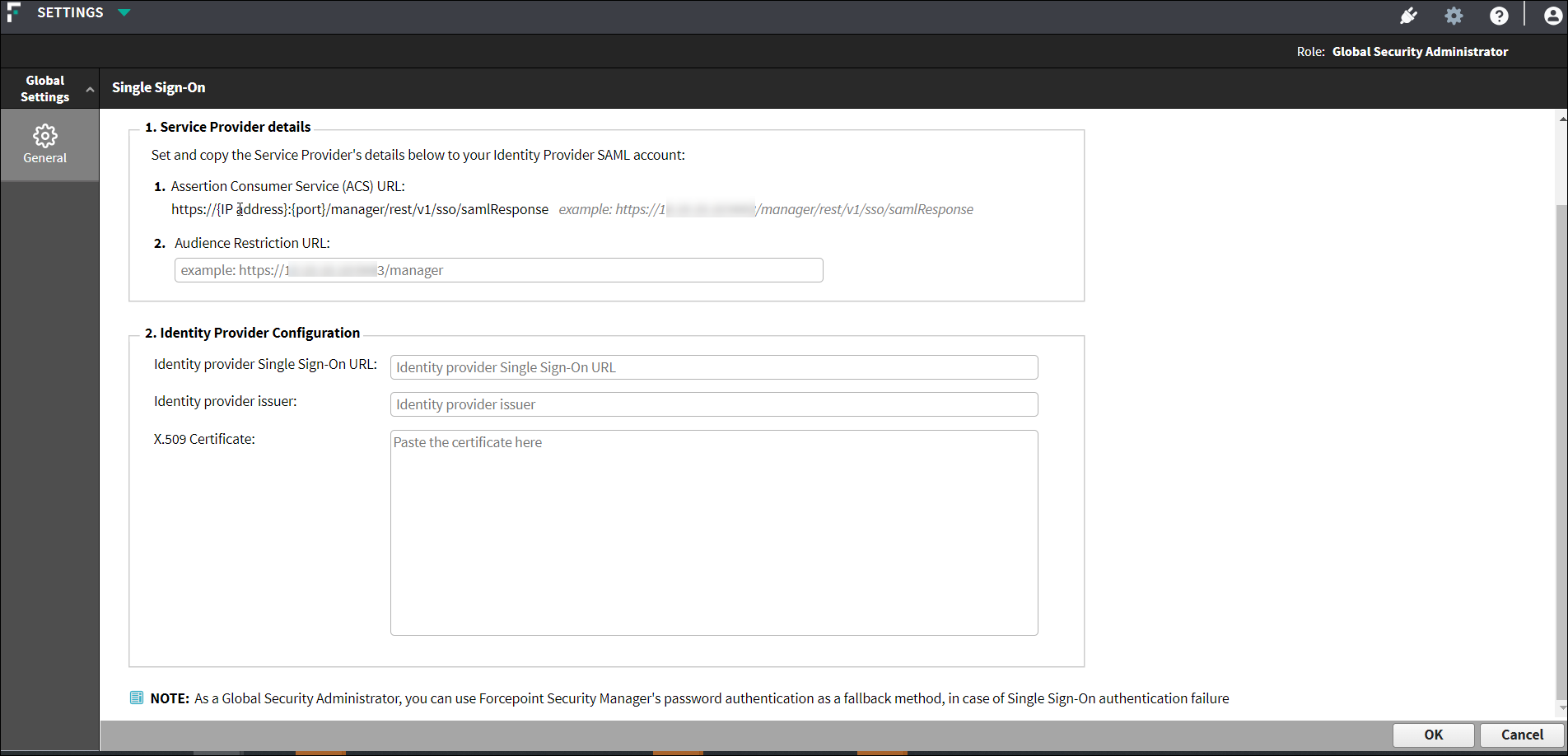
Single Sign-On
Forcepoint Security Manager supports Single Sign-On (SSO) via SAML 2.0 protocol. This feature allows the user to login to the Forcepoint Security Manager using Single Sign-On (SSO). It improves Forcepoint Security Manager user access experience and facilitates the cross-platform login.
- Okta
- Azure
Users who choose Okta as identity provider, can login to the Forcepoint Security Manager from their Okta portal. To do so, you must complete the configuration of the Okta for SAML 2.0 protocol, and must complete the SSO configuration in Forcepoint Security manager. Fore more information about the Okta configuration, see Configuring Okta SSO with SAML 2.0 protocol section.
Users who choose Azure as identity provider, can login to the Forcepoint Security Manager from their Azure portal. To do so, you must complete the configuration of the Azure for SAML 2.0 protocol, and must complete the SSO configuration in Forcepoint Security manager. Fore more information about the Azure configuration, see Configuring Azure AD SSO with SAML 2.0 protocol section.
- Global Security Administrator can use Forcepoint Security Manager's password authentication as a fallback method, in case of Single Sign-On authentication failure.
- Only Global Security Administrator can use User name and Password when SSO is enabled.
To configure SSO in Forcepoint Security manager, complete the steps below: