Standard Forcepoint DLP options
Steps
- Select Network Email to monitor email going through the network or a supported cloud infrastructure such as Microsoft Azure. By default, email is analyzed on all network destinations.
- Click Edit to select the destinations (such as computers, policies, or domains) this policy should analyze.
- Click Direction to select the traffic to monitor: inbound, outbound, internal, or all 3.
Forcepoint DLP Email Gateway analyzes traffic in all 3 directions.
Protectors monitor all traffic directed to them. All transactions are regarded as outbound.
Email Security Cloud protects only outbound traffic.
-
Select Endpoint Email to monitor email on endpoint machines (requires Forcepoint DLP Endpoint). By default, email is analyzed on all endpoint destinations.
- Click Edit to select the domains this policy should analyze.
- If Forcepoint DLP is integrated with Forcepoint Email Security, click Direction to select the traffic to monitor: outbound (default) or internal. Inbound email
cannot be monitored on endpoints.
The selected direction must have been configured under Settings > General > Endpoint > Email Domains to analyze endpoint email traffic.
For a complete list of endpoint email applications that Forcepoint DLP supports, see Forcepoint DLP Endpoint applications.
-
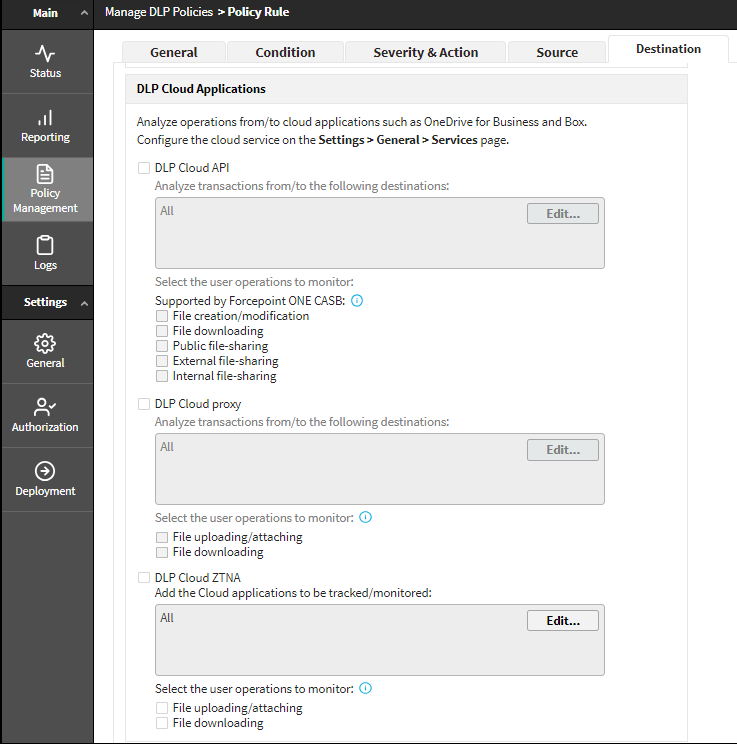
Select DLP Cloud Applications to analyze files sent to supported cloud applications, such as Office365 or Box.
Important:
File analysis occurs only when the following conditions are met:
- Cloud Applications service is activated (Settings > General > Services)
- Forcepoint Security Manager is connected to Data Protection Service (Settings > General > Services)
- The policy was deployed to this service successfully.
By default, all cloud channels are unselected.
Select DLP Cloud API, DLP Cloud Proxy, DLP Cloud ZTNA, or all.
-
If you select DLP Cloud API:
- By default, all applications are selected for monitoring. Select
specific cloud applications to monitor by clicking Edit
and adding available elements to the Selected Elements list. At
least one application must be selected.
If you have an Office 365 cloud application, you can choose to monitor OneDrive, SharePoint, Teams, or Other. Select Other to monitor Office 365 applications that are not OneDrive, SharePoint, or Teams.
- Select at least one user operation to monitor (File uploading/attaching, File downloading, External file-sharing, Unrecognized file-sharing).
- By default, all applications are selected for monitoring. Select
specific cloud applications to monitor by clicking Edit
and adding available elements to the Selected Elements list. At
least one application must be selected.
-
If you select DLP Cloud Proxy:
- By default, all applications are selected for monitoring. Select
specific cloud applications to monitor by clicking Edit
and adding available elements to the Selected Elements list. At
least one application must be selected.
If you have an Office 365 cloud application, you can choose to monitor OneDrive, SharePoint, Teams, or Other. Select Other to monitor Office 365 applications that are not OneDrive, SharePoint, or Teams.
- Select at least one user operation to monitor (File uploading/attaching, File downloading).
- By default, all applications are selected for monitoring. Select
specific cloud applications to monitor by clicking Edit
and adding available elements to the Selected Elements list. At
least one application must be selected.
-
If you select DLP Cloud ZTNA:
- By default, all applications are selected for tracking/monitoring. Select specific cloud applications to track/monitor by clicking Edit and adding available Cloud ZTNA applications to the Selected list. At least one application must be selected.
- Select at least one of the following user operation to
monitor.
- File uploading/attaching - Uploading or attaching a file to a cloud transaction.
- File downloading - Downloading a file from the cloud.
Note: For detailed information, login to https://support.forcepoint.com/ and search for the guide with title Forcepoint DLP and Forcepoint ONE ZTNA Integration Guide, which will be available with future Forcepoint ONE SSE release.
-
Select Mobile Email to monitor email sent to users’ mobile devices, then select whose devices to monitor. It is possible to select user directory entries (users and
groups), business units, or custom users. By default, all users’ email is analyzed when it is being synchronized to mobile devices.
Click Edit to select the users to monitor.
-
Select Web to prevent or monitor users posting sensitive data to networks, domains, business units, URL categories, directory entries, countries, or custom computers via
any of the following web channels:
FTP - file transfer sites
Chat - instant messenger applications
Plain text - unformatted textual content
HTTP - websites, blogs, and forums via HTTP
HTTPS - websites, blogs, and forums via secure HTTP
Endpoint HTTP - websites, blogs, and forums accessed by endpoint machines over HTTP
Endpoint HTTPS - websites, blogs, and forums accessed by endpoint machines over HTTPS
By default, posts to all web destinations are analyzed.
- Click Edit to select the destinations to analyze.
Note that several SaaS domains are excluded from analysis by default. Optionally, exclude more domains or remove domains from the exclusion list. You can also customize the list of resources that are excluded from web policies by default. For more information, see Business Units section.
- Click Channels to select or deselect individual Web channels.
For a complete list of endpoint browsers supported by Forcepoint DLP, see Selecting endpoint destination channels to monitor section.
- Click Edit to select the destinations to analyze.
-
Select Endpoint Printing to analyze files that endpoint users send to printers. (Requires Forcepoint DLP Endpoint.)
To select the printers to analyze click Edit.
-
Select Endpoint Application to analyze content that is being cut, copied, pasted, or otherwise handled by users on endpoint applications.
To select the application groups to analyze, click Edit.
Not all operations (cut, copy, paste, etc.) relate to all applications. The operations that are monitored are specified for each group.
Note that if you choose All activities on the rule’s condition page and choose an online application here, you are requesting to monitor all content that is
downloaded to endpoints. The same is true if you specify the Download operation in the online application group, then select this group.
To prevent the system from analyzing content that is cached on the endpoint, the following occurs:
- When files are saved to the browser’s cache folders, the crawler analyzes only .exe, .csv, .xls/xlsx, .pdf, .txt, .mht, and .doc/.docx files.
- When files are saved to any other local folder, it analyzes all file types.
For a list of applications that the system supports out of the box, see Forcepoint DLP Endpoint Applications section. You can also add custom applications.
Note: The list you create here is overridden by trusted application settings you configured under Resources > Endpoint Applications. Groups that are trusted on that page are not enforced even if they are included in the policy. -
Select Endpoint Removable Media to analyze media such as thumb drives, external hard drives, and other USB devices on endpoint machines. By default, all removable media is
included.
- To select the media to analyze, click Edit.
- For a complete list of supported endpoint removable devices, see Selecting endpoint destination channels to monitor section.
- Linux-based endpoints cannot share removable media devices through NFS.
-
Select Endpoint LAN to analyze endpoint file copy over LANs. By default, outbound traffic for all networks is covered—that is, traffic going from the endpoint to all
LANs.
Endpoint LAN control is applicable to Windows file sharing only.
To select a network to analyze, click Edit.
- Specify a list of allowed destination IP addresses or hostnames for LAN copy.
Users may connect to a destination machine using the hostname, IP address, or mapped drive, for example. Forcepoint DLP does not resolve the multiple names for a single destination. To block or allow access to a machine, specify each of the identifiers a user might specify: for example, FQDN, hostname, mapped drive, and so on. Alternatively, always block or allow access using hostname and require users to use hostname.
- Data from an endpoint client can be intercepted.
- If access to the LAN requires user credentials, files larger than 10 MB are handled as huge files which are only searched for file size, file name, and binary fingerprint. Files smaller than 10 MB are fully analyzed. The huge file limit for other channels is 100 MB.
- Specify a list of allowed destination IP addresses or hostnames for LAN copy.