How sub-policies work
Sub-Policies are sections of Access rules that you can insert in the IPv4 or IPv6 Access rules of Policies, Template Policies, or other Sub-Policies.
Sub-Policies can also be used to organize the policies and to delegate administrator rights. You can restrict specific administrators to edit, add, or delete rules within a limited section of IPv4 or IPv6 Access rules, which is more restrictive than giving access to a template or policy.
A Sub-Policy is inserted into some other policy element by adding a Jump rule to the policy element. The Jump rule directs connections that match the Jump rule for matching against the rules in the Sub-Policy.
Figure: A collapsed Sub-Policy
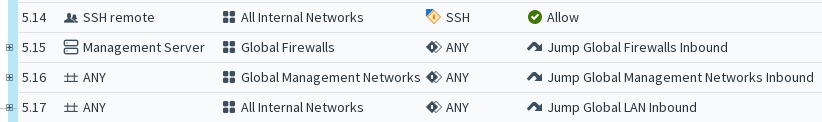
Figure: An expanded Sub-Policy
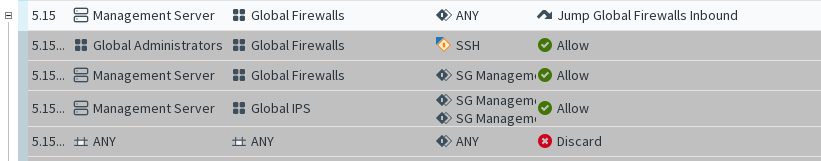
The illustrations show the same Jump rule in a policy in the collapsed and the expanded state. The rules of the Sub-Policy are shown on a gray background, because they can be edited only within the Sub-Policy itself, not in the Engine Policy that uses the rules.
You could use a Sub-Policy, for example, for examining traffic destined to a group of servers located in one particular network. The Jump rule could then use the destination network as a criteria for directing connections for matching against the Sub-Policy. Any connection that was destined to some other network would not get matched against any of the rules in the Engine Sub-Policy. This makes the matching process faster, because the engine can skip a whole Sub-Policy by comparing a connection to just one simple rule for any non-matching connection. If the Sub-Policy rules were inserted directly into the main Engine Policy, the engine would have to compare all connections to all those rules individually (because that is the only way to find out whether the connection matches the rules). The performance benefit gained depends on the number and complexity of the rules that can be placed in a Sub-Policy. It also depends on how heavy the engine load is to begin with.
The main goal of Sub-Policies is to match only part of the traffic against the rules in the Sub-Policy and allow other traffic to bypass the Sub-Policy. Rules in a Sub-Policy should have at least some identical matching criteria (source, destination, service, source SD-WAN, or user authentication details). These criteria can be used to select only a portion of the traffic for the sub-policy checks.
There are two ways to create Sub-Policies: you can either create a Sub-Policy and add Access Rules to it manually or select Access rules in a policy and convert them into a Sub-Policy.