Example: configuring NAT with hosts in the same network
An example of configuring NAT to route traffic between hosts in the same network through the engine.
Company B has two servers running in the same DMZ network. The servers keep contact with each other to exchange some information. The administrators want to route the traffic through the engine so that it is logged for reporting purposes instead of letting the servers communicate with each other directly.
Figure: Company B’s network setup
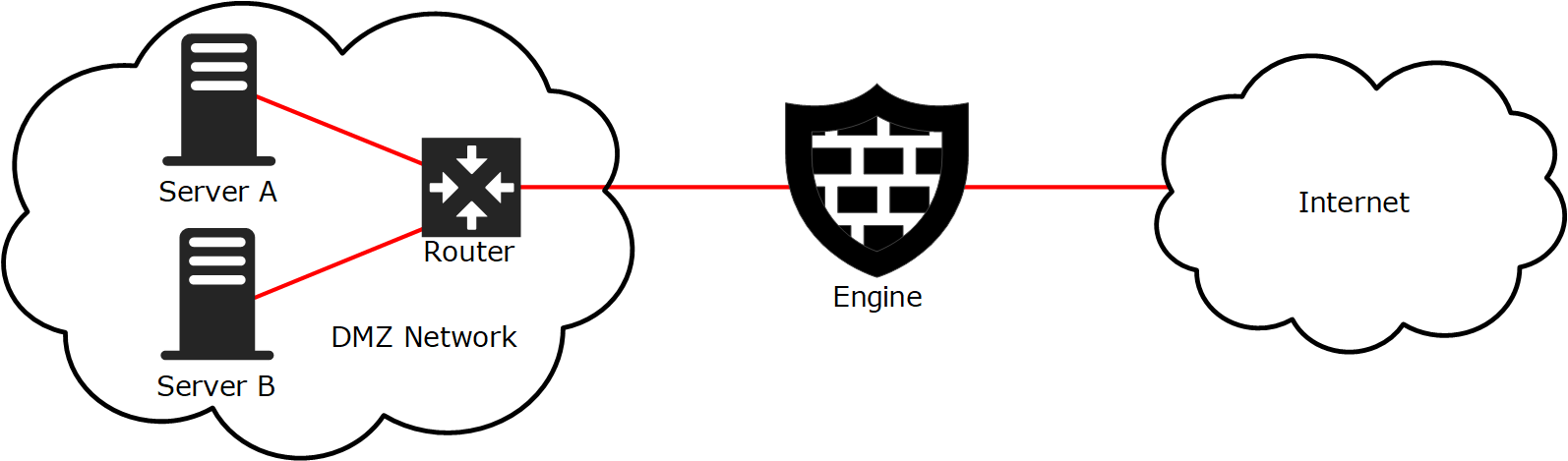
The administrators first intend to just configure the servers to use the external (NAT) address of the other server as a destination and configure the related static destination NAT rule. However, they soon realize that the receiver would see the real source address in the communications and the replies would be sent directly, bypassing the engine for the reply communications. This action would obviously prevent the connections. A static source NAT is required in addition to the static destination NAT.
- Create Host elements to represent the private addresses of the two servers.
- Create Host elements to represent the public addresses of the two servers.
- Add two new NAT rules before any other NAT rule that would match these connections:
Table 1. Static translation rules for opening connections both ways Source Destination Service NAT “Server A Private” Host “Server B Public” Host ANY Source: Static from Server A Private to Server A Public
Destination: Static from Server B Public to Server B private.
“Server B Private” Host “Server A Public” Host ANY Source: Static from Server B Private to Server B Public
Destination: Static from Server A Public to Server A private.
- When the servers are configured to contact each other using the public IP addresses, the communications are routed through the engine.
- The Engine translates the destination to the other server’s private IP address and the private IP address of the source to the public IP address to “hide” the private source address from the receiving host. This way, the replies are sent to the public IP address and routed correctly through the engine.