URL filtering configuration overview
The URL filtering feature is configured using category-based URL filtering and custom URL List Applications.
Figure: Elements in the configuration
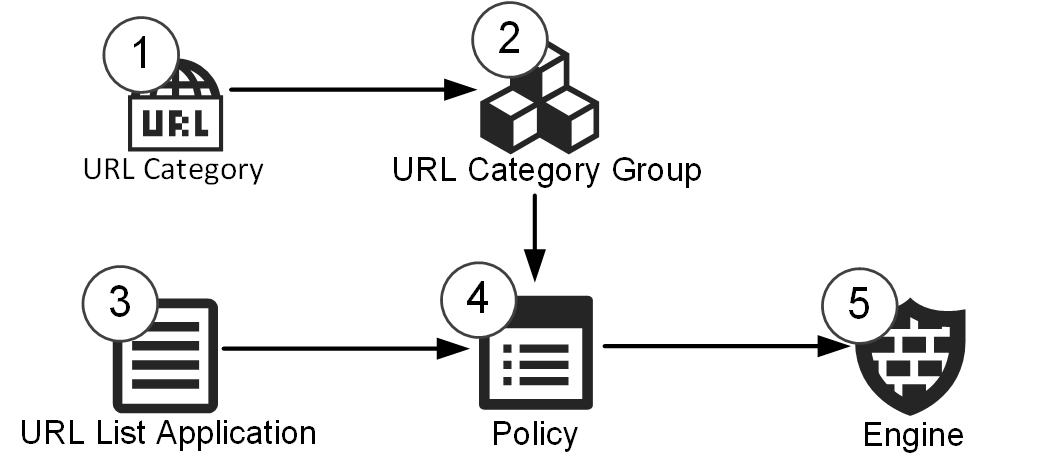
- 1
- The URL Category is referenced in the URL Category Group
- 2
- The URL Category Group is referenced in the Access rules in a policy
- 3
- The URL List Application is referenced in the Access rules in a policy
- 4
- The policy contains the Access rules that reference the URL elements.
- 5
- The policy is installed on the Secure SD-WAN Engine
The Access rules define how URL Categories and URL List Applications are matched to traffic and what reaction a match triggers. URL List Applications can override category-based URL filtering to allow some URLs manually.
Because an external service defines the URLs that are included in category-based URL filtering, it is not possible to add or edit categories. The category names for category-based URL filtering are updated through dynamic update packages.
- (Category-based URL filtering) Enable ThreatSeeker for the engine.
- (Category-based URL filtering) Make sure that the engine and the network are set up so that the engine can contact the ThreatSeeker Intelligence Cloud servers to request URL
categorizations.
- Make sure that DNS servers are defined for the engine in the General branch of the Engine Editor.
- Make sure that the engine can access the DNS server (UDP port 53, Service element "DNS (UDP)"). The connections are automatically allowed from the engine on which the policy is installed, but not from other components.
- (Optional) Configure an HTTP proxy for the connection to the ThreatSeeker Intelligence Cloud server in the branch of the Engine Editor.
- (Optional) Create User Responses to notify users about matches that are found.
- (Optional when using category-based URL filtering) Create URL List Applications to block or allow URLs manually.
- Add Access rules to define how URL filtering is applied.
- Create IPv4 or IPv6 Access rules to define how URL Categories are matched to traffic and what kind of reaction a match triggers.
- Create IPv4 or IPv6 Access rules to define how URL List Applications are matched to traffic and what kind of reaction a match triggers.
For example, you can add rules for URL List Applications to create exceptions to rules for category-based URL filtering.