Forcepoint Data Security Cloud | SSE supports OAuth 2.0 for REST API authentication. Admins can
setup a config API for user/group provisioning via a SCIM or Forcepoint Data Security Cloud | SSE API,
a log export API, or an IP API to pull Forcepoint Data Security Cloud | SSE IP addresses for firewall
or proxy configurations.
Steps
-
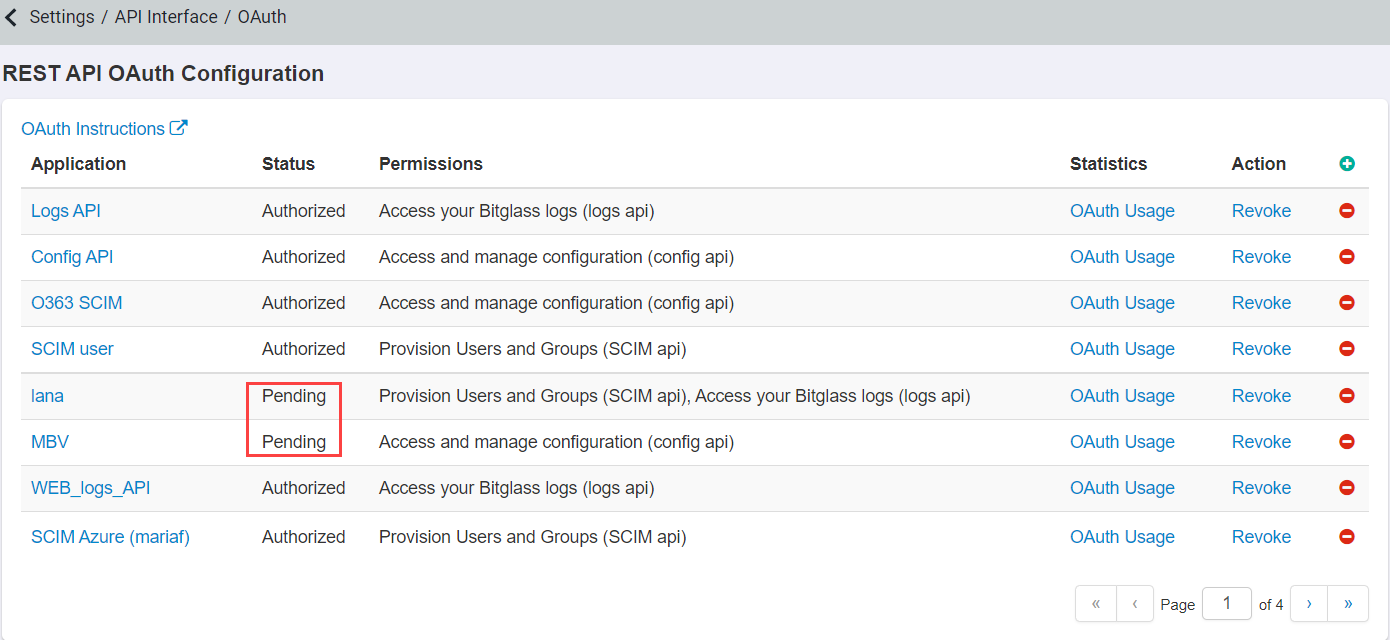
Navigate to .
