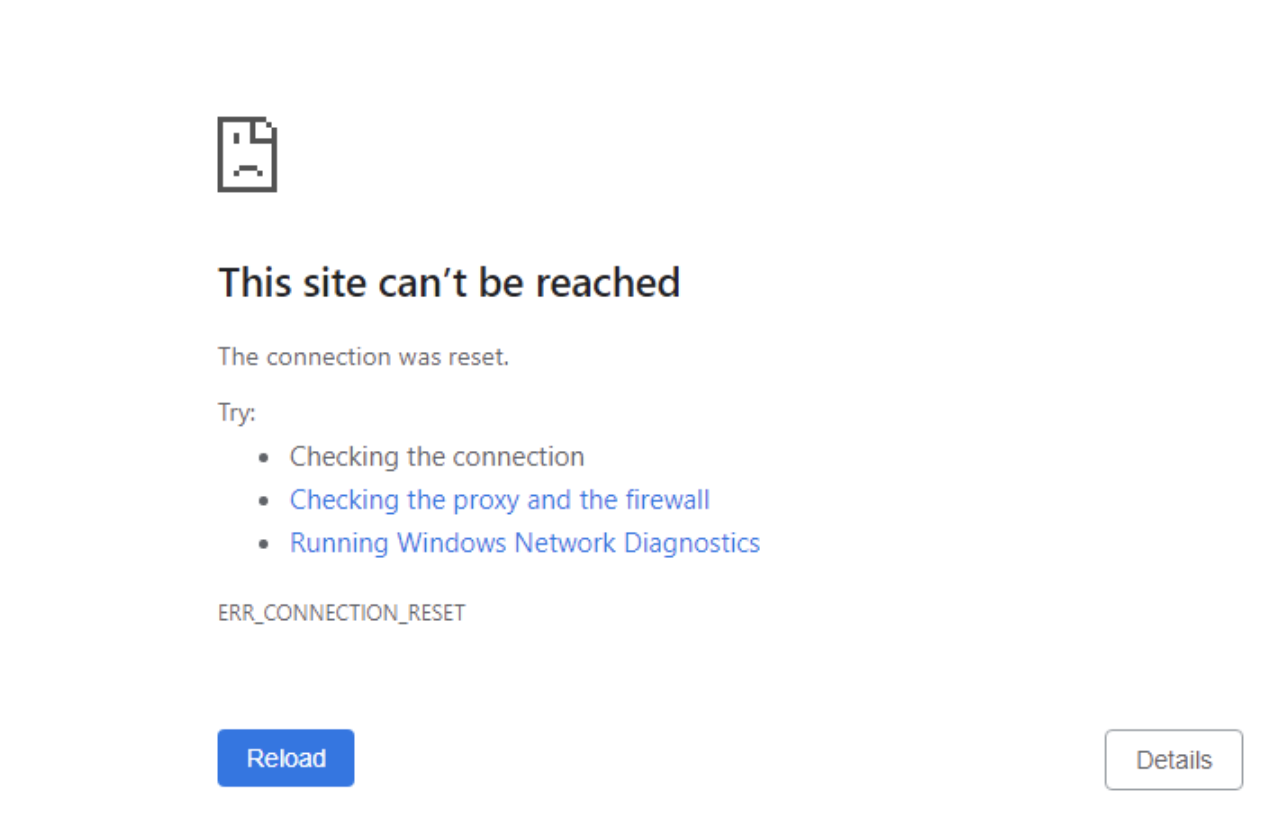
While Groups, Location, and Device are treated the same as any of our other policy setups, the other columns are unique to SWG Connection Policy.
Groups
Locally defined groups or security groups and OUs pulled from active directory. You can add as many groups as are needed for the policy. You can also negate the group so that policy line applies to everyone except the group you selected.
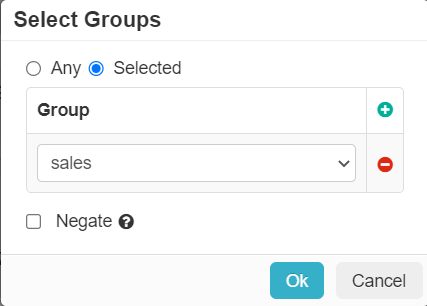
- Specific User groups are not supported in the SWG Connection Policy currently when the Site Type is set to Explicit Proxy together with the Agent Override set to Chain to Explicit Proxy in the Agent Overrides tab. In such a case, the user Group must be set to ANY in the SWG Connection Policy.
- This restriction does not apply to Agentless Explicit Proxy use case and to other agent override options when the Site Type is set to Explicit Proxy, that is Do Not Override and Do Not Set PAC.
Location
The Location column allows you to restrict or control where a user is accessing the cloud application from (either geographic location or IP).
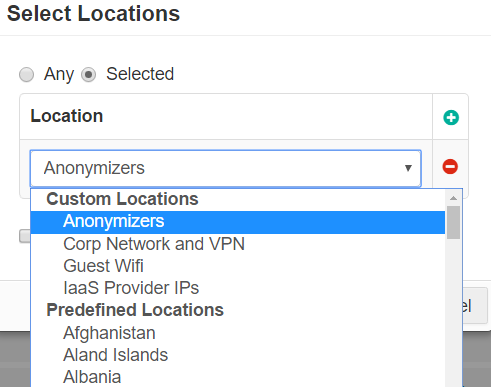
To use a location based policy for managed applications, the location object must contain the IP address of the Cloud-SWG datacenter. When the device is in the office, since traffic is tunneled to the Cloud-SWG, the Reverse Proxy sees the Cloud-SWG IP address and uses it to match the location configured in the managed app policy. Additionally, the location object should also contain other remote office locations that are also permitted.
- Custom Locations can be configured under . Custom locations also include predefined locations that are not based on countries (for example, Anonymizers and IaaS Provider IPs). These locations are managed and updated by Forcepoint ONE SSE.
- Predefined locations include a list of countries. Country match is done using a geo-IP lookup to match source IP address to country.
Device
The Device column allows you to set contextual access controls based on the users device (OS/user agent, managed vs unmanaged, and so on).
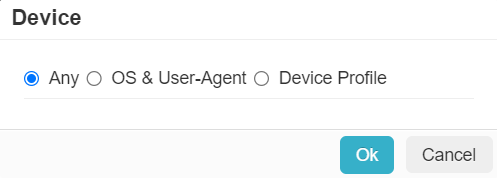
- OS & User-Agent: Allows you to match from a predefined set of common operating systems and/or User-Agent Strings.
- Device Profile: Allows you to match on Device Profiles which are managed under .
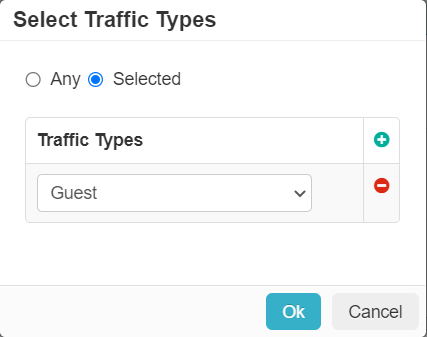
Traffic Type
The Traffic Type (Cloud SWG only) column allows you to select the traffic type so that policy can be applied to the group. You can select from the options in the drop-down or you can go to the page to create a custom traffic type.
Domain Category
The Domain Category column allows admins to provide controls over entire categories of applications. This allows you to configure if the end user connecting to specific category over the cloud proxy should be redirected to the domain's identity provider for authentication or not.
- For the Webroot URL Categories, you should see UI similar to the following:
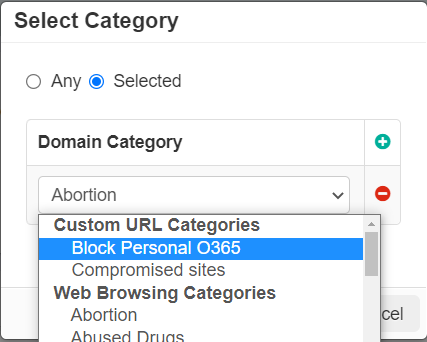
Refer to Webroot URL Categories.
- For the ThreatSeeker URL Categories, you should see UI similar to the following:
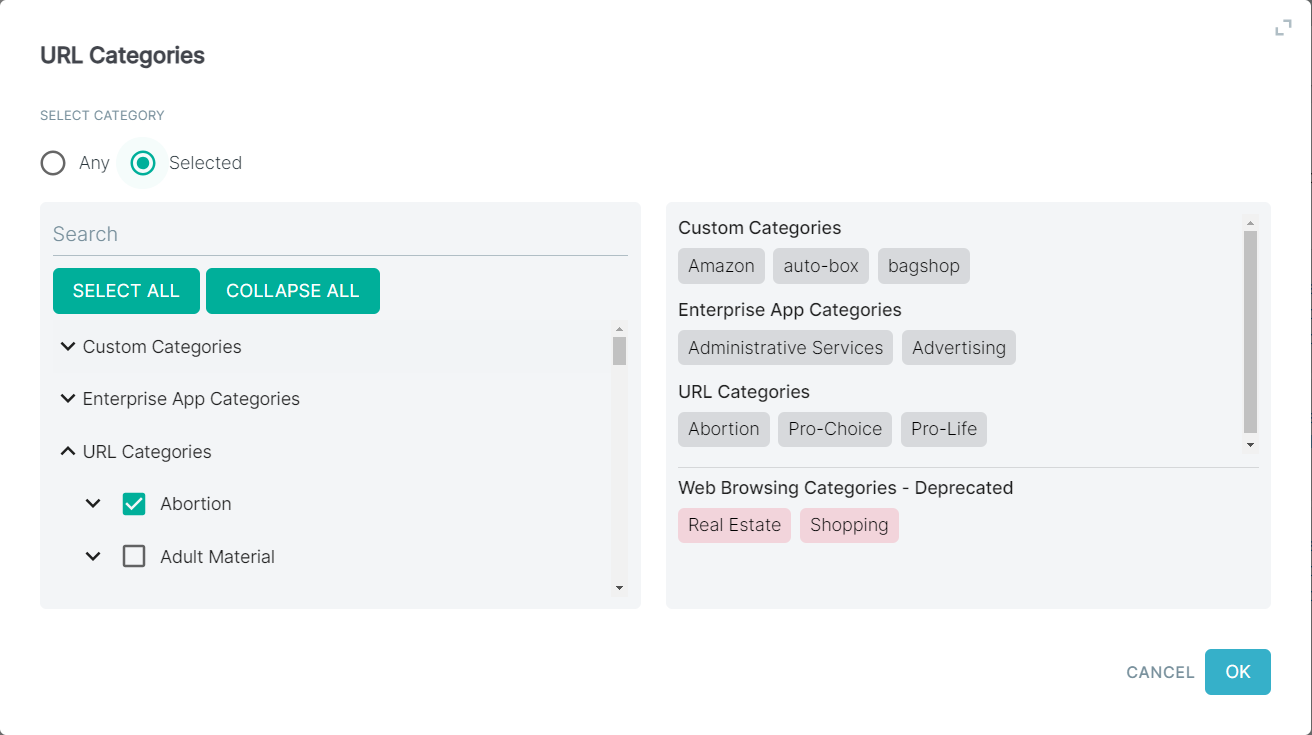
Refer to ThreatSeeker URL Categories.
You can use the inbuilt URL Lookup page to know the ThreatSeeker URL Categories, Enterprise App Categories, Web Browsing Categories along with their respective reputation scores for the entered URL or IP. Refer to Understanding URL Lookup page to know in detail.
Webroot URL Categories
You can select Webroot URL category from the options in the dropdown or you can go to the Common Objects page and create your own.
- Click into the Domain Category column link to open the dialog options for choosing which categories you will be controlling.
- In the Select Category dialog window, you will have two options: Any (which will apply the policy line to all categories)
and Selected where you can add the categories to the policy line. Click on Selected:

- You will notice 3 different Sections for Categories.
-
Custom URL Categories: These can be defined on the page where you can create a custom domain category to use in policies (that is creating a allow list or a custom list of domains to block).
On clicking Save on the page, the save action will fail and will display an error message if the number of unique custom URLs is more than 3000 across all or any of the SWG policies.
- Web Browsing Categories: This list of categories is sourced from Webroot and can be reviewed on their site.
- Enterprise App Categories: This is the list of categories that Forcepoint ONE SSE tracks and identifies and can be seen when looking through our cloud app repository.
-
- Click the green plus icon and select the desired category from the dropdown. You should select maximum of 50 categories per a policy rule.
- To add the selected categories to policy rule, click OK.
- To save the policy, click Save on the Policies page.
When you click Save after adding more than 50 categories per a policy rule, then the Error saving, status: error - Please check the following policies with IDs xxxx to ensure the amount of URL Categories per policy are 50 or under. error is displayed. You can avoid this error by creating two or more policy rules within SWG policy, with each policy rule having a URL category limit set to 50 or fewer.
