Forcepoint FlexEdge Secure SD-WAN Engine ports
The most important default ports used in communications to and from Secure SD-WAN Engines and Master Engines are presented in the following illustrations.
See the table for a complete list of default ports for the engines.
Note: Master Engines use the same default ports as clustered Secure SD-WAN Engines. Virtual Engines do not communicate directly with other system components.
Figure: Destination ports for basic Secure SD-WAN Engine communications
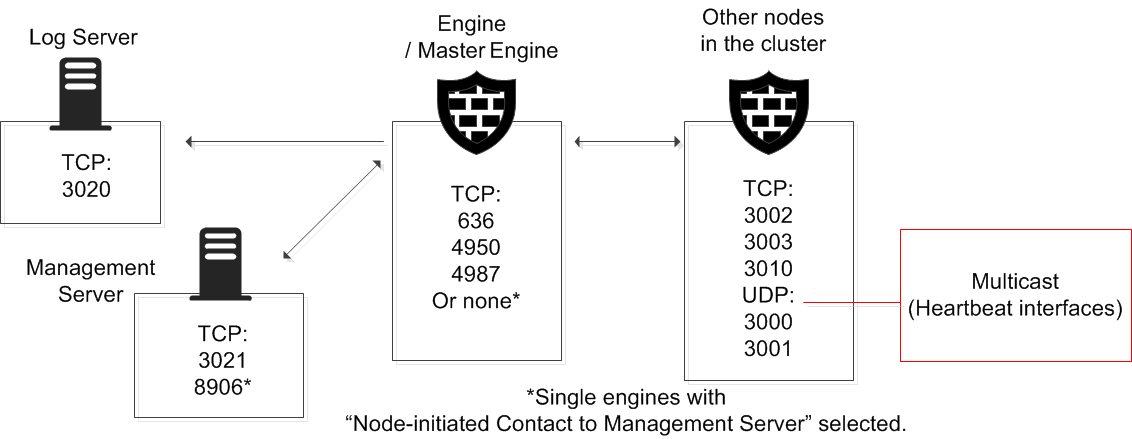
Figure: Default destination ports for Secure SD-WAN Engine service communications
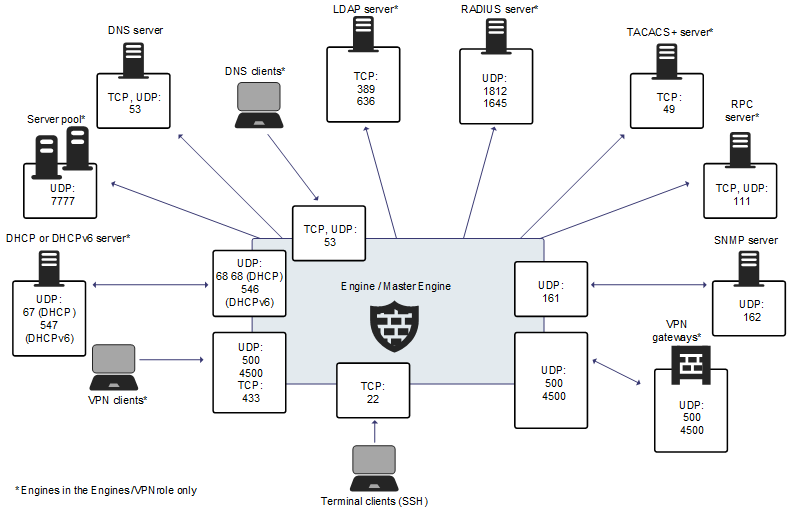
This table lists the default ports for Secure SD-WAN Engines and Master Engines. Many of these ports can be changed. The names of corresponding default Service elements are also included for your reference.
