Alerts
Alerts provide quick access to important events and information. The main navigation provides an updated counter of new events as they occur based on user activities by categories.
To analyze alerts, you can access the Alerts page using one of the following ways:
- On the upper-right corner of the Forcepoint Data Security Cloud | SSE, click the bell icon.
- Navigate to .
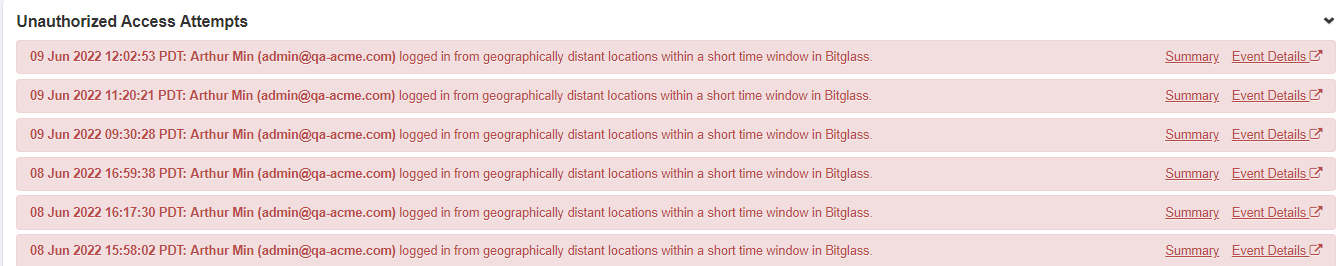
- Unauthorized Access Attempts: This category of alerts applies to events where Forcepoint Data Security Cloud | SSE suspects an unauthorized attempt to use an account.
Example events include a series of failed login attempts on a specific user’s account, or a user attempting to login from diverse geographic locations within a short time window.
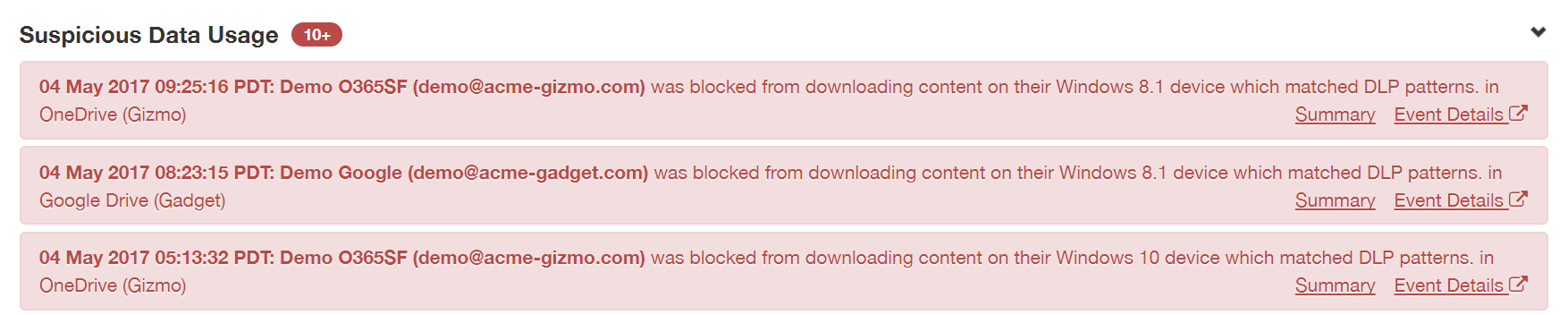
- Suspicious Data Usage: This category of alerts includes suspicious activities involving sensitive data. For example, if a user sends an email containing matched keywords to a
personal email account, if a file with sensitive data is accessed from several different locations in short succession, or if a Mobile DLP match occurs in user content.