ThreatSeeker URL Categories
You can select ThreatSeeker URL category from the options in the drop-down or you can go to the Common Objects page and create your own.

You can select all the ThreatSeeker URL Categories by selecting the All option or select desired category or categories by selecting the Selected option.
- Click the categories from the policy. This opens the URL Categories dialog.
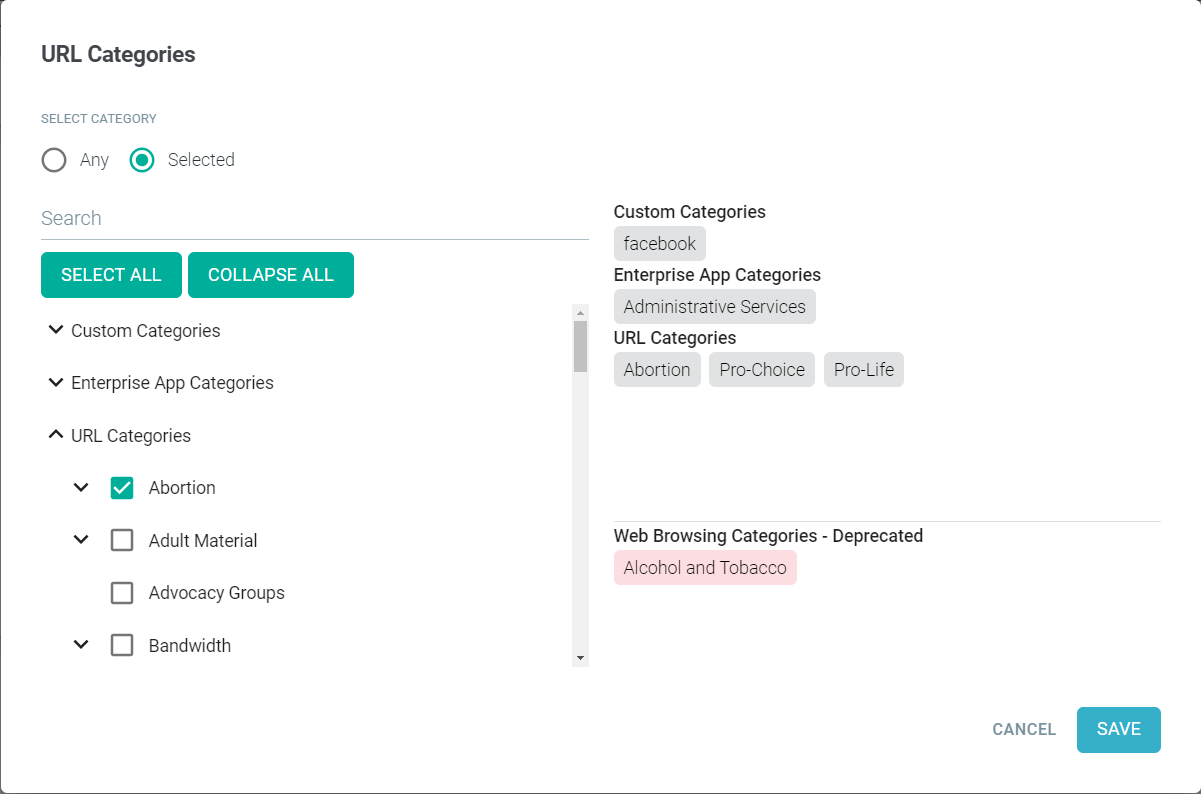
When ThreatSeeker URL Categories feature is enabled and when you modify an existing policy containing Webroot URL categories, then the URL Categories dialog displays the selected Webroot URL categories in red chips under the Web Browsing Categories - Deprecated section.
You should replace the Webroot URL Categories with the equivalent ThreatSeeker URL Categories. To know the mapping of Webroot to ThreatSeeker URL categories, refer to Mapping between Webroot URL Categories and ThreatSeeker URL Categories.
To submit uncategorized or incorrectly categorized sites, refer to How to submit uncategorized or incorrectly categorized sites.
- You will notice 3 different Sections for Categories.
-
Custom Categories: These can be defined on the page where you can create a custom domain category to use in policies (that is creating a allow list or a custom list of domains to block).
On clicking Save on the page, the save action will fail and will display an error message if the number of unique custom URLs is more than 3000 across all or any of the SWG policies.
- Enterprise App Categories: This is the list of categories that Forcepoint ONE SSE tracks and identifies and can be seen when looking through our cloud app repository.
- URL Categories: The list of ThreatSeeker URL categories.
-
- Expand the desired section and scroll down until you identify the desired category.
You can also filter categories by entering the text in the Search field.
- Expand the category if the category is associated with sub-categories.
- Select the check box next to the category or sub-categories. You should select maximum of 50 categories per a policy rule.
When you select Custom categories, Enterprise Categories or ThreatSeeker URL Categories, the selected categories are displayed as chips under their own section on the right of the dialog.
- To save the selected categories, click OK.
When you click OK after adding more than 50 categories per a policy rule, then the Please limit your entry to 50 URL categories or fewer to proceed successfully. error is displayed. You can avoid this error by creating two or more policy rules within SWG policy, with each policy rule having a URL category limit set to 50 or fewer.
- To save the policy, click Save.
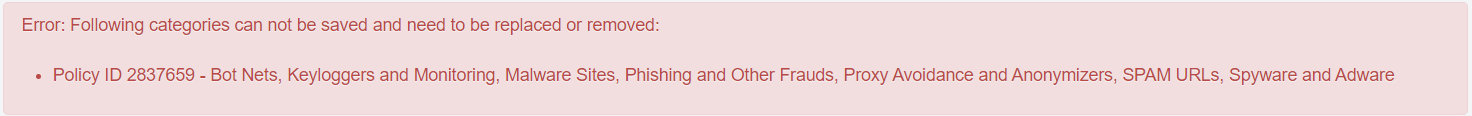
When ThreatSeeker URL Categories feature is enabled and when you save the existing policy containing Webroot URL categories after modifying the policy, then the Following categories cannot be saved and need to be replaced or removed: error will be displayed.
For example:
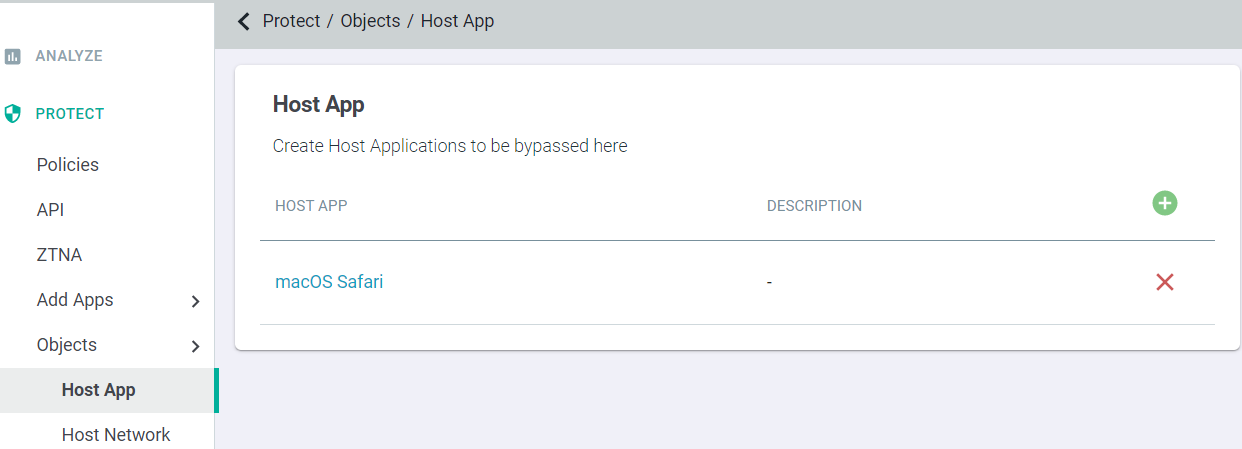
Host App
The Host App column allows you to select a preconfigured app that will be recognized in order for the policy to apply. You can create new Host App objects under .
- Navigate to in the left column. On the Host App page, you will see a table where you can add new Host App objects. You can add more than one app to a single object or
you can split them into separate objects depending on how you want your policies setup.
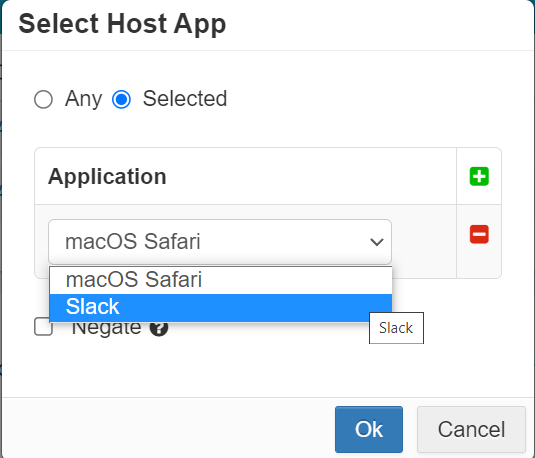
- Click the green plus icon to bring up the create Host App dialog window. Provide a name for the object and then optionally a description. In the big text box enter the
path to the application separating multiple apps by line.
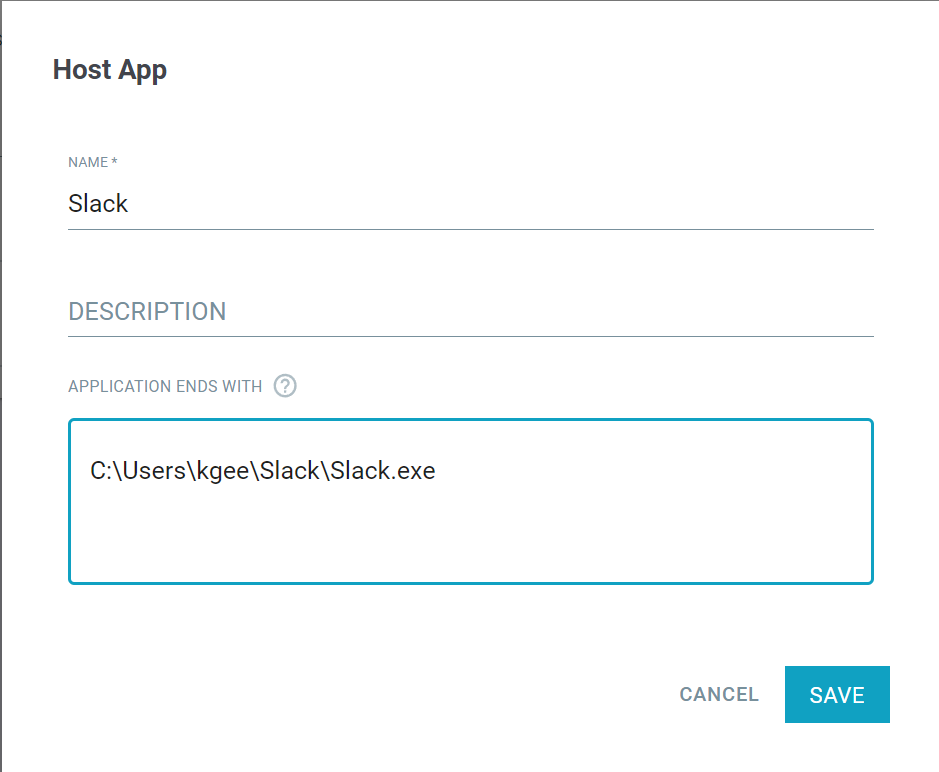
- With the object created, you can now select it in your connection policy under the Host App (Agent only) column.
