Forcepoint NGFW High Availability with Azure Resource Manager
This section provides detailed instructions to deploy and configure Forcepoint Next Generation Firewall using a high availability topology (Active-Active mode) in Azure. This deployment is done using an Azure Resource Manager (ARM) template.
Forcepoint-VM for Azure supports active/passive high availability (HA) configuration. When the Forcepoint-VM detects a failure, the passive firewall instance becomes active and uses Azure API calls to configure its interfaces/ports.
This Azure Resource Manager (ARM) template lets system administrators to automatically:
- Deploy two standalone Forcepoint Next Generation Firewall engines.
- Configure engines to operate in Active-Active mode and to report to an existing Forcepoint Security Management Center (SMC).
- Deploy and configure all Azure network components involved in the stack.
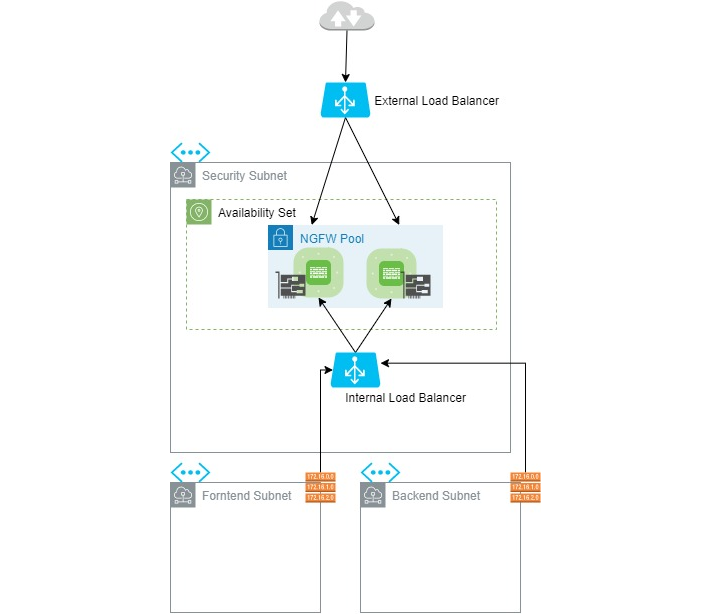
The ARM template is designed to deploy and configure the following resources within the Azure account of the user:
- External Load Balancer (Internet-facing).
- Internal Load Balancer.
-
Virtual Networks (if not already existing) with 3 subnets: subnet-0-security, subnet-1-front and subnet-2-back.
Subnets subnet-1-front and subnet-2-back are used to connect user workloads.
- Two instances of Forcepoint Next Generation Firewall engines either in the same Availability Zone using Availability Sets, or into two different Availability Zones.
- Two NICs one for each Forcepoint Next Generation Firewall engine.
- Azure components instrumental to operate the entire stack: Storage accounts, Route Tables, Security Groups and Public IP addresses
The following diagram provides a description of the workflow between the components involved in this solution: