Configuring Okta SSO with SAML 2.0 protocol
Forcepoint Security Manager supports Single Sign-On (SSO) via SAML 2.0 protocol, and certified for Okta identity provider. This helps the user to login to the Forcepoint Security Provider using SSO.
Complete the following steps to configure Okta with SAML 2.0 protocol.
Steps
- Sign into the Okta portal using the Okta account.
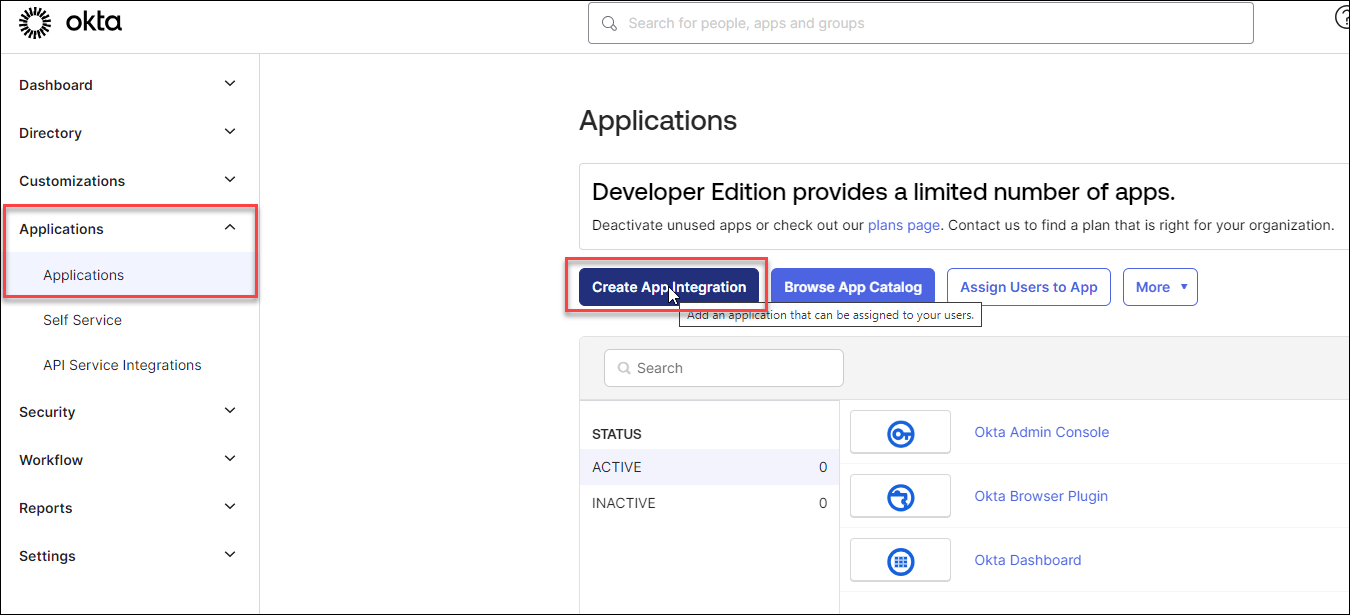
- On the left navigation pane, click the Applications drop-down.
-
From the Applications drop-down, click the Applications.
The Applications page opens.
-
Click the Create App Integration button.
-
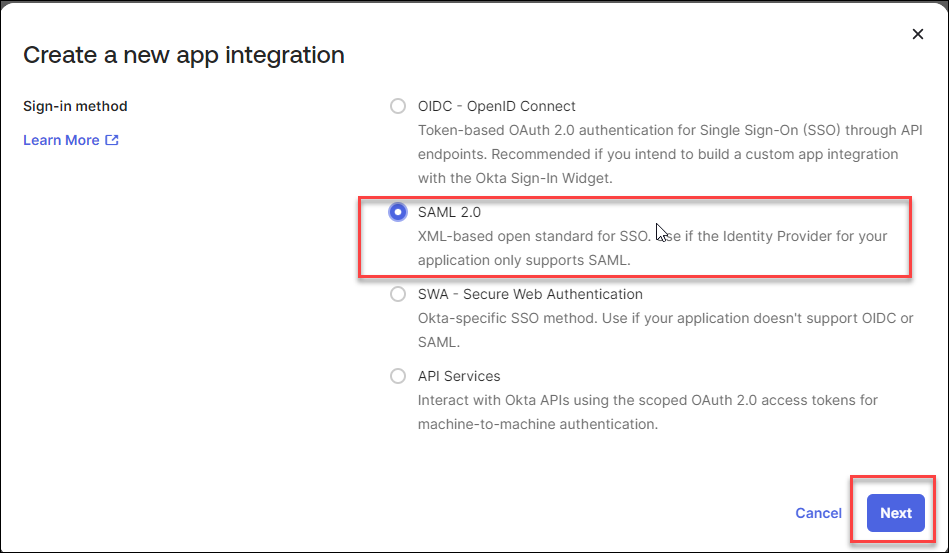
On the Create a new app Integration dialog, select the SAML 2.0
option, and then click the Next button.
The Create SAML Integration page opens.
-
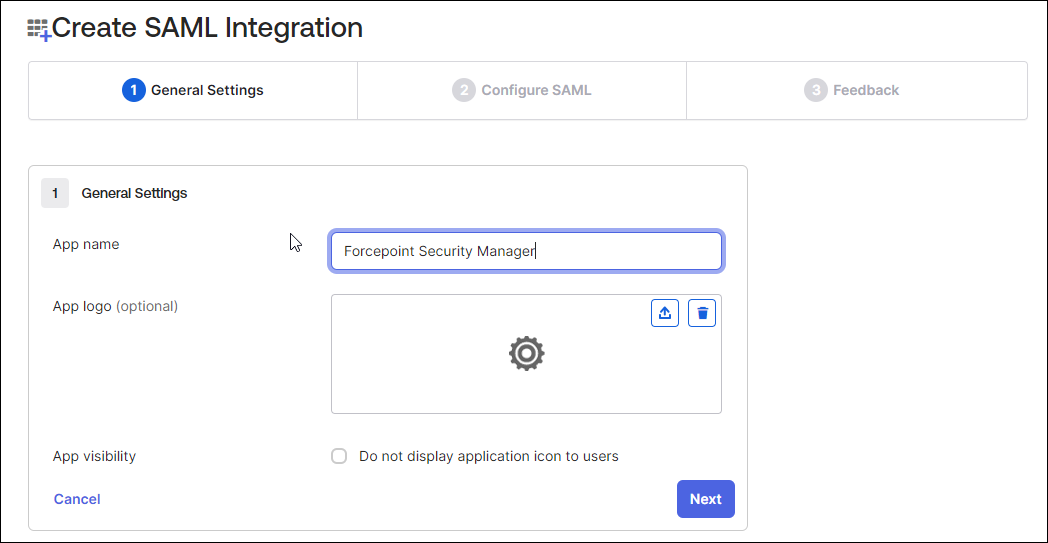
In the General Settings tab:
- In the App name field, enter the name of application e.g. Forcepoint Security Manager.
- (Optional) Add the logo into App logo box.
Click here to download Forcepoint Security Manager logo
- Click the Next button.