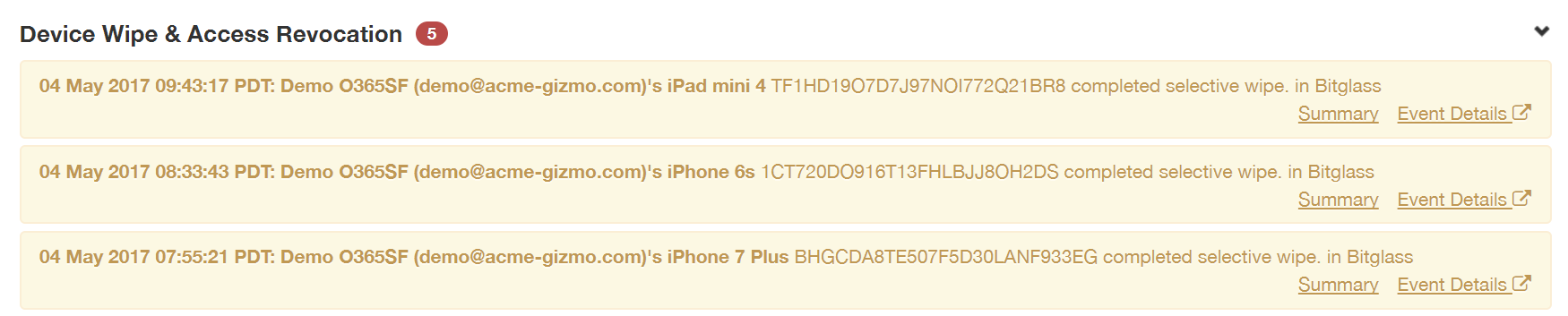
- Device Wipe & Access Revocation: These alerts indicate that a device has successfully been wiped or a user’s access to apps successfully revoked upon account deactivation.
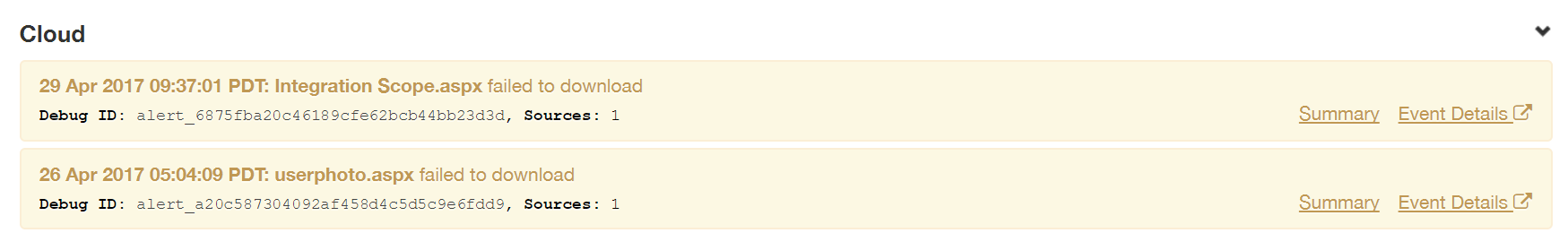
- Cloud: Shows alerts for actions/activity taking place with data-at-rest via API scans (actions such as quarantine, or API policy matches).
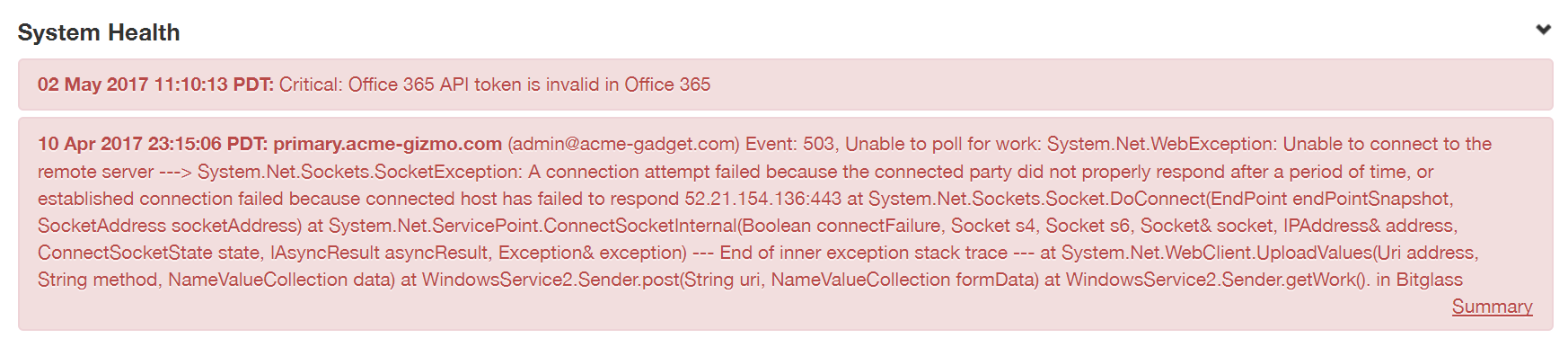
- System Health: These alerts are related to the Active Directory user synchronization agent as well as the SmartEdge Agent. The Active Directory Agent Event Codes can be used to
characterize the event type.