To test that traffic is going through the Secure SD-WAN Engine and that logs are being received, add a Linux host behind the Secure SD-WAN Engine.
Before you begin
Log on to the
Secure SD-WAN
Engine using SSH.
In this example, the following connections are used to test connectivity:
- An SSH connection to the Linux host that is protected by the Secure SD-WAN Engine
- A ping connection to a Google server.
Steps
-
Deploy a new AMI.
This example uses Amazon Linux as the operating system for the instance.
-
Select , then select an AMI that meets your needs.
-
Select the internal subnet, then define an IP address from that network for the eth0 network interface.
This example uses the 10.29.101.0/24 internal subnet. The IP address is 10.29.101.1.10.
-
Launch the instance.
-
In the Management Client component of the SMC, add rules to the Engine policy.
-
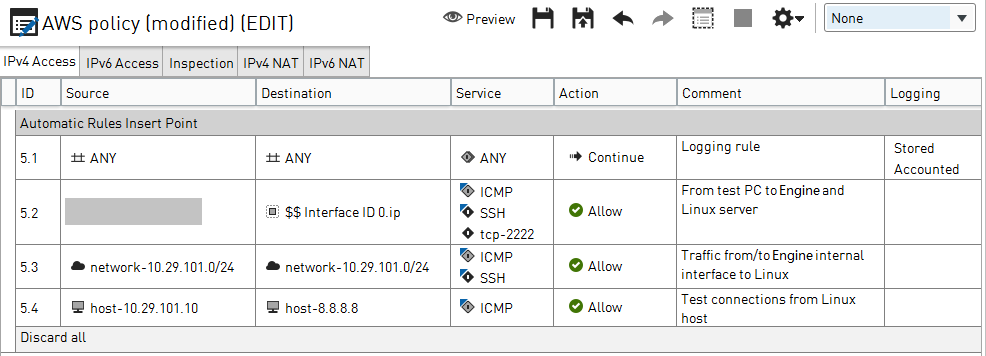
Add Access rules to allow the following traffic:
- SSH from your client computer to the Secure SD-WAN Engine and to the Linux host.
- ICMP and SSH from the Linux host to the Secure SD-WAN Engine, and from the Secure SD-WAN
Engine to the Linux host.
- Ping from the Linux host to the IP address of a Google server (8.8.8.8).
-
Add the following NAT rules:
- Destination translation for the public IP address of the Secure SD-WAN Engine on port 2222 to port 22 on the Linux host.
- Source translation for connections from the Linux host to the public IP address of the Secure SD-WAN Engine.

-
Install the policy.
After the policy has been successfully installed, the status of the Secure SD-WAN Engine is shown as green in the Home view of the
Management Client component of the SMC.
-
Test connectivity.
-
In a terminal program, make an SSH connection on TCP port 2222 to the public IP address of the Secure SD-WAN Engine.
-
Log on using the key pair exported from AWS.
The default user for Amazon Linux is ‘ec2-user’.
-
When logged in, ping 8.8.8.8.
-
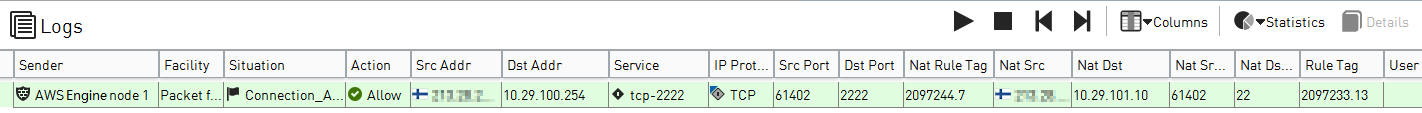
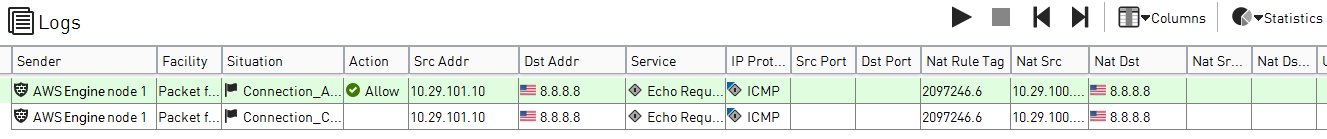
In the Management Client component of the SMC, open the Logs view, then check to see that the connection was allowed.
Result
The example deployment is now complete.
Example
- The NAT operation that translates the Elastic IP address of the Secure SD-WAN Engine to the internal IP address of the Secure SD-WAN Engine is applied on the Internet gateway before the packet reaches the Secure SD-WAN Engine. For
this reason, the public IP address of the Secure SD-WAN Engine is not shown in the logs.
- AWS reserves the .1 IP address for its router. The routing table on the Linux host shows that the next-hop subnet gateway is 10.29.101.1. However, the Secure SD-WAN Engine has been configured as the next-hop subnet gateway and its IP address is 10.29.101.254. AWS uses 10.29.101.1 as the default
gateway and applies internal NAT to 10.29.101.254. It is important to keep this internal NAT operation in mind, especially when troubleshooting.