Introduction
The upgrade process for Forcepoint™ Web Security and Forcepoint™ URL Filtering allows you to upgrade your deployment incrementally, over a period of days or weeks, rather than requiring all machines and components to be upgraded simultaneously. Your deployment will continue to function normally as it is upgraded over a period of time. Policy enforcement, logging, and reporting will continue as the incremental upgrade progresses.
Note, however, that once the incremental upgrade process has started, there are specific limitations that affect the way your software will function, until all machines and components have been upgraded. These include:
- Once the upgrade process has been started, you are not allowed to add new components to your configuration until the full upgrade has been completed.
- After the primary Policy Broker is upgraded, no data synchronization will occur to any replica Policy Brokers that have not also been upgraded.
- When accessing the Forcepoint Security Manager, you can connect only to Policy Server instances whose version is supported by the Security Manager. In addition, the Control Service instance on the Policy Server machine must be running.
- If the database has been upgraded but investigative reports has not, you will need to connect to an older database. Until that happens, investigative report scheduled jobs may fail.
- As the incremental upgrade proceeds, “not running” Health Alerts may appear on the System dashboard for services that are not yet upgraded, even though the service is actually running. The Alert is triggered by a version mismatch and will clear as soon as that component is upgraded.
See Limitations & restrictions for a list of important details.
A security update done for the v8.5.4 product release has resulted in a new requirement for a specific dynamic-link library (dll) when installing or upgrading to v8.5.4 or v8.5.5 on a Windows platform.
See the Install Guide for details.
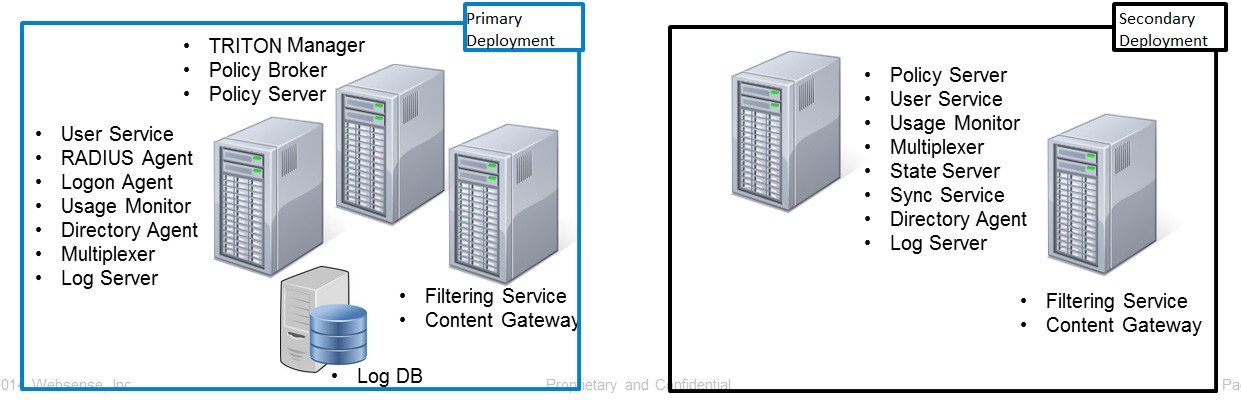
The incremental upgrade process is based on the ability to upgrade one “logical deployment” at a time. Each logical deployment is made up of a Policy Server instance and all components that rely on it.