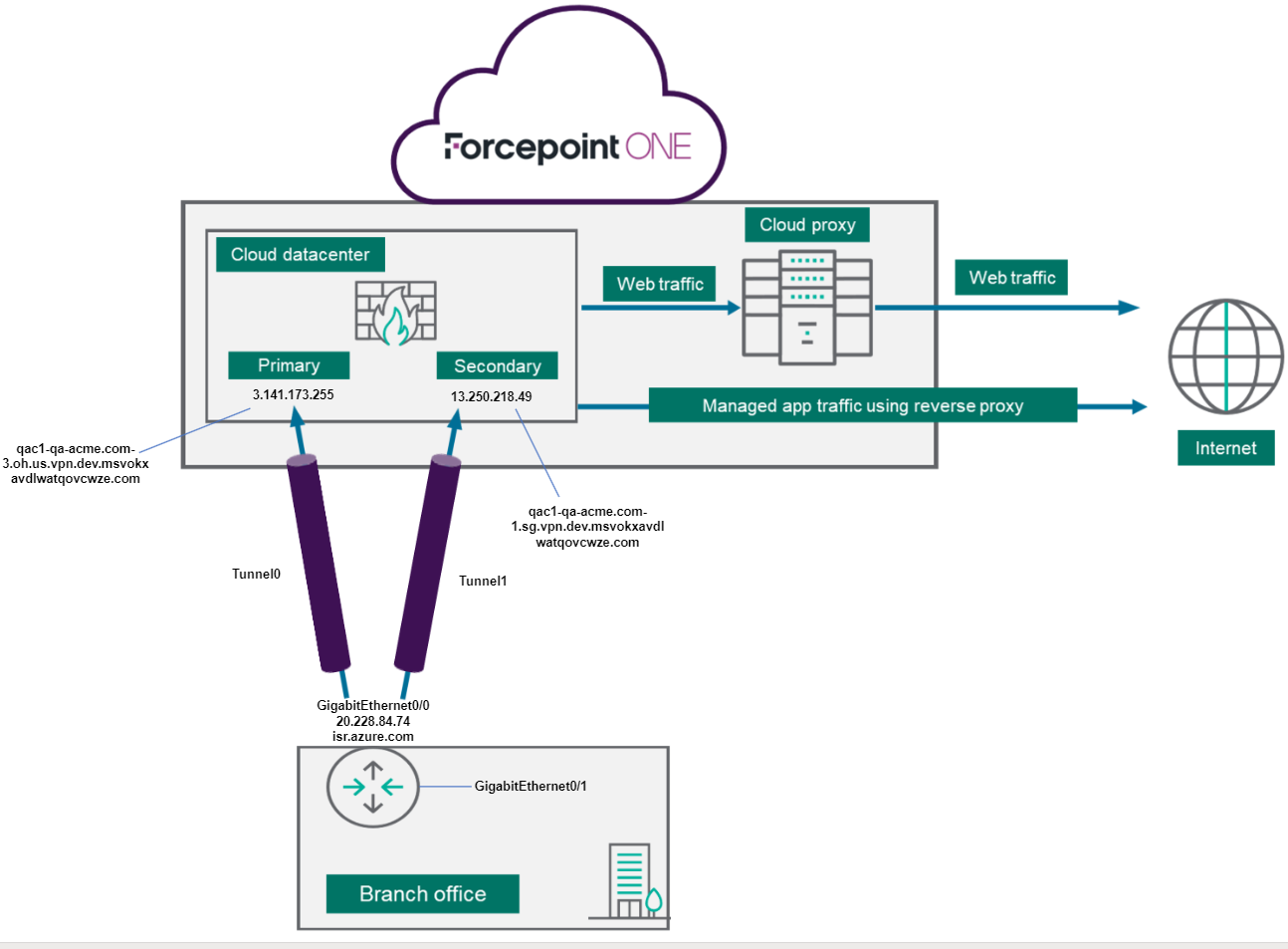
Configurations on Cisco ISR device
This section details the configurations you need to carry on edge device using the details from the page in Forcepoint ONE SSE portal.
Maximum segment size (MSS)
The encapsulation overhead of the IPsec tunnel means that TCP sessions sent over the tunnel must be limited to a lower Maximum Segment Size (MSS) than usual. Most TCP clients will propose an MSS value of 1460 bytes when connecting over an Ethernet network.
Forcepoint ONE SSE recommends setting an MSS value of no more than 1360 bytes in order to leave overhead for IPsec encapsulation. This can often be achieved by using the MSS clamping feature of a firewall or router, to ensure that any TCP traffic sent down the tunnel is limited to an MSS value of 1360.
Where the WAN connection to the Forcepoint ONE SSE data center is using the IPoE or PPPoE protocol, the MSS value may need to be lower still, to account for the encapsulation overhead of the WAN connection.
To display the current MSS setting for your tunnel interface, use the appropriate show interface command on your edge device.