Creating an agent-based ZTNA policy
Once Agent-based application is configured and saved, a default policy gets created under Policies page.
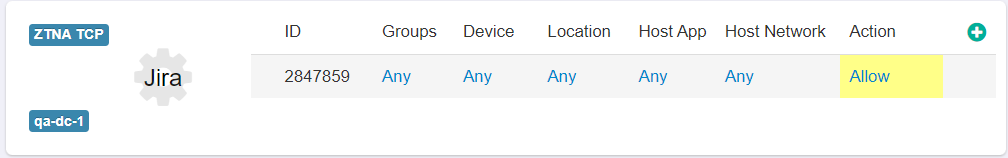
In the above image, you can see a standard policy table allowing you to configure a number of variables and apply an exception action to prevent Forcepoint Data Security Cloud | SSE from proxying traffic.
- Group: Locally defined groups or security groups and OUs pulled from active directory. You can add as many groups as are needed for the policy. You can also negate the group so that
policy line applies to everyone except the group you selected.
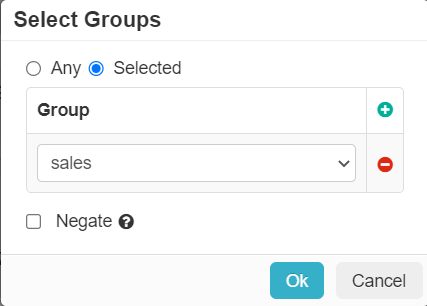
- Device: Set contextual access controls based on the users device (OS/user agent, managed vs unmanaged, etc).
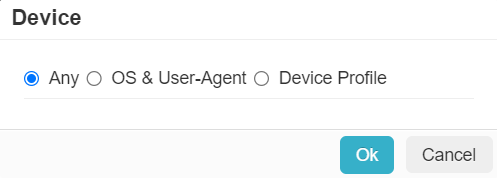
- OS & User-Agent: Allows you to match from a predefined set of common operating systems and/or User-Agent Strings
- Device Profile: Allows you to match on Device Profiles which are managed under .
- Location: This column allows you to restrict or control where a user is accessing the application from (either geographic location or IP).
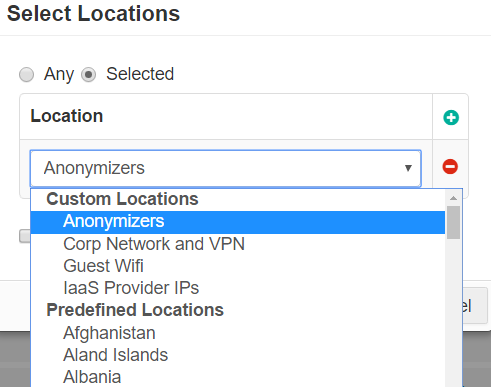
- Predefined locations include a list of countries. Country match is done using a geo-IP lookup to match source IP address to country.
- Custom Locations can be configured under . To configure a custom region, enter an IP address, subnet, or IP ranges on individual lines. Remember to use external internet facing addresses (example, 67.228.234.100/30). Custom locations also include predefined locations that are not based on countries (example, Anonymizers and IaaS Provider IPs). These locations are managed and updated by Forcepoint Data Security Cloud | SSE.
- Host App: Unique contextual variable to connection policies, can select the specific host app that is allowed the bypass (that is, selecting a specific web browser or chat app). To know more about Host App, refer to Host App.
- Host Network: This column can be configured to identify when users are on the corporate network to allow the bypass. To know more about Host Network, refer to Host Network.
- Action: This column indicates the actions to be taken when policy is met. You can choose one of the following actions:
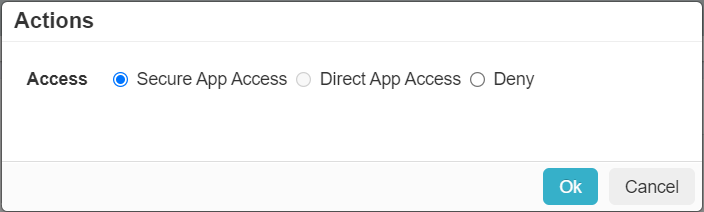
- Secure App Access - Connects users to the ZTNA application through Forcepoint Data Security Cloud | SSE cloud. This will also implicitly deny them the ability to access the ZTNA application directly.
- Direct App Access - After authentication, allows users to connect directly to the ZTNA application bypassing the Forcepoint Data Security Cloud | SSE cloud. To enable this access mode, you should set Host
Network to selected network and should not be Any.
To access the ZTNA application directly, the user's machine should have SmartEdge Agent 1.7.0 or newer version installed and the OS should be Windows 10 or newer version. Older versions of the SmartEdge agent will deny access when evaluating a policy rule with Action set to Direct App Access since they are unable to interpret it.
Note: If the Host Network is configured and if admin changes it back to Any, then the Action will be automatically changed to Secure App Access. - Deny - Allows you to block users from using the ZTNA application based on a rules match criteria.