Host Network
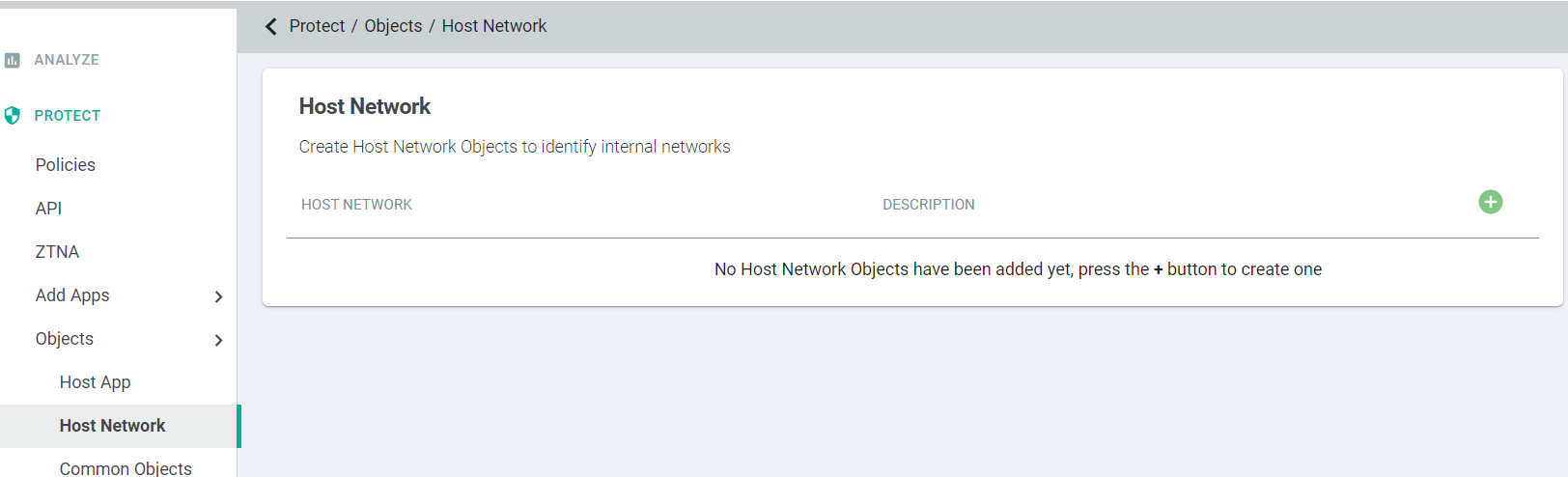
The Host Network object allows you to specific DNS servers/ranges to identify in order to match devices coming from the corporate network to apply exclusions (users coming from a corporate secure location can have the proxy bypassed).
- Navigate to and you will see a table where you can create new objects to represent a Host Network or networks.
- Click on the green plus icon and in the create Host Network dialog window, provide a name for the object and optionally a description.
You will see two text boxes to fill out (DNS Server and DNS Suffix). The policy is an "And" of both boxes but both do not need to be filled out.
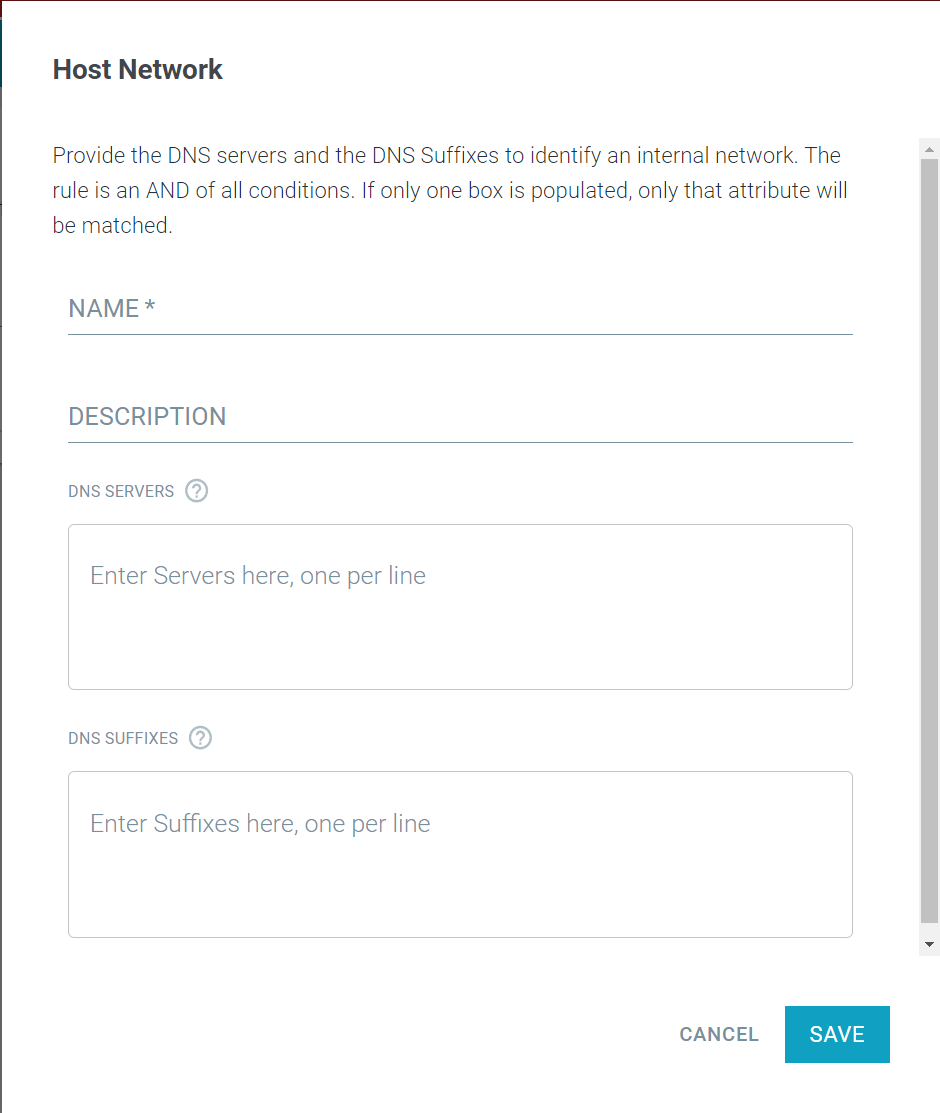
- DNS Server: You can enter valid IPv4 or IPv6 addresses and can add a maximum of 32 DNS servers.