-
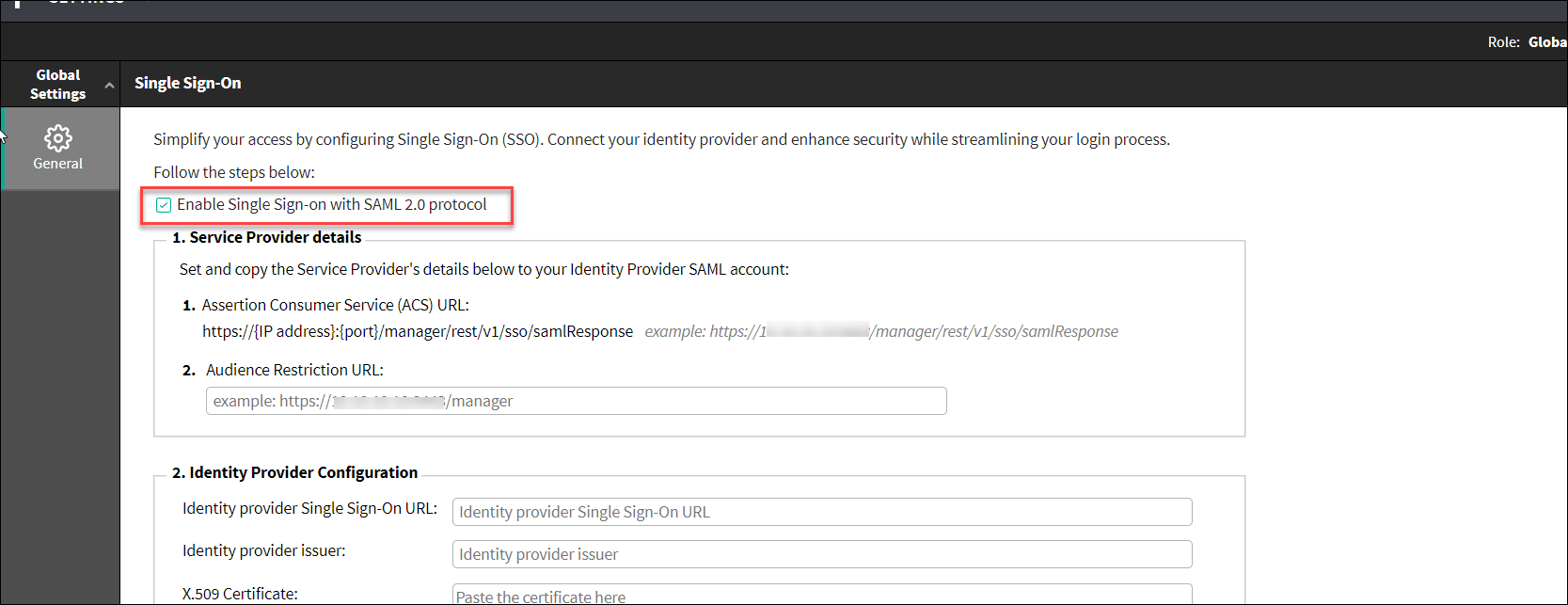
Open Forcepoint Security Manager and navigate to Global Settings > General > Single Sin-On.
In Single Sign-On page:
- Enable the SSO feature by selecting Enable Single Sign-on with SAML 2.0 protocol checkbox.
-
Go back to Create SAML Integration page.
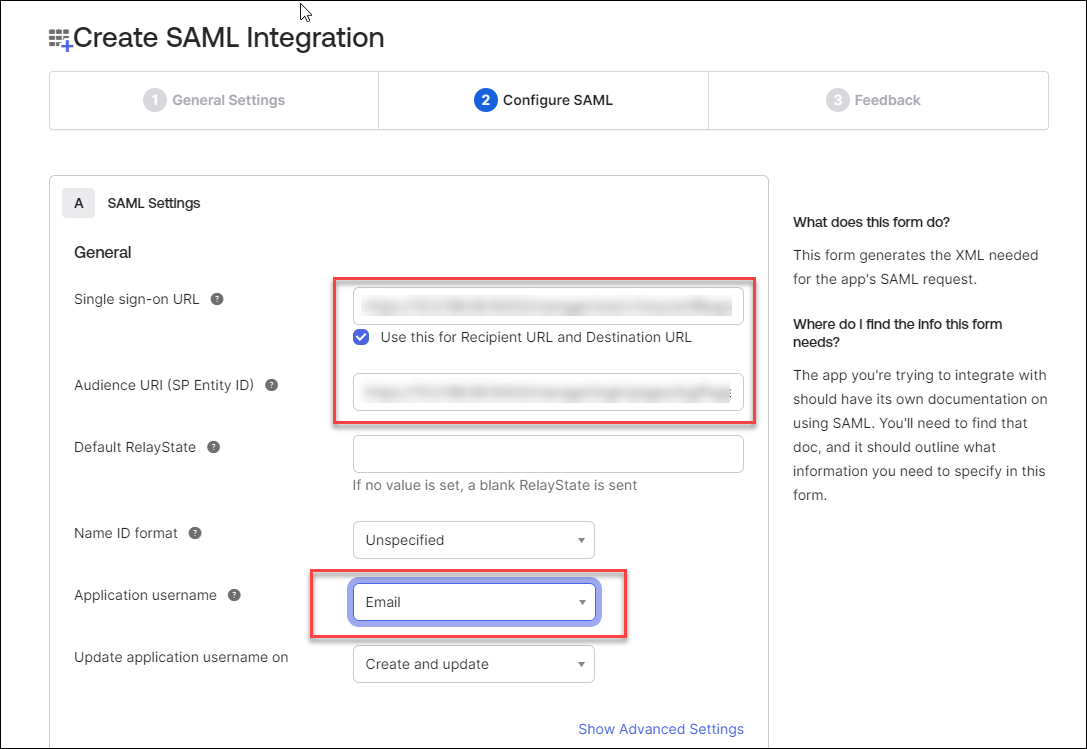
Under the SAML Settings section:
- Enter the Single sign on URL and Audience URI (SP Entity ID).
- Check the Use this for Recipient URL and Destination URL checkbox.
- Select Email from drop-down as the Application username.
-
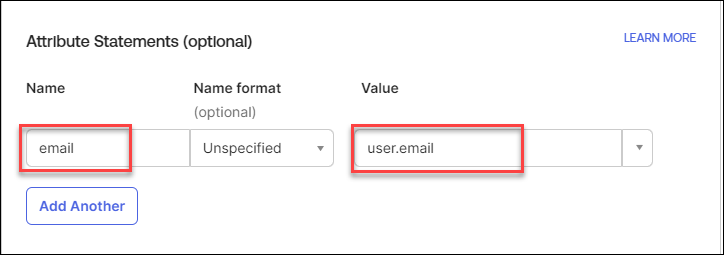
Navigate to the Attribute Statements (optional) section:
- Add 'Email' for Name and 'user.email' for Value.
- Click Next button.
- Click Finish to save the details.
- Go to Directory, and then click People.
- Select user from Person & Username list.
-
Click on Assign Applications from Application tab.
Assign Applications window opens.
- Click Assign button to assign the application, and click Done.
-
In Assignments tab:
Note: To log in to the Forcepoint Security Manager using SAML SSO, users must be assigned to the Forcepoint Security Manager application in the Okta portal.
-
Navigate to Forcepoint Security Manager application in okta, go to
Settings:
- Scroll down for the SAML Setup section, click the View SAML
setup instructions button.
The How to Configure SAML 2.0 for Forcepoint Security Manger Application page opens.
- Scroll down for the SAML Setup section, click the View SAML
setup instructions button.
- Copy the Identity Provider Single Sign-On URL, Identity Provider Issuer, X.509 Certificate from Okta.