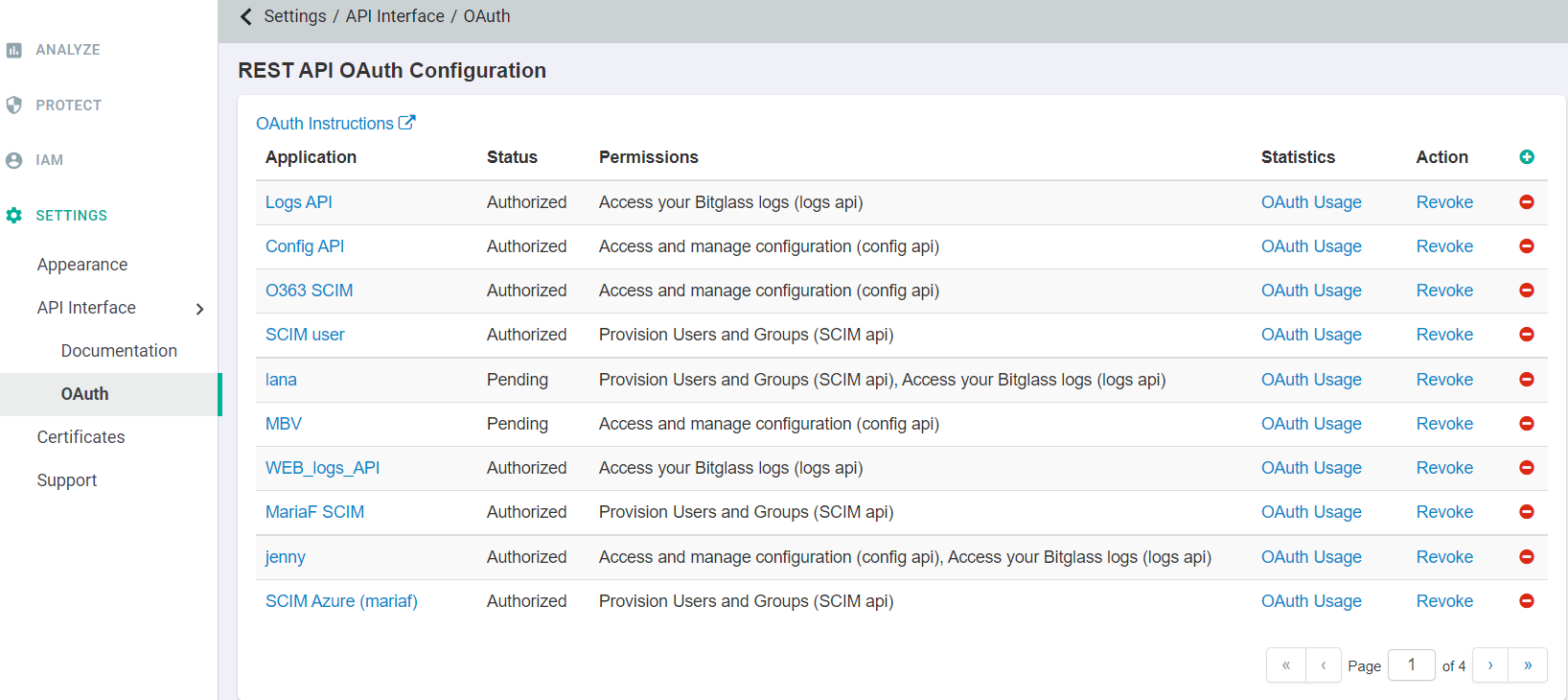
REST API OAuth Configuration page opens which allows you to add and configure different levels of API permissions.
-
To add a new configuration, click the green plus icon.
-
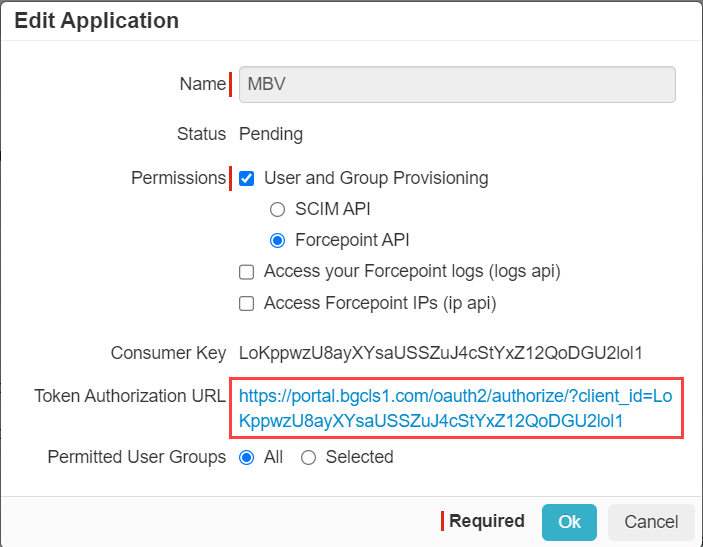
On the Edit Application dialog, fill out the information based on the permission levels you wish to grant.
