Enabling CloudTrail
To enable CloudTrail tracking for object ACL changes, you must enable CloudTrail and configure the setting in Forcepoint Data Security Cloud | SSE.
Steps
-
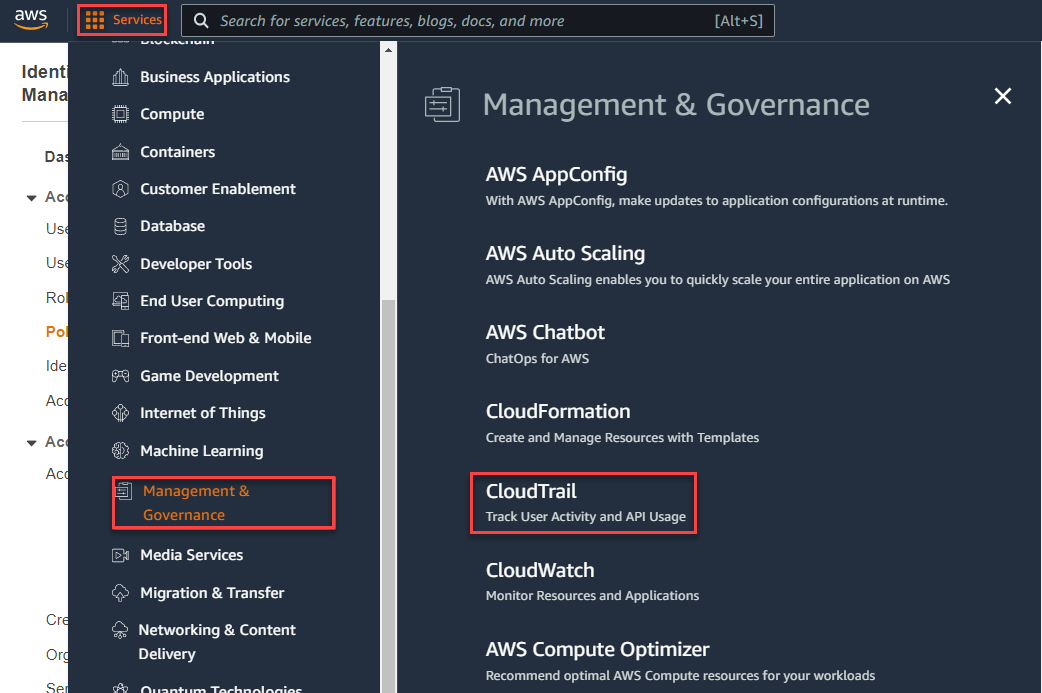
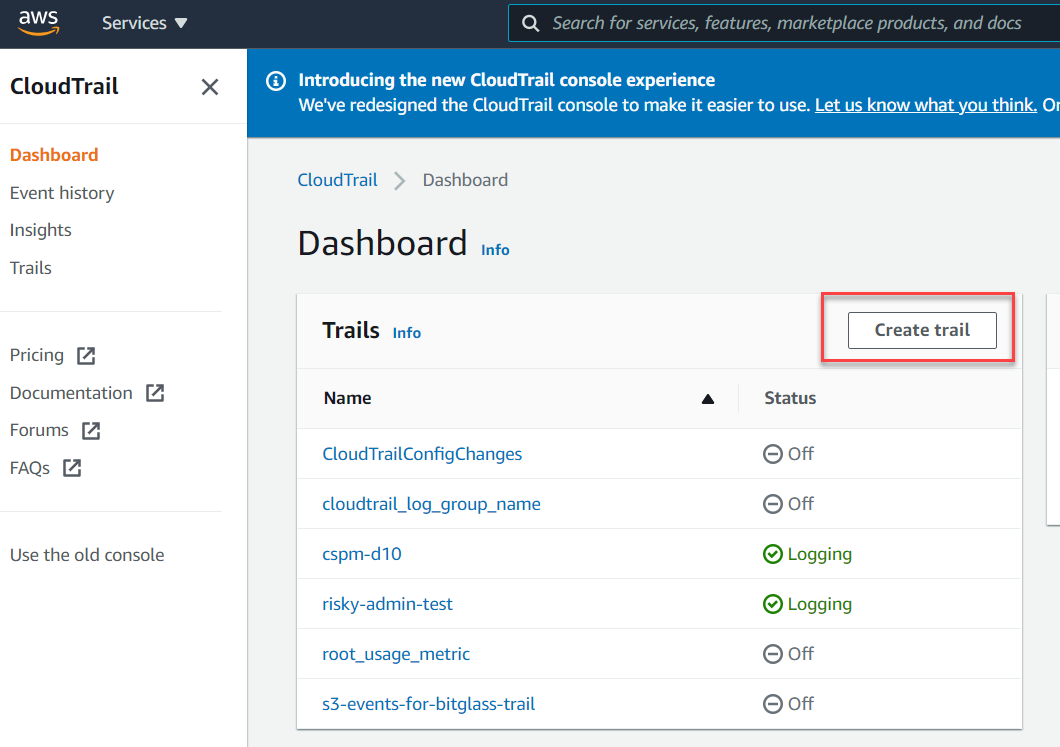
Back on the AWS home, navigate to Services > Management & Governance > CloudTrail > Create trail.
-
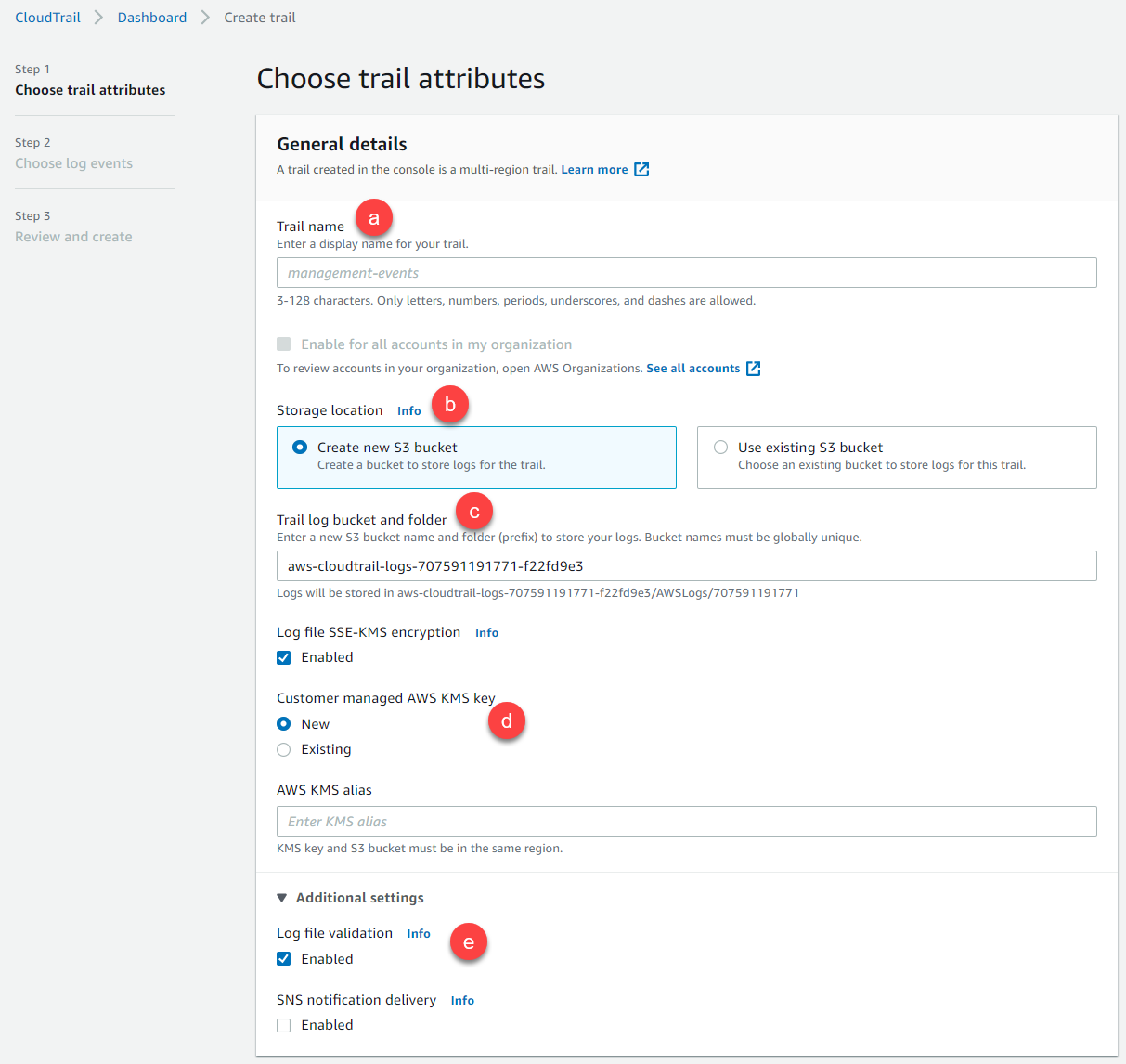
Fill out the fields appropriate to your environment and desired setup.