| Listening host | Port/protocol | Contacting hosts | Service description | Service element name |
|---|---|---|---|---|
| Certificate Revocation List (CRL) server | 80/TCP | Engine | Online certificate status protocol (OCSP) queries and fetching CRLs. | HTTP |
| DHCP server | 67/UDP | Engine | Relayed DHCP requests and requests from a engine that uses dynamic IP address. | BOOTPS (UDP) |
| DHCPv6 server | 547/UDP | Engine | Requests from a engine that uses dynamic IPv6 address. | N/A |
| External DNS server | 53/UDP, 53/TCP | Engine, Master Engine | DNS resolution and dynamic DNS updates. | DNS (TCP), DNS (UDP) |
| File reputation server | 443/TCP | Engine, Layer 2 Engine, IPS, Master Engine | GTI File Reputation Server | HTTPS |
| Engine | 67/UDP | Any | DHCP relay on engine. | BOOTPS (UDP) |
| Engine | 68/UDP | DHCP server | Replies to DHCP requests. | BOOTPC (UDP) |
| Engine | 80/TCP | Clients that need to authenticate to the Engine | Browser Based User Authentication | HTTP |
| Engine | 443/TCP | Clients that need to authenticate to the Engine | Browser Based User Authentication | HTTPS |
| Engine | 443/TCP | VPN clients using SSL tunneling | VPN client SSL tunneling | TLS |
| Engine | 443/TCP | SSL Portal users | SSL VPN Portal | HTTPS |
| Engine | 546/UDP | DHCPv6 server | Replies to DHCPv6 requests. | N/A |
| Engine, Master Engine | 53/UDP, 53/TCP | Clients in the internal network | DNS relay | DNS (TCP), DNS (UDP) |
| Engine, Master Engine | 500/UDP | VPN clients, VPN gateways | VPN negotiations, VPN traffic. | ISAKMP (UDP) |
| Engine, Master Engine | 636/TCP | Management Server | Internal user database replication. | LDAPS (TCP) |
| Engine, Master Engine | 4500/UDP | VPN client, VPN gateways | VPN traffic using NAT-traversal. | NAT-T |
| Engine Cluster Node, Master Engine cluster node | 3000-3001/UDP, 3002–3003, 3010/TCP | Engine Cluster Node, Master Engine cluster node | Heartbeat and state synchronization between clustered Engines. | SG State Sync (Multicast), SG State Sync (Unicast), SG Data Sync |
| Engine, Layer 2 Engine, IPS, Master Engine | 22/TCP | Terminal clients | SSH connections to the engine command line. Note: Do not use SSH in FIPS mode.
|
SSH |
| Engine, Layer 2 Engine, IPS, Master Engine | 4950/TCP | Management Server | Remote upgrade. | SG Remote Upgrade |
| Engine, Layer 2 Engine, IPS, Master Engine | 4987/TCP | Management Server | Management Server commands and policy upload. | SG Commands |
| Engine, Layer 2 Engine, IPS, Master Engine | 15000/TCP | Management Server, Log Server | block list entries. | SG block listing |
| Engine, Layer 2 Engine, IPS, Master Engine | 161/UDP | SNMP server | SNMP monitoring. | SNMP (UDP) |
| Engine, Layer 2 Engine, IPS | 9111/TCP | Forcepoint One Endpoint client | Endpoint information from the Forcepoint One Endpoint client. | N/A |
| Forcepoint User ID Service server | 5000/TCP | Engine, Layer 2 Engine, IPS | Information about user name and IP address mappings. | N/A |
| IPS Cluster Node | 3000-3001/UDP, 3002–3003, 3010/TCP | IPS Cluster Node | Heartbeat and state synchronization between clustered IPS engines. | SG State Sync (Multicast), SG State Sync (Unicast), SG Data Sync |
| LDAP server | 389/TCP | Engine, Master Engine | External LDAP queries, including StartTLS connections. | LDAP (TCP) |
| Layer 2 Engine Cluster Node | 3000-3001/UDP, 3002–3003, 3010/TCP | Layer 2 Engine Cluster Node | Heartbeat and state synchronization between clustered Layer 2 Engines. | SG State Sync (Multicast), SG State Sync (Unicast), SG Data Sync |
| Log Server | 3020/TCP | Engine, Layer 2 Engine, IPS, Master Engine | Log and alert messages; monitoring of block lists, connections, status, and statistics. | SG Log |
| Malware signature server | 80/TCP | Engine, Layer 2 Engine, IPS, Master Engine | Malware signature update service. | HTTP |
| Management Server | 3021/TCP | Engine, Layer 2 Engine, IPS, Master Engine | System communications certificate request/renewal (initial contact). | SG Initial Contact |
| Management Server | 8906/TCP | Engine, Layer 2 Engine, IPS | Management connection for engines with "Node-Initiated Contact to Management Server" selected. | SG Dynamic Control |
| RADIUS server | 1812, 1645/UDP | Engine, Master Engine | RADIUS authentication requests. | RADIUS (Authentication), RADIUS (Old) |
| RPC server | 111/UDP, 111/TCP | Engine, Master Engine | RPC number resolve. | SUNRPC (UDP), Sun RPC (TCP) |
| Server Pool Monitoring Agents | 7777/UDP | Engine, Master Engine | Polls to the servers' Server Pool Monitoring Agents for availability and load information. | SG Server Pool Monitoring |
| SNMP server | 162/UDP | Engine, Layer 2 Engine, IPS, Master Engine | SNMP traps from the engine. | SNMP Trap (UDP) |
| TACACS+ server | 49/TCP | Engine, Master Engine | TACACS+ authentication requests. | TACACS (TCP) |
| ThreatSeeker Intelligence Cloud server | 443/TCP | Engine, Layer 2 Engine, IPS, Master Engine | ThreatSeeker Intelligence Cloud URL categorization service. | HTTPS |
| VPN gateways | 500, 4500/UDP | Engine, Master Engine | VPN traffic. Ports 443/TCP (or custom port) can also be used, depending on encapsulation options. | ISAKMP (UDP) |