Deploying the protector
Protectors can be used in monitoring mode for data loss detection. When deployed in this manner, they do not interfere with network traffic, but they also cannot prevent (block) data loss—only note and report losses that occur.
For each data loss detection channel, the protector can be deployed to use the following modes:
| Service | Function |
|---|---|
| HTTP | Monitoring |
| SMTP |
Monitoring passive Mail Transfer Agent (MTA) |
| All Others | Monitoring |
| ICAP | Monitoring Blocking |
In monitoring mode, the protector is connected off the network via the SPAN/mirror port of a switch (or via a network TAP), as shown in the following diagram. This allows the protector to monitor and analyze traffic, but not block it.
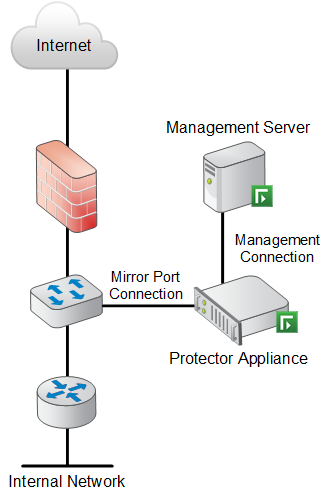
The protector must connect both to the SPAN/mirror port or TAP, and the Forcepoint DLP management server.