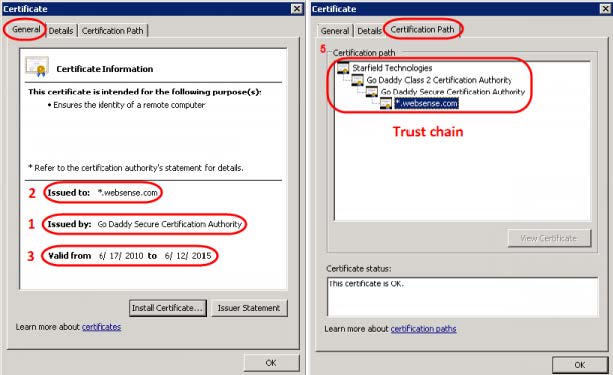
Common verification checks
Common verification checks include:
- The certificate must be issued by a trusted Certificate Authority (CA).
- The fully qualified hostname in the HTTPS request URL and the certificate owner (“Issued to” name) must match.
- The certificate must be current (within its “Valid from...to...” date range).
- The certificate must not be on a revocation list (either CRL or OCSP).
- Checks 1-4 are recursively applied to every certificate in the trust chain.
- The certificate is not self-signed.
Note: In the above list, quoted field names (“ ”) are those used by Internet Explorer.
Below is a certificate as it appears in Internet Explorer 11. The numbers in red correspond to checks in the preceding list.