-
Enter a Name for the new application configuration.
-
Select the type of Permissions you wish to grant (selecting just Config API, Log API, IP API).
- User and Group Provisioning: Will allow you to connect to Forcepoint Data Security Cloud | SSE to control user/group configuration via
SCIM or Forcepoint Data Security Cloud | SSE API.
- Log API: Will allow you to access and pull Forcepoint Data Security Cloud | SSE logs via API.
- IP API: Will allow you to pull Forcepoint Data Security Cloud | SSE's public IP addresses to ensure that your firewalls are configured properly to maintain outbound traffic flow to Forcepoint Data Security Cloud | SSE.
-
Select which users the permissions will apply to (All is default).
You can click Selected and then click the green plus icon to add a new line field and select a specific group you wish to grant the permissions to.
You can add as many groups as you wish.
-
Once you are done with the settings, click Ok to save the changes.
You will now see your application added to the list, but still listed as Pending under status.
-
Select the name of your application in the Application column to go into the Edit Applications.
-
On the Edit Applications dialog, you will need the Token Authorization URL to authorize your current Forcepoint Data Security Cloud | SSE account for the application you set up.
You can also copy the URL and send to the other users who will also be given the permission as well.
-
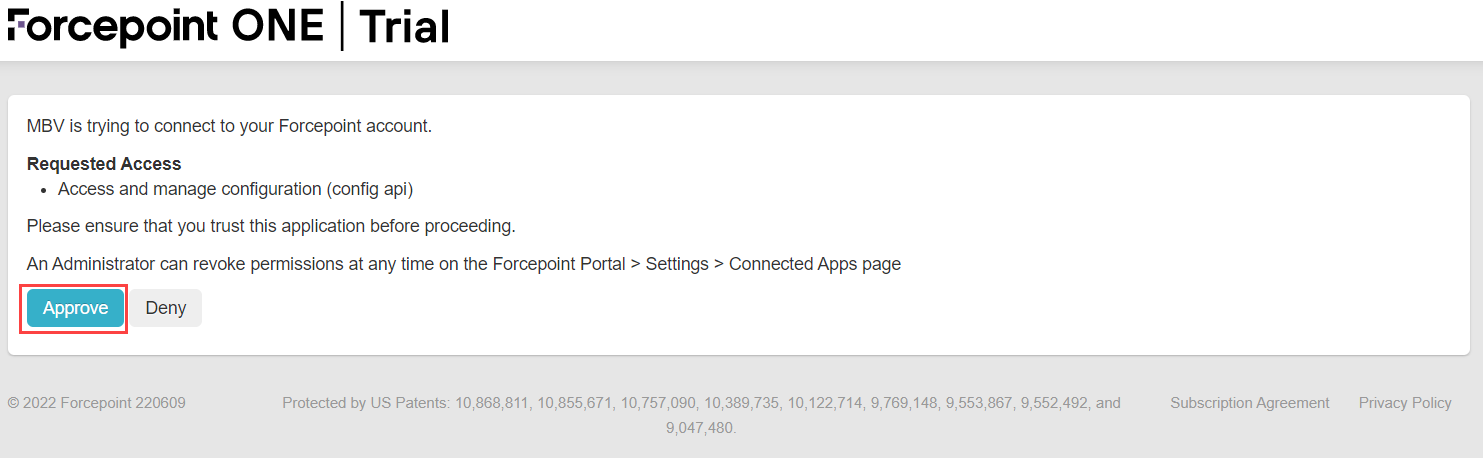
Selecting the URL will take you to the Requested Access page allowing you to Approve or Deny the
application permission settings. Again you will need to send this URL to each permitted user and have them Approve their access.
