Configure Forcepoint FlexEdge Secure SD-WAN settings in the SMC
Use the VPN Connection configuration that you downloaded from AWS to configure the remaining Secure SD-WAN Engine settings.
Steps
-
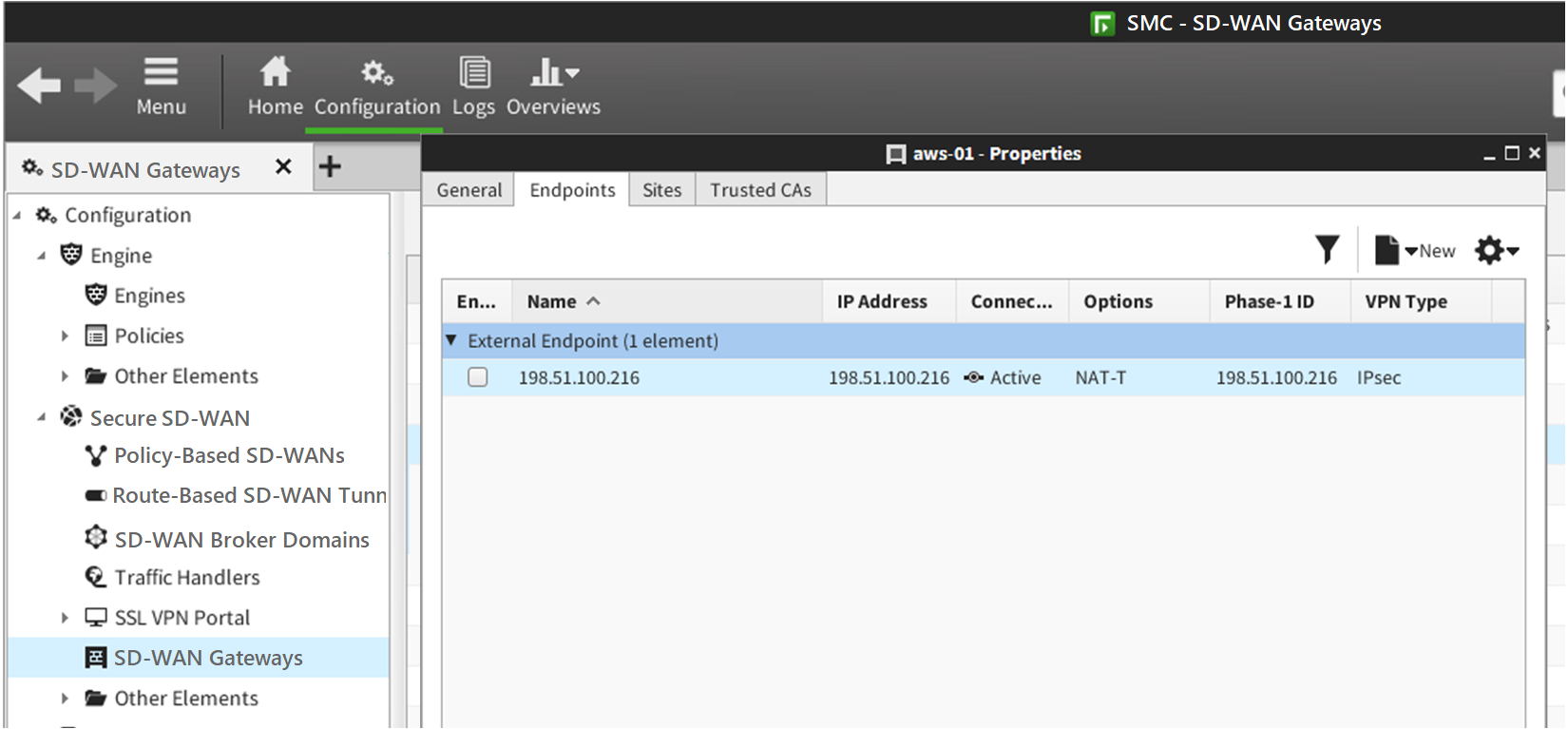
In the Management Client, create two External SD-WAN Gateway elements that represent the two AWS endpoints.
-
Select
 Configuration then browse to Secure SD-WAN > SD-WAN Gateways.
For older versions, select
Configuration then browse to Secure SD-WAN > SD-WAN Gateways.
For older versions, select Configuration then browse to VPN > Gateways.
Configuration then browse to VPN > Gateways. -
Right-click SD-WAN Gateways, then select New > External SD-WAN Gateway.
For older versions, right-click Gateways, then select New External VPN Gateway.
- On the Endpoints tab of each External SD-WAN Gateway element, add the IP address of the AWS endpoint.
-
On the Sites tab of each External SD-WAN Gateway element, configure each external gateway site to match the VPC network, then click
OK.
In this example, the VPC network is 172.31.0.0/16.
-
Select
-
Add a tunnel interface to the Secure SD-WAN Engine for each SD-WAN gateway, then add the IP address of the AWS endpoint to each tunnel
interface.
- Browse to Configuration > Engines > Engine.
- Right-click the Engine, then select Edit Single Engine.
- In the Engine Editor, browse to Interfaces.
- Add one tunnel interface for each SD-WAN gateway.
-
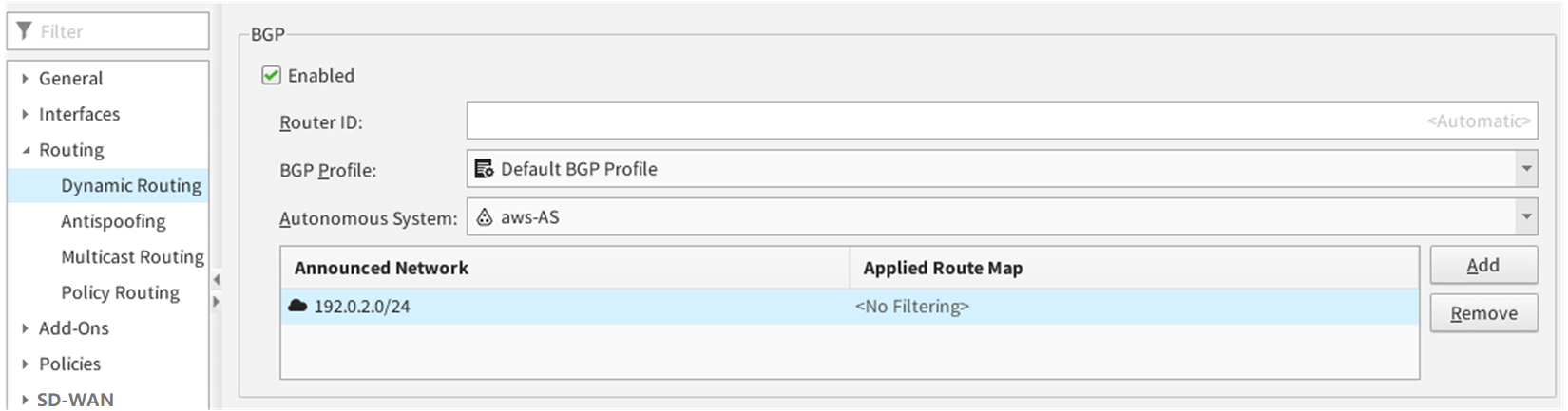
Enable BGP in the Engine properties.
- In the Engine Editor, browse to Routing > Dynamic Routing.
- In the BGP settings, select Enabled.
-
In the Autonomous System field, create an Autonomous System element that uses the AS number that AWS specified in the configuration.
The default is 65000.
- Add your protected network to the Announced Network configuration.
-
Edit the routing configuration for the Secure SD-WAN Engine.
- In the Engine Editor, browse to Routing.
- Under each tunnel interface, add a BGP Peering element.
- Right-click the BGP Peering element under each tunnel interface, then select Add External BGP Peer.
-
Select an AWS gateway for each tunnel interface.
For the Autonomous System (AS) field, create an Autonomous System element that uses the AS number provided by AWS.In this example, the AS number is 7224 for us-east.
-
Click
 Save.
Save.
-
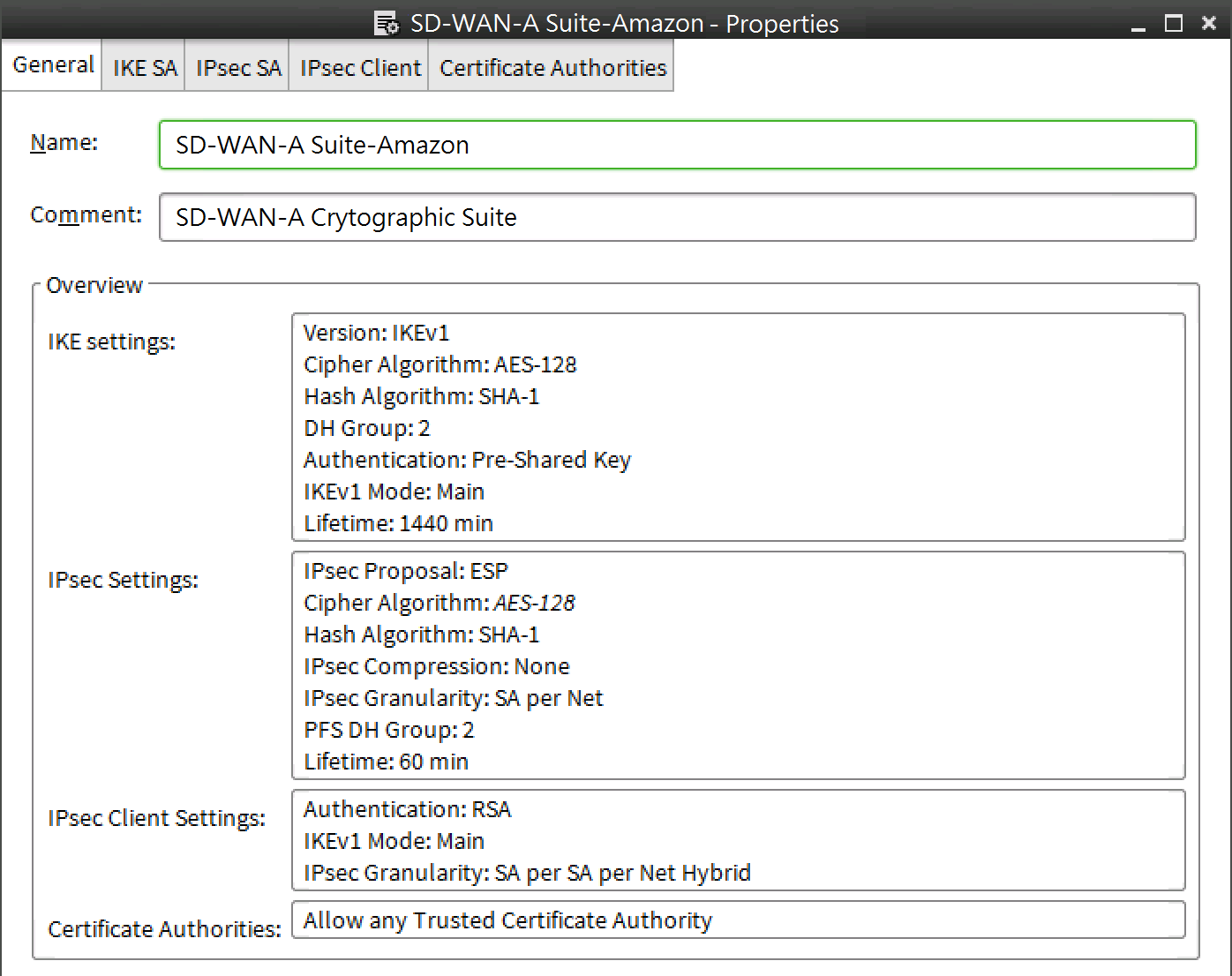
Create a SD-WAN Profile that matches the settings required by AWS.
-
Select
 Configuration then browse to Secure SD-WAN > Other Elements > Profiles > SD-WAN Profiles.
For older versions, select
Configuration then browse to Secure SD-WAN > Other Elements > Profiles > SD-WAN Profiles.
For older versions, select Configuration then browse to VPN > Other Elements > Profiles > VPN Profiles.
Configuration then browse to VPN > Other Elements > Profiles > VPN Profiles. - Right-click SD-WAN Profiles, then select New SD-WAN Profile
- Configure the settings to match the settings required by AWS, then click OK.
-
Select
-
Create route-based VPN tunnels for each AWS gateway.
-
Browse to Configuration > Secure SD-WAN > Route-Based SD-WAN Tunnels.
For older versions, browse to Configuration > VPN > Route-Based VPN Tunnels.
-
Right-click Route-Based SD-WAN Tunnels, then select New Route-Based SD-WAN Tunnel.