- Provide a name for the trail.
- Select the storage location (new or existing bucket).
- If new bucket, provide it a name.
- Select if you want the file to be encrypted and if so where the encryption key is being managed.
- Finally, select additional settings for log file validation and/or SNS notification.
- Optional settings are not required but can be configured if desired for cloudwatch and tags. Click Next at the bottom to proceed.
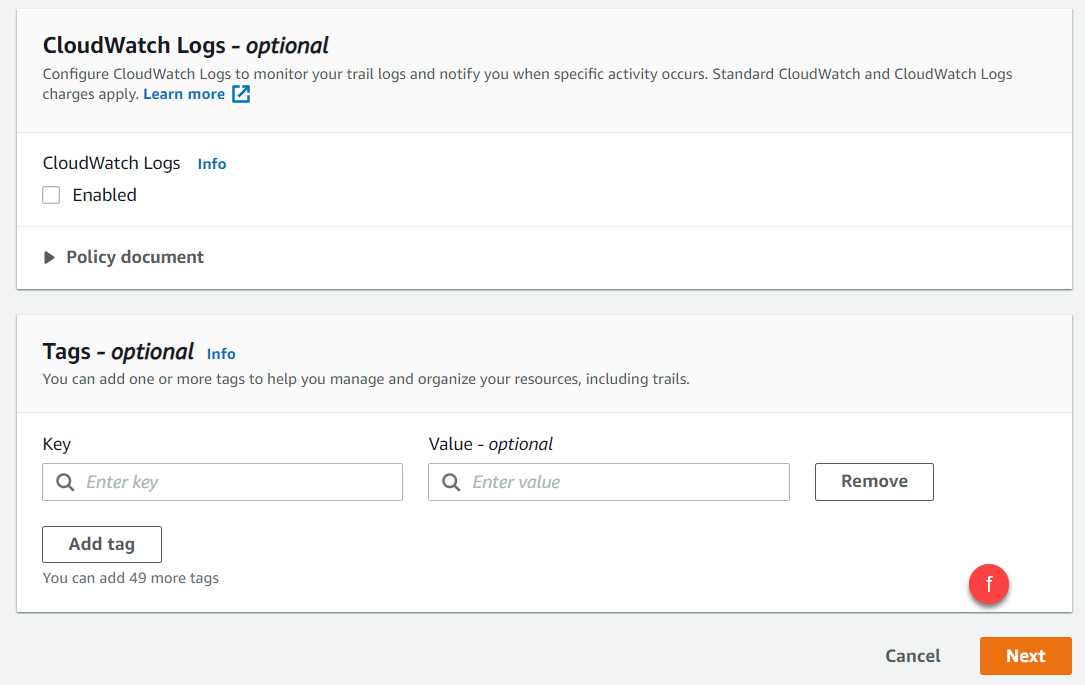
-
On the Events page, select the type of events you want to track as well as the action trigger (read or write) at the bottom and then click
Next to proceed.