-
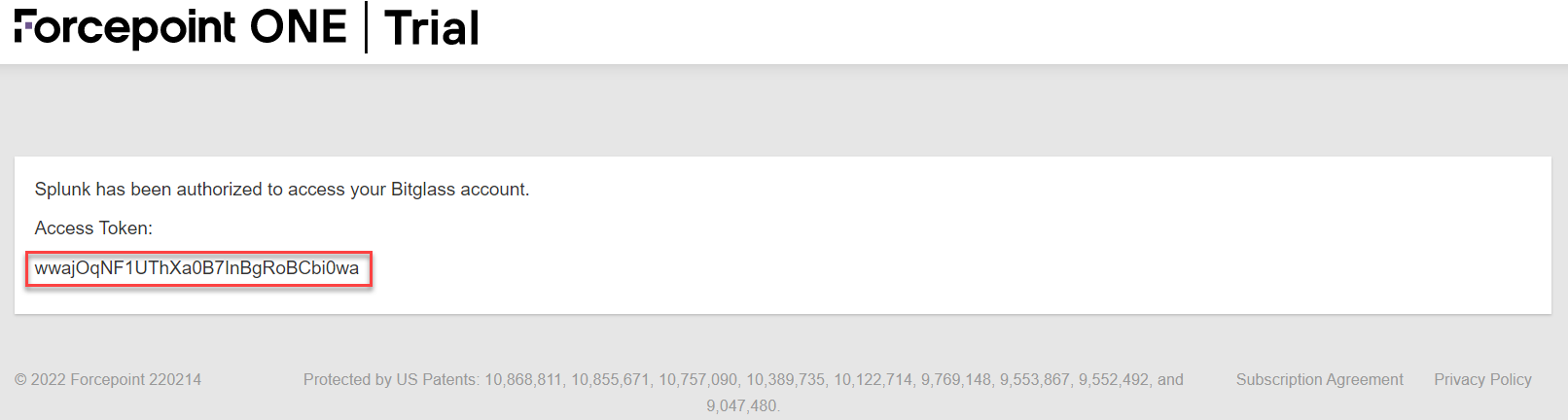
After you approve, you will be given an Access Token that is unique to that user and that the user must keep. The token is valid forever and must be
included in each request for authorization.
Note: If RBAC permissions change for the user, those
permission changes will carry over with the same token. The only time a new token will need to be generated is if scopes are added to the application.
Once access has
been approved, you will notice that Status is changed to Authorized.
-
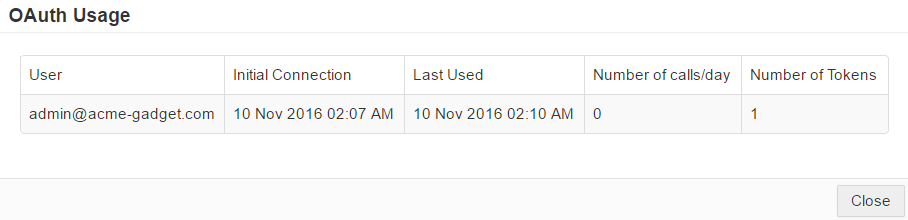
Once users begin to authorize the application, that information will be tracked and you can view it under the Statistics column by select OAuth
Usage for the particular application.
It will also identify their
Initial Connection (date and time in the admin's timezone),
Last Used (date and time in the admin's
timezone),
Number of calls/day, and
Number of Tokens.
-
If required, you can choose to revoke access to the application under the Action column.
Example
The primary difference between generating a request with basic Auth and OAuth is replacing
-u <username> <password> with
-H "Authorization: Bearer:
<your_token_here>".
curl -H "Authorization: Bearer TZGS5cnWjR2D0YHdfPmJwH2OZlrCFm" "https://portal.btglss.net/api/bitglassapi/logs?type=cloudsummary&responseformat=csv&startdate=2016-09-10T04:25:05Z&cv=1.1.5"