The different parts of the policy editing view
The tabs and options shown in the policy editing view depend on the type of policy you are editing.
All policy editing views have by default the Resources pane on the left, the rule table on the right, and the policy toolbar at the top of the page. The available elements in the Resources pane can be used as matching criteria in different rule cells. There are tabs for the different rule types that are available for each type of policy.
Figure: Policy editing view (IPv4 Access tab)
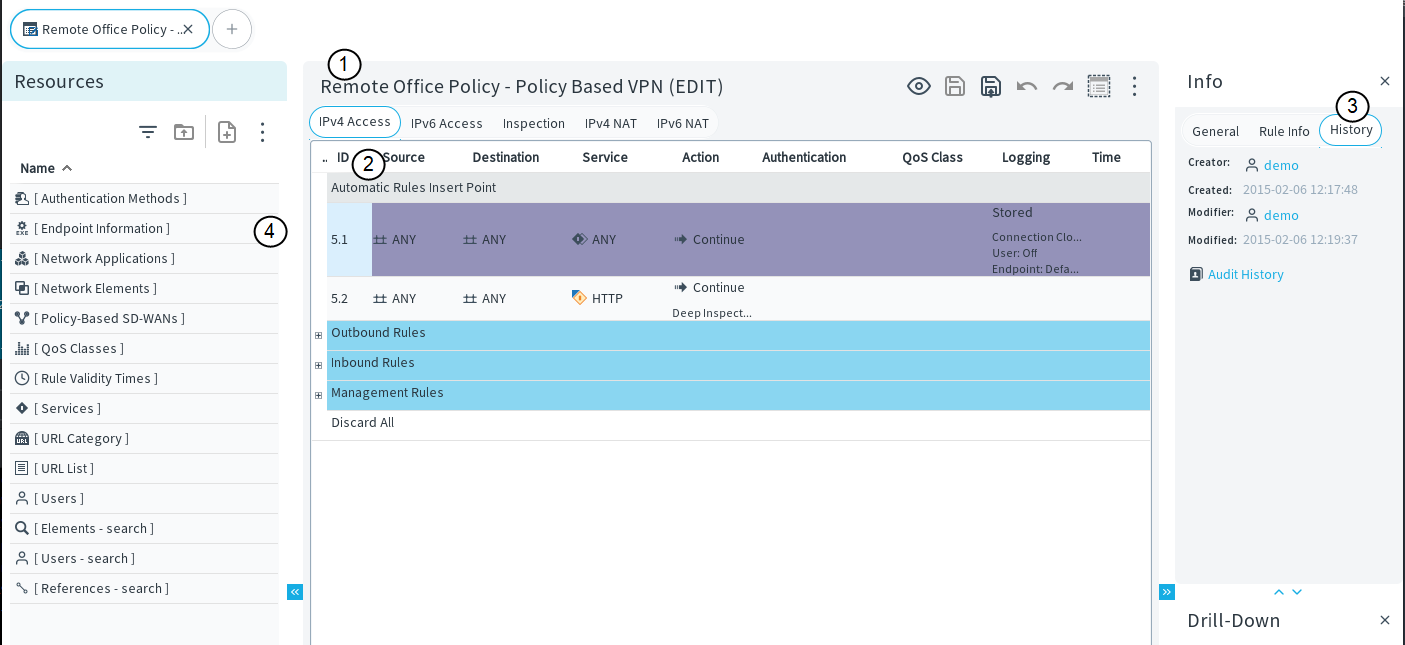
- 1
- Policy toolbar
- 2
- Rule table
- 3
- History for selected rule
- 4
- Search tool
In the Inspection Policy Editing view, there are only two tabs: Exceptions and Inspection. Global Inspection rules are configured on the Inspection tab, and exceptions to global Inspection rules on the Exceptions tab.
