How Inspection Policy elements are designed
Inspection Policy elements activate checks for specific traffic patterns and define what action the engine takes when a match is found.
Engines, IPS engines, and Layer 2 Engines inspect traffic based on Situation elements, which contain the information about traffic patterns. Patterns can trigger immediate responses or be recorded. Detected events can be matched against Correlation Situations, which combine and further analyze the traffic-based findings to detect more threats and produce an easy-to-read event stream.
Inspection Policy elements are selected on the Inspection tab inside the Engine, IPS, and Layer 2 Engine Policy and Template Policy elements. Sub-Policies cannot contain Inspection Policy elements. You can add new rules to the Inspection Policy elements in the Policy Editing View and also in the Logs view based on log entries.
- The Inspection tab contains the main rules for finding traffic patterns. The Rules tree is applied to all traffic that is not handled as Exceptions.
- The Exceptions tab contains rules that match specific portions of the traffic based on Logical Interface, IP addresses, and Ports. Exceptions have some additional options, and can also set some of those options for the main Rules by using Continue rules.
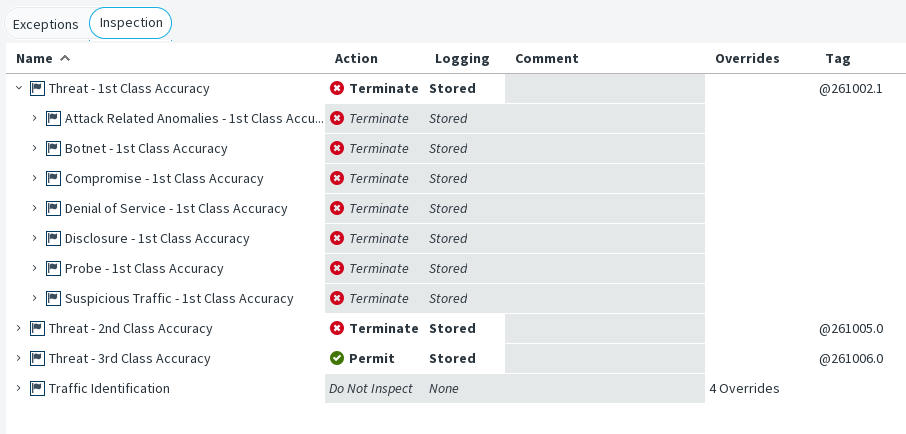
The main Rules tree on the Inspection tab contains a tree of Situations, which are organized under Situation Types. This tree allows you to control which inspection checks trigger a reaction and which checks are ignored. The Rules tree defines general checks that are applied to all patterns that are not handled by a more specific definition. It is not possible to limit the scope of the checks to certain IP addresses or Logical Interfaces in the Rules tree.
Figure: Inspection tab - Rules tree
The Exceptions are matched before the main rules. The most frequent use of Exceptions is to eliminate false positives. This typically requires permitting a pattern for some part of the traffic while the same pattern still triggers a reaction when it is encountered in any other traffic.
Figure: Exceptions tab
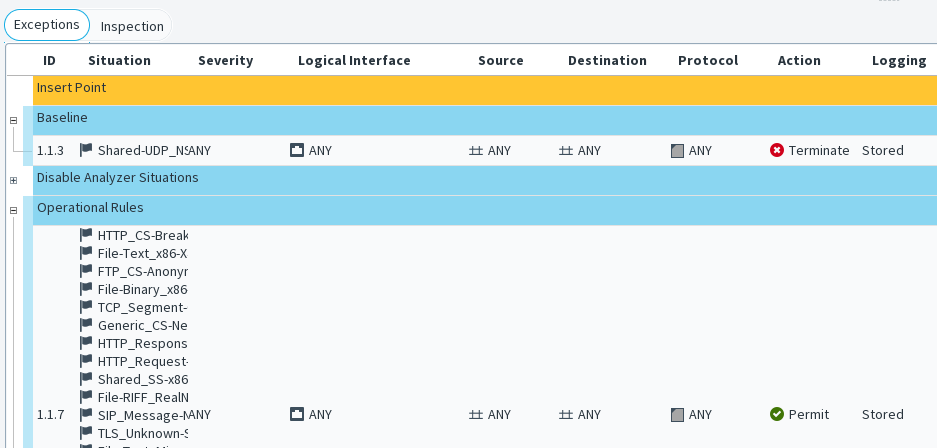
The main matching cell is the Situation cell, which contains the actual patterns. The other matching cells are Logical Interface, Source, Destination, Protocol, and Time. The role of the other matching cells is to limit the scope of the rule to some specific traffic. For example, the engine can take different action based on which host is the sender or receiver of traffic identified as malicious.