When does the system need to grow?
- Performance issuesPerformance issues may vary in visibility and impact.
- Slow discovery or fingerprinting scans, for example, could indicate an overworked crawler. This might be resolved by adding a crawler or Forcepoint DLP server.
- If users are experiencing slow web or email transactions, an additional policy engine might help.
Even if performance issues are not obvious, system resources may not be fully optimized.
To see how the Forcepoint DLP system is performing, open the Security Manager and go to the page. Expand each module to see load statistics, the number of transactions, latency information, and more.
Before adding modules, try balancing the load between existing Forcepoint DLP servers (policy engines). To do this, go to the page, then clickLoad Balancing. Select a service, then indicate which policy engine to assign to that service.Note: Forcepoint recommends that you do not distribute the load to the management server. - The number of users grows
A typical small organization (1–500 users) might only need a management server and a protector to monitor traffic. A larger organization (500–2,500 users) might have a management server, a supplemental Forcepoint DLP server, and a protector, with load balancing between the protector and supplemental server. (The management server cannot be used for load balancing.)
As the number of users grows, so does the need for additional Forcepoint DLP servers.
- The number of transactions grows
This is the most important requirement for determining the number of Forcepoint DLP components needed. Typically the number of transactions grows as the number of users grows.
In monitoring mode, Forcepoint recommends having 1 protector per 20,000 users. This calculation assumes:
- The protector is monitoring HTTP and SMTP
- There are 9 busy hours per day
- There are approximately 20 million transactions per day with a ratio of 15:1 HTTP:SMTP. (HTTP includes GETs and POSTs.)
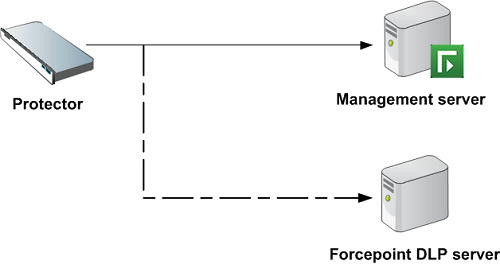
For more users, add an extra Forcepoint DLP server and balance the load between the protector and the extra server.
In blocking mode, Forcepoint recommends 1 management server, 1 V Series appliance with Forcepoint Email Security software, and 1 V Series appliance with Content Gateway software. This calculation assumes:
- There are 9 busy hours per day
- There are approximately 15 million transactions per day with a ratio of 15:1 HTTP:SMTP. (HTTP includes GETs and POSTs.)
For more users, add an extra Forcepoint DLP server.
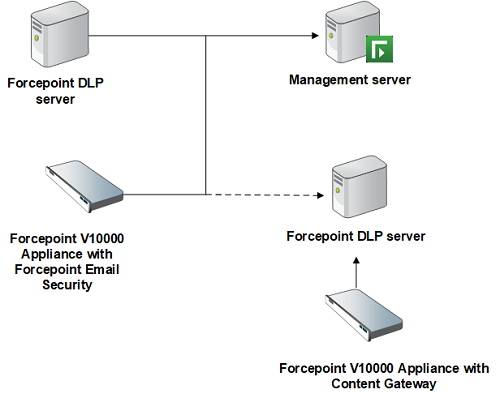
The transaction volume can grow even if the user base does not. If a significant increase in traffic is anticipated, the system may benefit from adding one or more Forcepoint DLP servers.
- The number of endpoints grows
With Forcepoint DLP Endpoint, when large numbers of endpoint clients are being deployed, additional endpoint servers may be required. A general rule of thumb is to add 1 Forcepoint DLP server for every 15,000 endpoint clients.
- Moving the deployment from monitor to protect
Enforcement requires more resources than monitoring, particularly because load- balancing must be enforced between policy engines and other Forcepoint DLP modules.
When a deployment is moving from monitor to protect, it may benefit from an additional Forcepoint DLP server. Note that the Forcepoint DLP Web Content Gateway is required to enforce the HTTP channel; the protector is required to enforce the SMTP channel.
- Moving from a single-site to multi-site configuration
Forcepoint DLP supports multi-site, distributed deployments. An organization can have a local policy engine on the protector, for example, and distributed (primary and secondary) fingerprint repositories. There can be a management server in one location and one or more supplemental Forcepoint DLP servers in other locations.
Administrators have the option to use the crawlers on the Forcepoint DLP servers alone to do fingerprint and discovery scans, or to install the crawler agent on additional servers to improve performance.
Many scalable options are available.
Organizations with multiple geographical locations need a protector for each site. A deployment with low latency between two geographically distributed sites might need two protectors and two supplemental Forcepoint DLP servers.
- Adding branch offices
Each branch office requires a protector. When a branch office is added or acquired, add a protector.
- Adding HTTP, SMTP and FTP egress points
If egress points are being added to the network structure, a protector is needed to monitor each egress point. Each one also needs a Web Content Gateway instance if HTTP protection is required.
- The network grows (in GB)
In deployments that use network discovery, the network size greatly affects sizing requirements, as does the frequency of full versus differential scans. Growing networks may require an additional crawler or Forcepoint DLP server.
- Repositories such as forensics, fingerprint, policy database are reaching their maximum capacity
The Forcepoint DLP software has default settings for the disk space requirements of its fingerprint and forensic repositories, but these values can be modified.
Organizations with larger transaction volumes and numbers of users can adjust values significantly upward.
At some point, however, it may be necessary to add another server to accommodate these repositories and increase available disk space. The forensics repository can get very large. It has a default setting of 40 GB. The archive has a default setting of 50 GB.