-
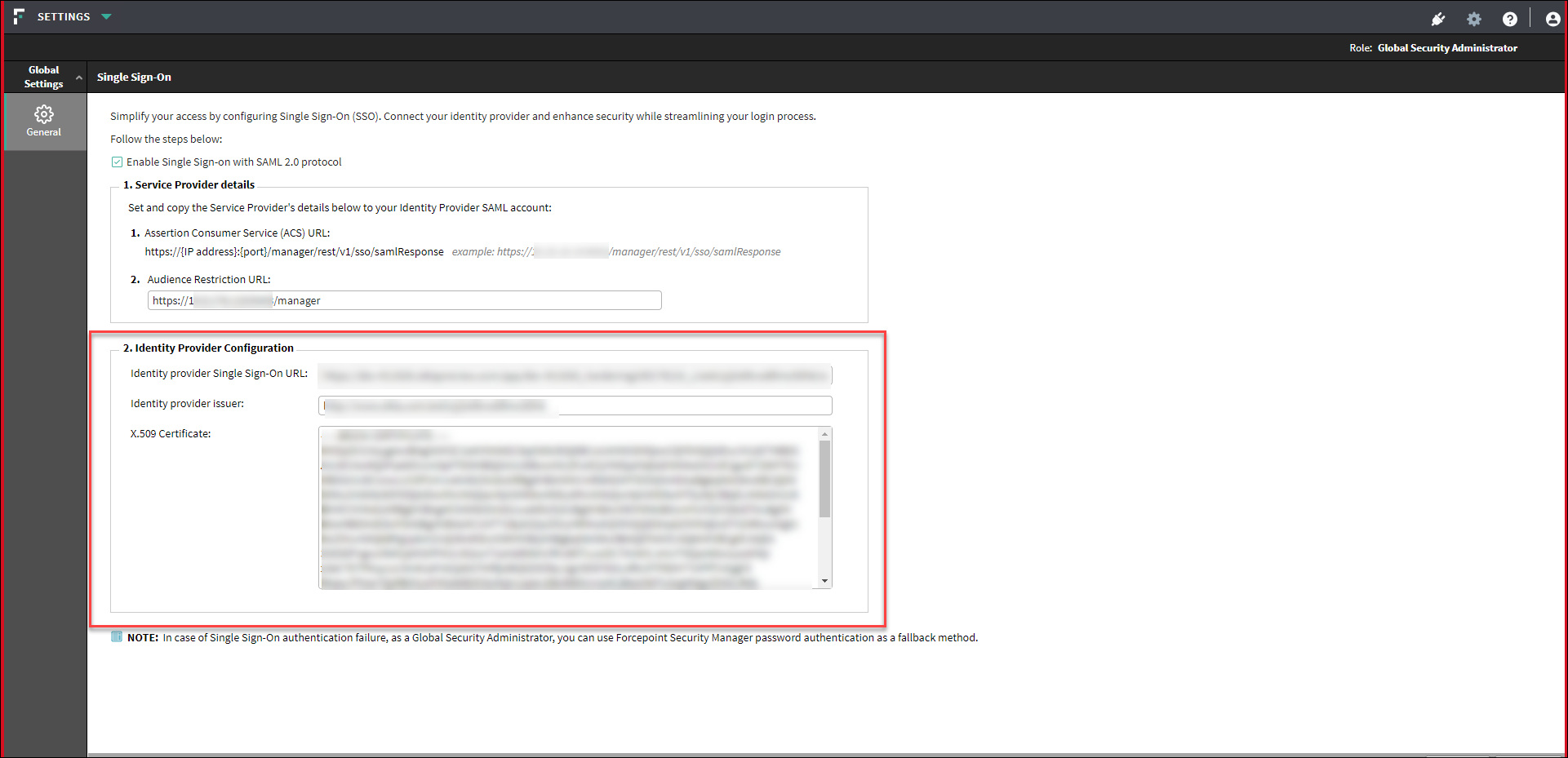
Open Forcepoint Security Manager and navigate to Global Settings > General > Single Sign-On.
In Single Sign-On page:
- In Identity Provider Configuration section, enter Identity Provider Single Sign-On URL, Identity Provider Issuer, and X.509 Certificate copied from previous step.
-
Go to Forcepoint Security Manager.
In Administrators page:
- Add a new user with the Okta user email address.
Now, Forcepoint Security Manager is able to access with SSO.
- Add a new user with the Okta user email address.
-
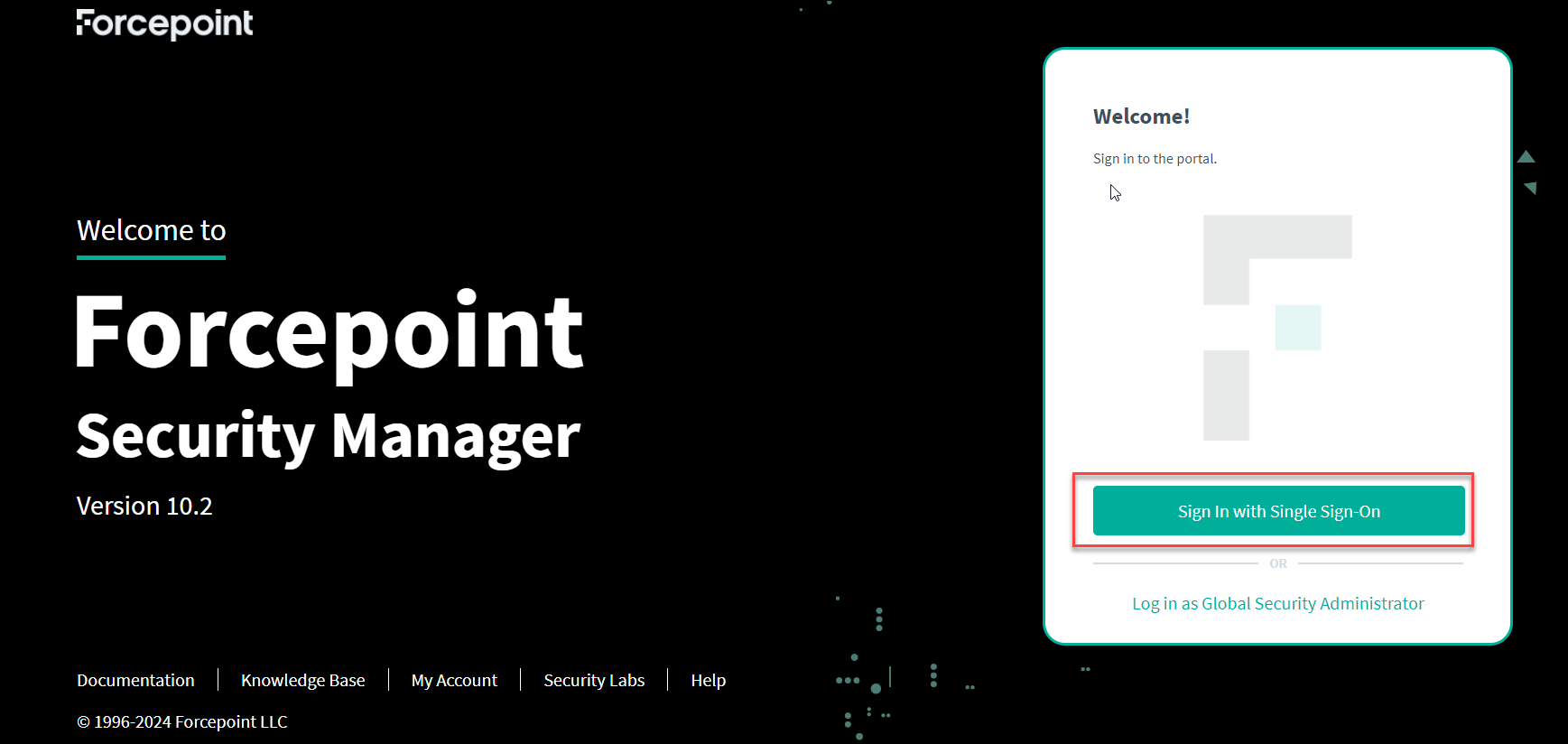
In Okta, navigate to My settings > Open link in new tab.
- Go to My Apps, a new application Forcepoint Security
Manager will be available.
By using this Forcepoint Security Manager application in Okta, the user can login to the Forcepoint Security Manager using SSO.
When the user click on the newly added Forcepoint Security Manager application, the system redirects you to the Forcepoint Security Manager portal from the Okta account.
- Go to My Apps, a new application Forcepoint Security
Manager will be available.