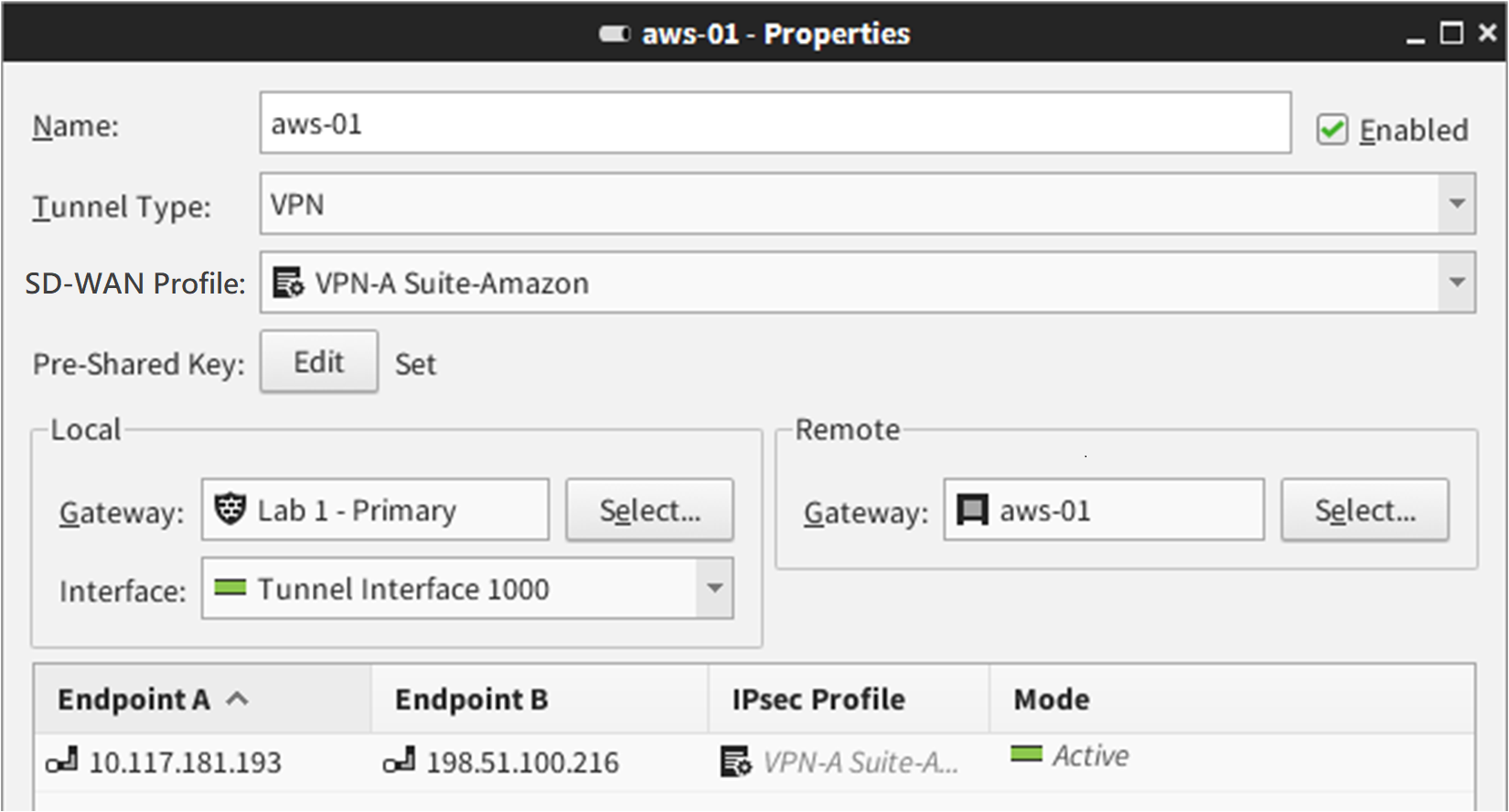
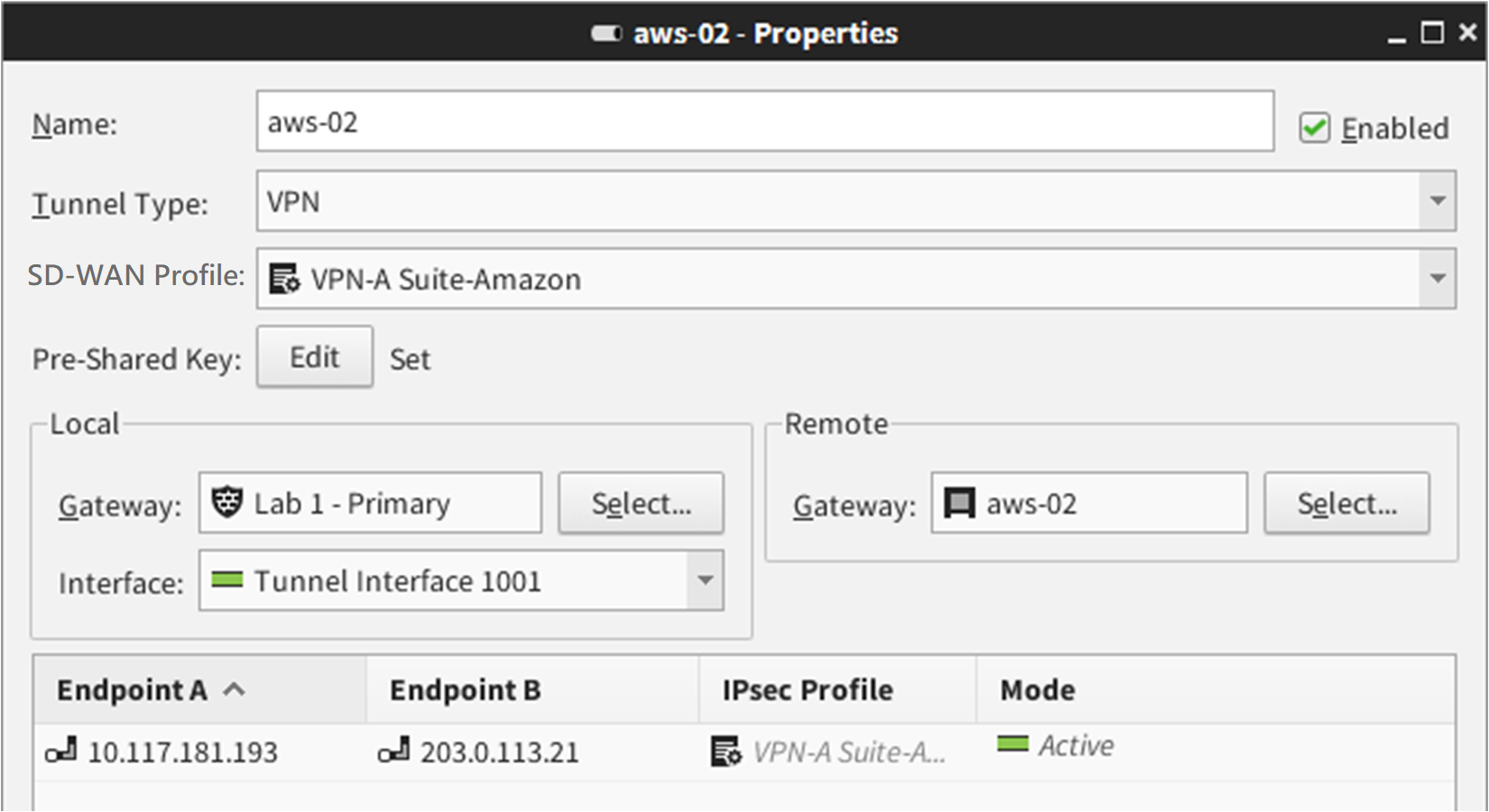
- For each tunnel, select the SD-WAN Profile element that you created.
- For each tunnel, enter the pre-shared key from the AWS VPN Connection configuration.
- In the Local settings, select the Secure SD-WAN Engine, then select a tunnel interface.
-
In the Remote settings, select an AWS gateway.
Make sure that you select the correct AWS gateway for each tunnel interface.
-
Browse to Configuration > Secure SD-WAN > Route-Based SD-WAN Tunnels.
-
Browse to Configuration > Policy > Engine Policy, then create a Engine Policy that allows traffic in both directions between the networks.
-
To verify that the IPsec tunnel is correctly established, right-click the Secure SD-WAN Engine, then select Monitoring > SD-WAN SAs.
-
To verify that BGP correctly propagates routes, select Dashboards > Engines, right-click the Engine, then select Monitoring > Routing.
-
In the AWS console, browse to the Tunnel Details tab, then verify that the tunnels are active.