How single sign-on works
Before you begin
The following diagram illustrates how Forcepoint authenticates users via your identity provider.
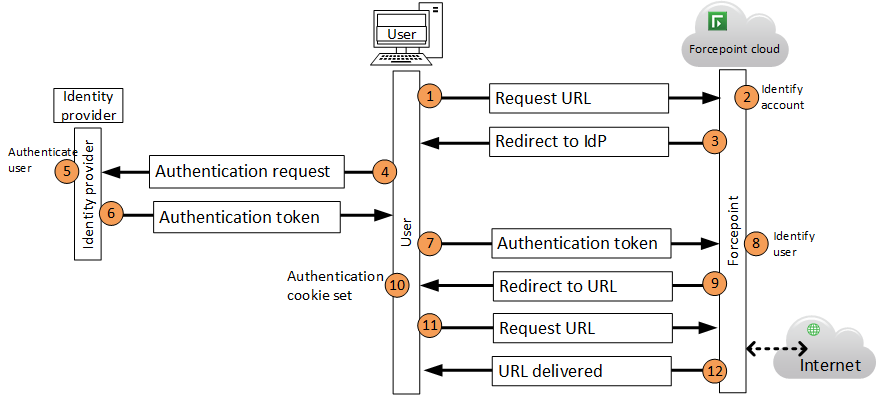
Steps
Next steps
If the user’s policy does not force authentication for requests with known IP addresses, the authentication process for local users happens without user interaction.
If the user’s policy is set to Always authenticate users on first access, or if the user is requesting a category that requires authentication, the user receives the identity provider’s sign in page. The sign in page below is an example from Microsoft AD FS. (This page can usually be customized via your identity provider’s management console)
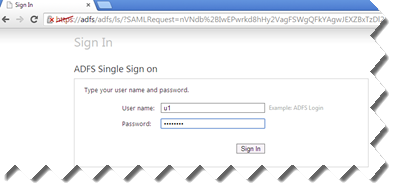
After entering valid credentials, the user is redirected to the requested website.