Figure: Inspection Policy Editing view
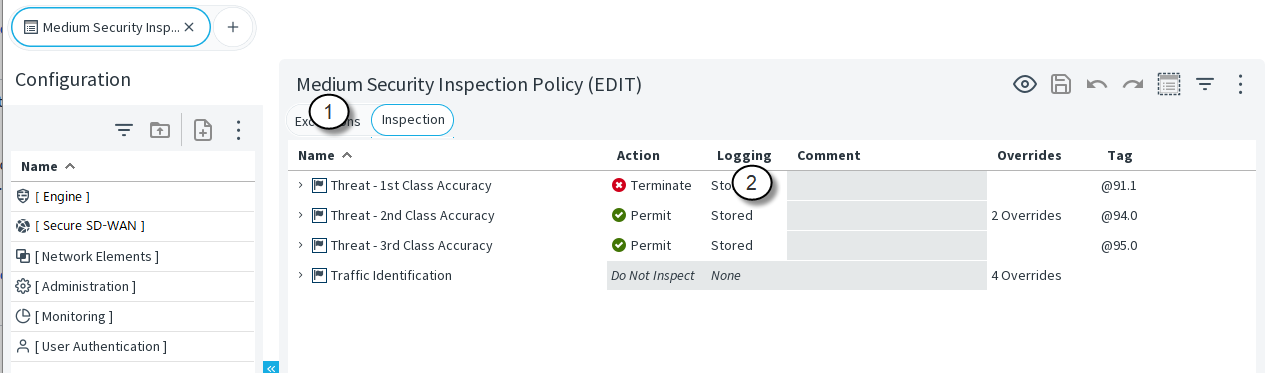
- 1
- Detailed Exceptions to the main Inspection rules
- 2
- The main rules tree
The policy toolbar contains tools for managing the policy.
Figure: Policy toolbar
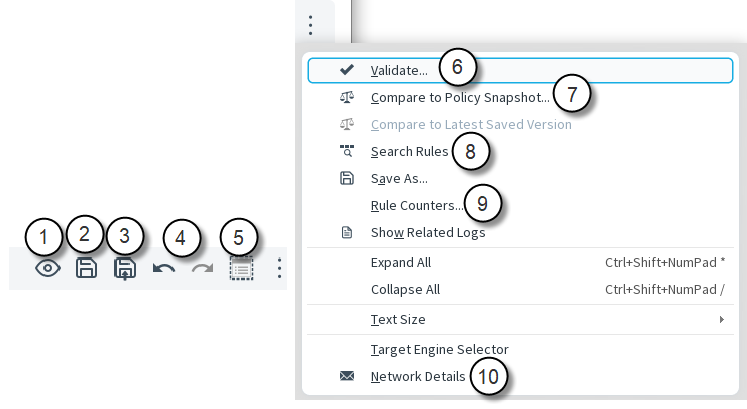
- 1
- Preview the policy in read-only mode
- 2
- Save
- 3
- Save changes and install policy on Secure SD-WAN Engines
- 4
- Undo or Redo
- 5
- Show Inherited rules passed down from higher-level templates
- 6
- Automatic validation finds rules that are clearly incorrect
- 7
- A Snapshot is made at each policy installation to allow change tracking
- 8
- Search tool for finding rules
- 9
- Display the number of hits for each rule
- 10
- Toggle between showing element names and IP addresses
Policy Editing view
Use this view to edit Engine, IPS, Layer 2 Engine, and Layer 2 Interface Policies.
| Option | Definition |
|---|---|
| Resources | Use this pane to create and add elements to a policy. |
| Filter | Opens a search field for the selected element list. |
| Up | Navigates up one level in the navigation hierarchy. Not available at the top level of the navigation hierarchy. |
| New | Opens the associated dialog box to create an element. |
| Tools |
|
| Option | Definition |
|---|---|
| Policy Toolbar | |
| Preview and Edit | Changes between the preview (read-only) and editing views. |
| Save | Saves the changes. |
| Save and Install | Saves the changes and installs the policy on the target Secure SD-WAN Engine. Note: This option is not available for Layer 2 Interface
Policies.
|
| Undo operation | Undoes the last change made. |
| Redo operation | Redoes the last change that was undone. |
| Inherited Rules | Shows inherited rules passed down from higher-level templates. |
| Aborts the running rule counters query | Cancels a rule counters query. This option is only available when a rule counters query is running. |
| Tools | |
| Validate | Validates the rules in the policy. Opens the Validate Policy dialog box in which you can select which issues are checked in the rules. |
| Compare to Policy Snapshot | Compares the policy with a previously created snapshot of the policy. |
| Search Rules | When selected, the Search Rules is available below the rules table. |
| Save As | Saves a copy of the policy as a new element. |
| Rule Counters | Displays the number of hits for each rule. |
| Expand All | If you have added Rule Sections or Sub-Policies, they are all expanded. |
| Collapse All | If you have added Rule Sections or Sub-Policies, and they are expanded, they are all collapsed. |
| Text Size | Changes the text size. |
| Target Engine Selector | Selects the target Engine for the Validate, Network Details, and Rule Counters actions. |
| Network Details | Toggles between element names and IP addresses. |
| Option | Definition |
|---|---|
| Ethernet tab (IPS, Layer 2 Engine, and Layer 2 Interface Policies only) | |
| ID (Not editable) |
Automatically assigned ID number that indicates the order of the rules in the policy. The rules are matched against traffic in the order of the ID numbers. |
| Logical Interface | For IPS engines, Layer 2 Engines, and Layer 2 Physical Interfaces on Engines, traffic matches the rule based on which interface the traffic is picked up from. The same logical interface can be assigned to one or several interfaces as configured in the properties of the Engine. This cell accepts only Logical Interface elements. |
| Source | Elements containing the MAC addresses that the rule matches. Both the Source and the Destination defined must match the source and destination of a packet for the packet to match the rule. The Source and Destination cells accept MAC Address elements. |
| Destination | Elements containing the MAC addresses that the rule matches. Both the Source and the Destination defined must match the source and destination of a packet for the packet to match the rule. The Source and Destination cells accept MAC Address elements. |
| Service | The Services match an Ethernet frame type. The Service cell accepts Ethernet Service elements. |
| Action | Command for the Engine to carry out when a connection matches the rule. |
| Logging | The options for logging. |
| Comment (Optional) |
A comment for your own reference. You can also add separate comment rows in between rules. |
| Rule Name | Contains a rule tag and optionally a rule name.
|
| Hits
(Not editable) |
Shows the number of connections that have matched the rule. This information is only shown if you have run a Rule Counter Analysis for the policy. The cell shows “N/A” if there is no information available about the rule. |
| Ethernet Insert Point (Before) and Ethernet Insert Point (After) | Marks the positions where rules can be added. |
| Option | Definition |
|---|---|
| IPv4 Access and IPv6 Access tabs | |
| ID (Not editable) |
Automatically assigned ID number that indicates the order of the rules in the policy. The rules are matched against traffic in the order of the ID numbers. |
| Logical Interface | For IPS engines, Layer 2 Engines, and Layer 2 Physical Interfaces on Engines, traffic matches the rule based on which interface the traffic is picked up from. The same logical interface can be assigned to one or several interfaces as configured in the properties of the Engine. This cell accepts only Logical Interface elements. |
| Source and Destination | A set of matching criteria that defines the IP addresses and interfaces that the rule matches. Both the Source and the Destination defined must match the source and destination of a packet for the packet to match the rule. The Source and Destination cells accept any elements in the Network Elements category, as well as User and User Group elements. |
| Service | A set of matching criteria that defines the service or application the rule matches. Services match a certain port, but they often also reference a Protocol for more advanced, application-layer inspection and traffic handling. The Service cell accepts Service and Service Group elements, URL Situations, Network Applications, and TLS matches. |
| Action | Command for the engine to carry out when a connection matches the rule. Also allows you to set options for file filtering (IPv4 only, not supported on Virtual Secure SD-WAN Engines), block listing, connection tracking, deep inspection, rate-based DoS protection, scan detection, user responses, and VPN connections (Engines Policy only). |
|
Authentication
(Engine Policy only) |
Defines whether the rule requires end users to authenticate, which end users the rule applies to when the rule requires authentication, and which authentication methods are valid for the rule. |
| QoS Class | The QoS Class that the Engine assigns to connections that match this rule. Used in traffic prioritization and bandwidth management. The QoS Class has effect only if you set up QoS Policies. |
| Logging | The options for logging. |
| Time |
Allows you to specify when the rule starts being enforced, when the rule automatically expires, and when the rule is active. By default, rules start being enforced when you install the policy, never expire automatically, and are always active. Drag and drop a Rule Validity Time element to the cell. |
| Comment (Optional) |
A comment for your own reference. You can also add separate comment rows in between rules. |
| Rule Name | Contains a rule tag and optionally a rule name.
|
| Source SD-WAN (Engine Policy only) |
Makes the rule match traffic based on whether it is coming from a specific VPN. If this cell is left empty, the rule matches both VPN and non-VPN traffic. |
| Hits
(Not editable) |
Shows the number of connections that have matched the rule. This information is only shown if you have run a Rule Counter Analysis for the policy. The cell shows “N/A” if there is no information available about the rule. |
| Automatic Rules Insert Point | Marks the position of automatic rules in the policy. |
| Insert Point | Marks the positions where rules can be added. |
| Option | Definition |
|---|---|
| Inspection tab (Not available in Layer 2 Interface Policies) | |
| Inspection Policy | Specifies the Inspection Policy. Click Select to select an element. |
| File Filtering Policy | Specifies the File Filtering policy. Click Select to select an element. |
| Option | Definition |
|---|---|
| IPv4 NAT and IPv6 NAT tabs (Engine Policy only) | |
| ID (Not editable) |
Automatically assigned ID number that indicates the order of the rules in the policy. The rules are matched against traffic in the order of the ID numbers. |
| Source and Destination | A set of matching criteria that defines the IP addresses and interfaces that the rule matches. Both the Source and the Destination defined must match the source and destination of a packet for the packet to match the rule. The Source and Destination cells accept any elements in the Network Elements category, as well as User and User Group elements. |
| Service | A set of matching criteria that defines the service or application the rule matches. Services match a certain port, but they often also reference a Protocol for more advanced, application-layer inspection and traffic handling. The Service cell accepts Service and Service Group elements, URL Situations, Network Applications, and TLS matches. |
| NAT | Specifies the translation type and options for the translation operation. |
| Used on | Specifies the Secure SD-WAN Engine to which the rule applies. |
| Comment (Optional) |
A comment for your own reference. You can also add separate comment rows in between rules. |
| Rule Name | Contains a rule tag and optionally a rule name.
|
| Hits
(Not editable) |
Shows the number of connections that have matched the rule. This information is only shown if you have run a Rule Counter Analysis for the policy. The cell shows “N/A” if there is no information available about the rule. |
| NAT Insert Point | Marks the positions where rules can be added. |
| Option | Definition |
|---|---|
| Search Rules pane | |
| Options |
|
| Next | Moves to the next search result. |
| Previous | Moves to the previous search result. |
| Clear | Clears the search fields. |
| Option | Definition |
|---|---|
| Info pane — Use this pane to view more information about the selected rule. | |
| General tab |
|
| Rule Info tab | Shows the matching criteria and options for the rule. |
| History tab |
|
| Option | Definition |
|---|---|
| Properties | Opens the Rule Properties dialog box. |
| Disable Rule and Enable Rule | If the rule is enabled, temporarily disables the rule without deleting. If the rule is disabled, enables the rule. |
| Lock Rule | Prevents edits until the rule is explicitly unlocked. |
Inspection Policy Editing view
Use this view to edit an Inspection Policy element.
| Option | Definition |
|---|---|
| Resources | Use this pane to create and add elements to a policy. |
| Filter | Opens a search field for the selected element list. |
| Up | Navigates up one level in the navigation hierarchy. Not available at the top level of the navigation hierarchy. |
| New | Opens the associated dialog box to create an element. |
| Tools |
|
| Option | Definition |
|---|---|
| Policy Toolbar | |
| Save | Saves the changes. |
| Undo operation | Undoes the last change made. |
| Redo operation | Redoes the last change that was undone. |
| Inherited Rules | Shows inherited rules passed down from higher-level templates. |
| Tools | |
| Validate | Validates the rules in the policy. Opens the Validate Policy dialog box in which you can select which issues are checked in the rules. |
| Compare to Policy Snapshot | Compares the policy with a previously created snapshot of the policy. |
| Search Rules | When selected, the Search Rules is available below the rules table. |
| Save As | Saves a copy of the policy as a new element. |
| Expand All | If you have added Rule Sections or Sub-Policies, they are all expanded. |
| Collapse All | If you have added Rule Sections or Sub-Policies, and they are expanded, they are all collapsed. |
| Text Size | Changes the text size. |
| Show Only Overrides | When selected, only rules that override the default settings are shown. |
| Target Engine Selector | Selects the target Engine for the Validate, Network Details, and Rule Counters actions. |
| Network Details | Toggles between element names and IP addresses. |
| Option | Definition |
|---|---|
| Exceptions tab | |
| ID (Not editable) |
Automatically assigned ID number that indicates the order of the rules in the policy. The rules are matched against traffic in the order of the ID numbers. |
| Situation | Defines the patterns of traffic that the rule matches. In addition to individual Situation elements, this cell can contain Situation Type and Situation Tag elements, which are shown as branches in the Situations tree and allow adding the whole branch of Situations at once to a rule. |
| Severity | Limits the rule to matching Situations that have a severity value within a range you define. This is most useful with rules that include Situation Tags in the Situation cell. |
|
Logical Interface
(IPS and Layer 2 Engine only) |
Traffic matches the rule based on which interface the traffic is picked up from. The same logical interface can be assigned to one or several interfaces as configured in the properties of the Engine. This cell accepts only Logical Interface elements. |
| Source and Destination | A set of matching criteria that defines the IP addresses and interfaces that the rule matches. Both the Source and the Destination defined must match the source and destination of a packet for the packet to match the rule. The Source and Destination cells accept any elements in the Network Elements category, as well as User and User Group elements. |
| Protocol | Limits the Protocols that the rule matches. The protocol is set for traffic in the Access rules in the Service cell of the rule that allows the traffic. |
| Action | Command for the engine to carry out when a connection matches the rule. The action-specific Action Options define settings for connection termination, and user responses. The Continue action can be used to set options for the Exceptions. |
| Logging | The options for logging. |
| Time |
Allows you to specify when the rule starts being enforced, when the rule automatically expires, and when the rule is active. By default, rules start being enforced when you install the policy, never expire automatically, and are always active. Drag and drop a Rule Validity Time element to the cell. |
| Comment (Optional) |
A comment for your own reference. You can also add separate comment rows in between rules. |
| Rule Name | Contains a rule tag and optionally a rule name.
|
| Option | Definition |
|---|---|
| Inspection tab | |
| Name | The name of the Situation or Situation Category. |
| Action | Command for the Engine to carry out when a connection matches the rule. |
| Logging | The options for logging. |
| Comment (Optional) |
A comment for your own reference. |
| Overrides | Shows the number of overrides to the default settings. |
|
Tag
(Not editable) |
Shows the rule tag. |
| Option | Definition |
|---|---|
| Info pane — Use this pane to view more information about the selected rule. | |
| General tab |
|
| Elements tab | Shows information about the elements that are of the selected Situation Type.
|
| History tab |
|
| Tags tab |
|
| Option | Definition |
|---|---|
| Properties | Opens the Properties dialog box for the selected element. |
| Where Used | Searches for references to the selected element. |