Blacklisting process
Blacklisting is executed as defined in the Access rules. Automatic blacklisting requests are sent as defined in the Inspection Policy.
Figure: Blacklisting process
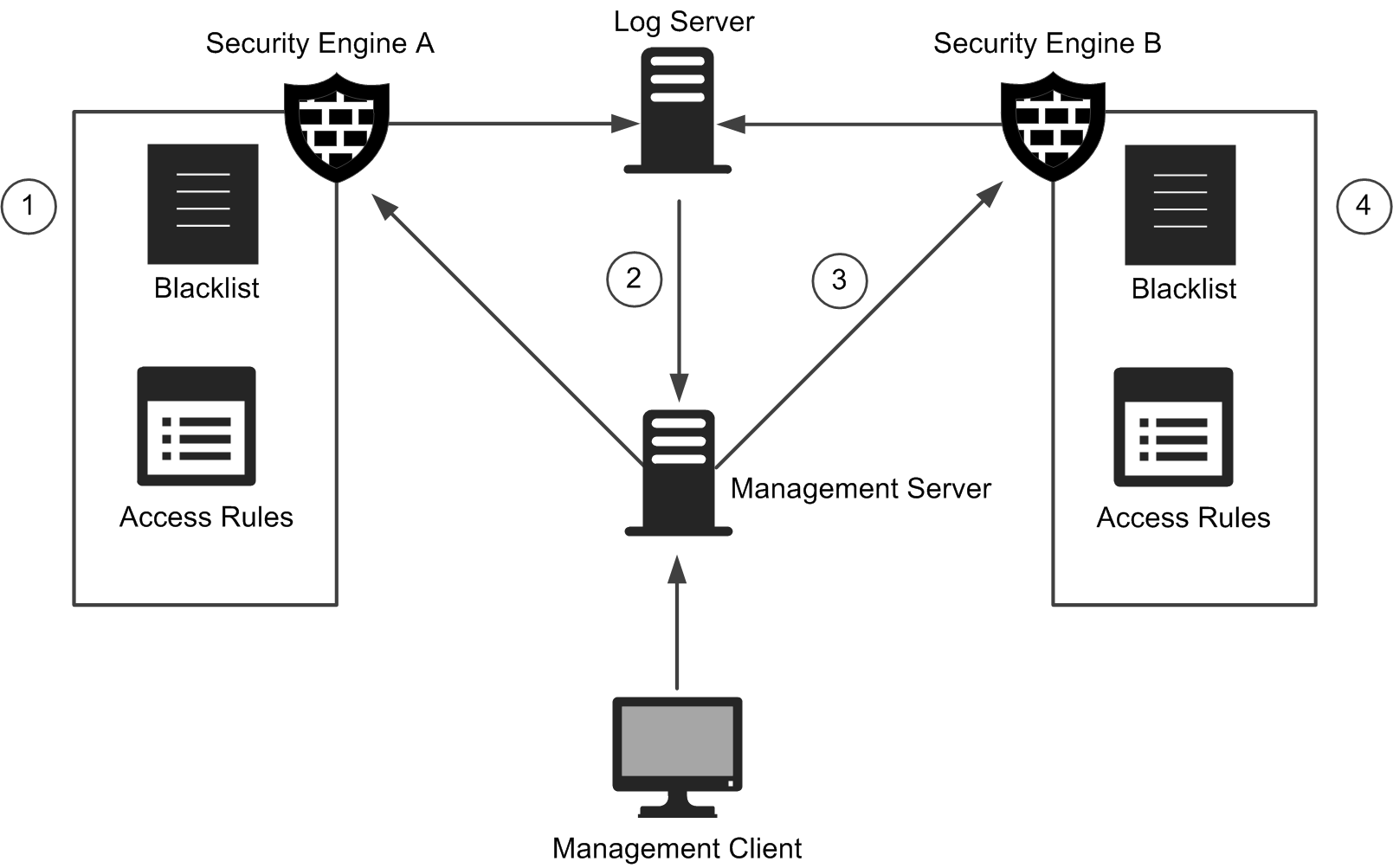
- 1
- Engines add entries to their own blacklists for traffic they inspect.
- There is one blacklist for each Firewall, Layer 2 Firewall, IPS engine, or Virtual Engine.
- In engine clusters, there is one blacklist for each cluster. The nodes in the cluster exchange blacklist information in their synchronization communications.
- 2
- Log Servers send blacklisting requests as a response to correlation of detected events. When one Engine sends a blacklisting request to another Engine, the Log Server relays the blacklisting request to the Management Server.
- 3
- Management Servers relay manual blacklisting commands from administrators, and blacklisting requests sent by Log Servers to the Engines.
There is no direct communication between different Virtual Engines or between Virtual Engines and the Management Server. For this reason, Virtual Engines cannot send blacklisting requests to other Virtual Engines.
- 4
- Engines enforce the entries on their blacklists according to their Access rules.
- Each blacklist entry exists only for a defined duration, after which the entry is removed from the blacklist, and matching connections are again allowed. The duration of the blocking is defined when the blacklist entry is created.
- Access rules check connections against the blacklist. If the IP addresses and ports in one of the blacklist entries match, the connection is discarded.
- If the connection does not match a blacklisting Access rule or its related blacklist entries, the next Access rule in the policy is checked as usual.