- DNS Suffix: Can contain only upper/lower case alphabetical or numeric characters along with minus (-), underscore (_), or period(.). The object supports a max of 16 DNS suffixes.
- Once created, you can now select it on the policies page under the Host Network (Agent only) column.
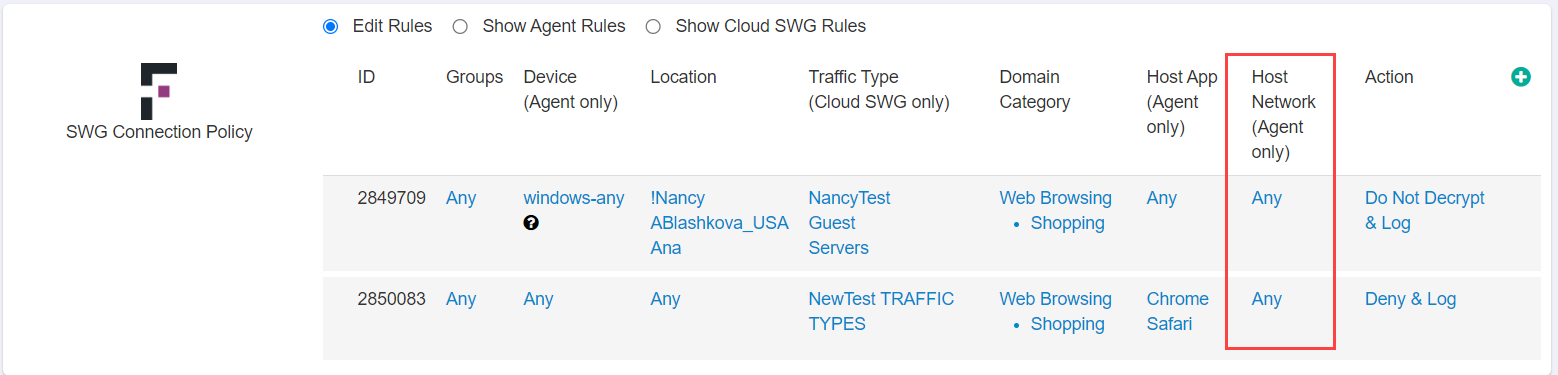
Action
Once your column variables have been configured, you can now select the action to apply.
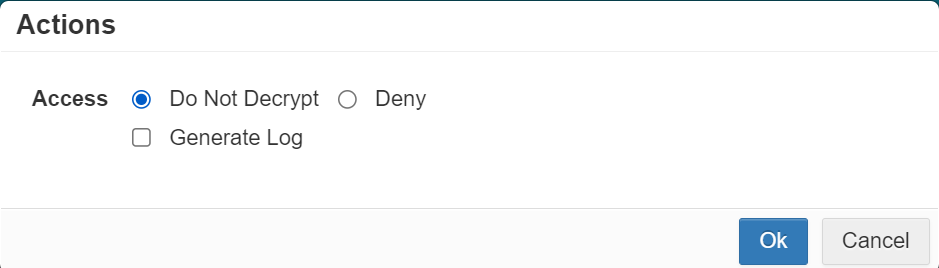
Your options are:
- Do Not Decrypt: Will not perform SSL termination so the traffic will not be proxied.
- Deny Inline: Will block the connection altogether.Note: For the Cloud SWG, when the SWG Connection Policy is set to Deny & Log for a particular domain category, then the website displays This site can't be reached error while accessing it.

- Generate Log: Will generate a log line of the action performed on the page.