Configuring Access rules
Access rules filter traffic by defining matching criteria and an action that is applied to packets that match all criteria defined in the rule.
- Engine Policy
- IPS Policy
- Layer 2 Engine Policy
- Layer 2 Interface Policy
- Template Policy
- Sub-Policy
Before starting to build policies, make sure that you understand the network element types available and how you can use them efficiently to define the resources that you want to protect and control.
Configuring Engine Access rules
Figure: Newly inserted Engine IPv4 Access Rule - Main cells
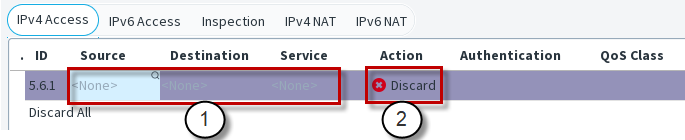
- 1
- Mandatory cells for matching traffic
- 2
- Engine applies this Action when it finds a match
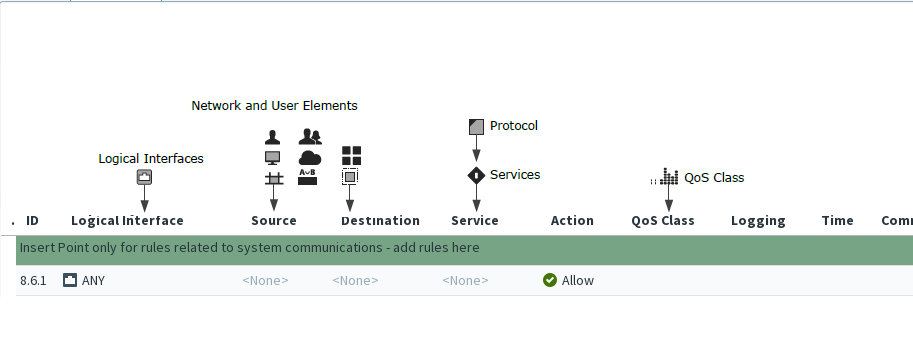
This illustration shows an Access rule that has been inserted into the policy. The matching cells are set to <None> and the action is set to Discard. These settings prevent the rule from having any affecting in case a new rule is added to the policy accidentally. It is not necessary to edit all cells in each rule. However, the mandatory cells for traffic matching (Source, Destination, and Protocol) must be set to some value other than <None> for the rule to be valid. The Source SD-WAN cell is also matched against traffic in the inspection process, but it can be left empty to match all traffic. The other editable cells specify further conditions and options, such as logging.
Figure: Elements in Engine Access rules
Configuring IPS and Layer 2 Engine Access rules
Figure: Newly inserted IPS or Layer 2 Engine Access Rule - Main cells
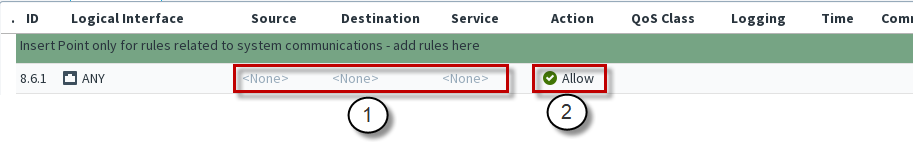
- 1
- Mandatory cells for matching traffic
- 2
- Engine applies this Action when it finds a match
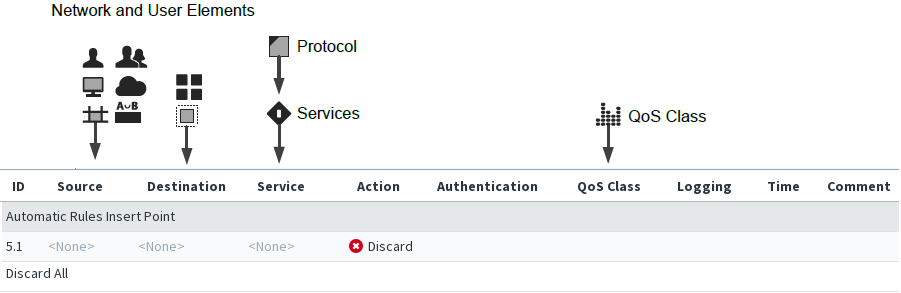
This illustration shows an Access rule that has been inserted into the policy. The matching cells are set to <None> to prevent the rule from affecting traffic in case a new rule is added to the policy accidentally. It is not necessary to edit all cells in each rule, but the mandatory cells for traffic matching (Source, Destination, and Service) must be set to some value other than <None> for the rule to be valid. The Logical Interface cell is also matched against traffic, but it is not mandatory to change its value if you want the rule to apply regardless of the interface. The other editable cells specify further conditions and options for handling connections that match the cells that are used for traffic matching.
The following illustration shows the types of elements that you can use in IPv4 and IPv6 Access rules.
Figure: Elements in IPS and Layer 2 Engine Access rules