Configuration of Ethernet rules
You can use Ethernet rules in IPS, Layer 2 Engine, and Layer 2 Interface Policy and Template Policy elements. Sub-Policies cannot contain Ethernet rules.
Figure: Newly inserted Ethernet rule - Main cells
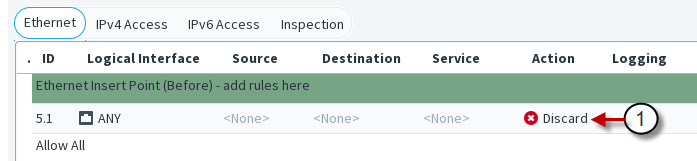
- 1
- Secure SD-WAN Engine applies action when it finds a match
This illustration shows an Ethernet rule that has been inserted into the policy. The Source, Destination, and Service cells are set to NONE, so this rule does not until they are changed to ANY or a more specific value. The Logical Interface cell is also matched against traffic, but it is not mandatory to change it if you want the rule to apply regardless of the interface. The other editable cells specify further conditions and options for handling matching connections. It is not necessary to edit all cells in each rule. Ethernet rules are read from the top down. More specific rules must be placed above more general rules that match the same traffic.
The illustration below shows the types of elements that you can use in Ethernet rules.
Figure: Elements in Ethernet rules
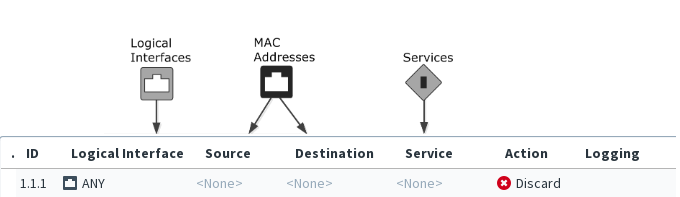
| Cell | Description |
|---|---|
| Logical Interface | Accepts Logical Interface elements. Traffic matches the rule based on which interface the traffic is picked up from. |
| Source |
Accept MAC address elements. You can set these cells to ANY to make the rule match all possible source or destination MAC addresses. You can also add more than one element in each cell to make the rule match multiple MAC addresses. The source and destination MAC addresses specified in an Ethernet rule are compared to the MAC addresses in each packet’s header. Based on these and other criteria, the rule is applied to matching packets. |
| Destination | |
| Service |
Accepts Ethernet Services elements. Defines which protocols the Ethernet rule applies to. You can set the Service to ANY to make the rule match all protocols. |
| Action |
Defines what happens when a packet matches the Ethernet rule. The following actions are available:
These actions stop the processing from continuing down the rule table for any packet that matches the rule. Rules with
these actions must be placed so that the more limited the rule is in scope, the higher up in the rule table it is. If
the traffic does not match any of the Ethernet rules by the end of the policy, the final action is applied.
Note:
When the Allow action is used for IPv4 or IPv6 traffic in the Ethernet rules, the traffic is then checked against
the IPv4 or the IPv6 Access rules. The final action for the IPv4 and IPv6 traffic is determined according to
traffic type by the IPv4 or the IPv6 Access rules.
|