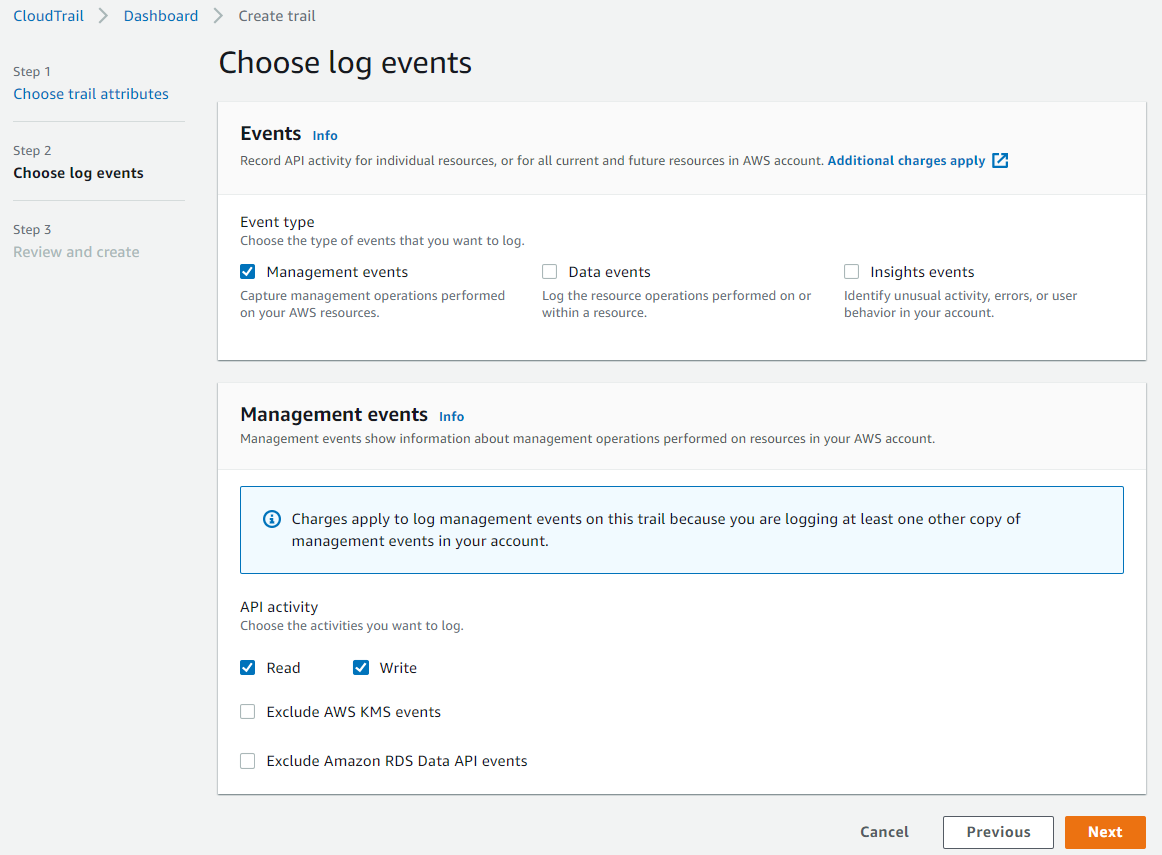
-
On the final page, review your configuration and click Create Trail at the bottom.
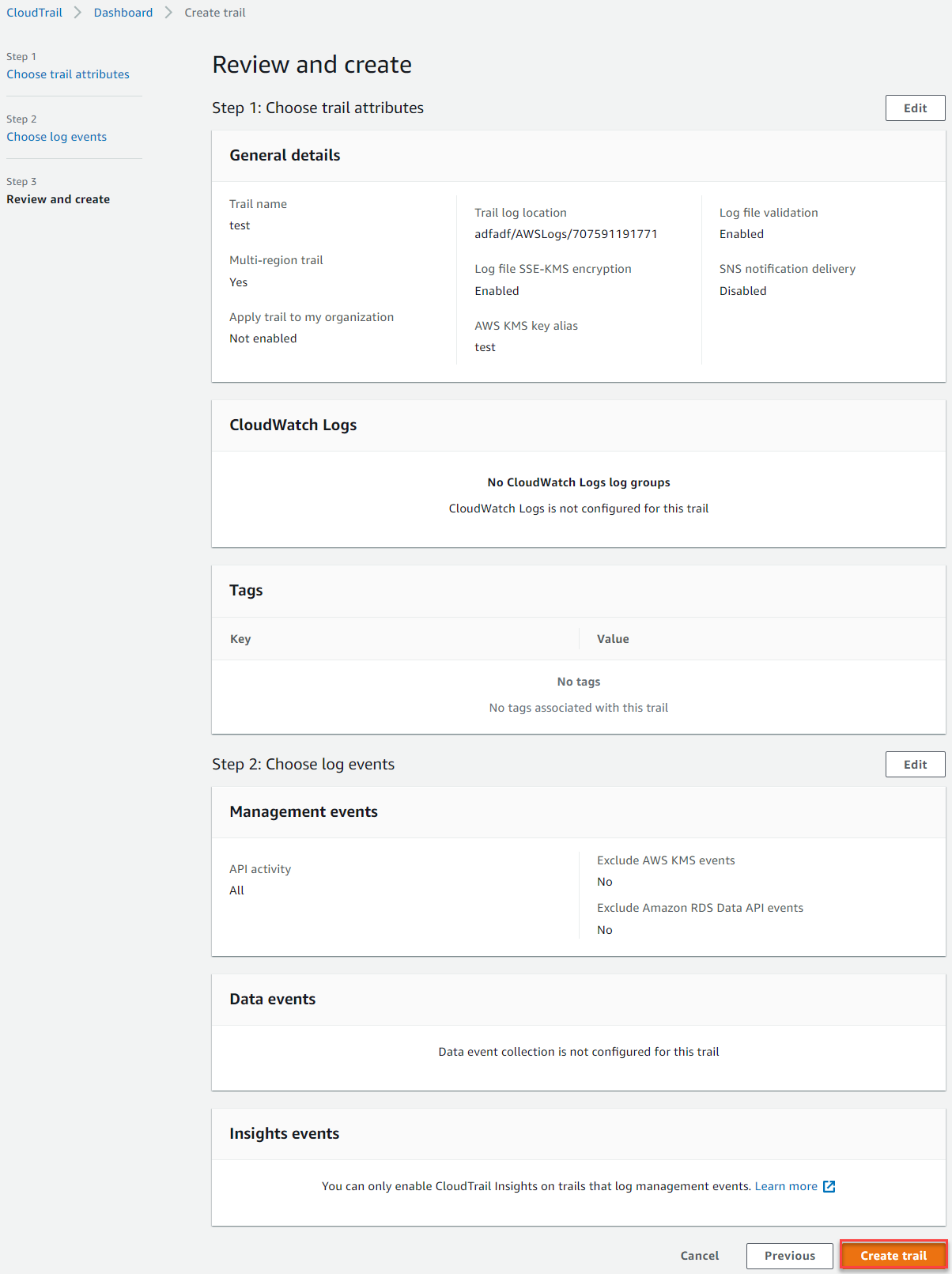
-
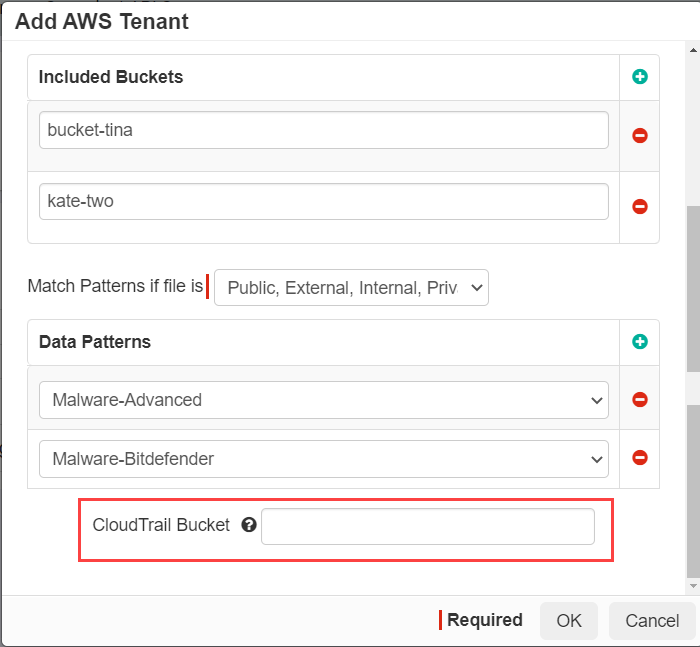
Once you are done, go back to the Forcepoint Data Security Cloud | SSE portal and
navigate to Protect > Policies > AWS > Setup API and click on the API policy instance you want to adjust under API Setup section. Down at the bottom, you will see a field for CloudTrail
bucket. Insert the CloudTrail bucket name that you just created above (or are using to store your CloudTrail). Forcepoint Data Security Cloud | SSE will now scan the Trail results in the bucket to track
changes.