Getting started with forwarding traffic
You can forward traffic to a proxy service where the traffic can be, for example, scanned for malware before the traffic continues to its final destination.
You can configure a Single Engine or Engine Cluster to forward FTP, SMTP, HTTP, and HTTPS traffic. The main benefit in using the engine to forward traffic to a proxy service is that the forwarding works transparently: the communicating hosts need no additional proxy configuration when the forwarding is done for them at the engine.
Proxies are typically used for malware scanning and content filtering, but there are more applications. Using an external service allows you to expand the capabilities of the engine with many other types of content screening. For example, the service can strip certain types of attachments out of emails without blocking the message itself. This type of feature is available directly on the engine as well, but an external service is a better option in medium to high throughput environments.
For the FTP or SMTP protocols, you cannot use inspection and forwarding. You must either forward the traffic or inspect the traffic locally. You cannot do both.
Figure: Forwarding traffic
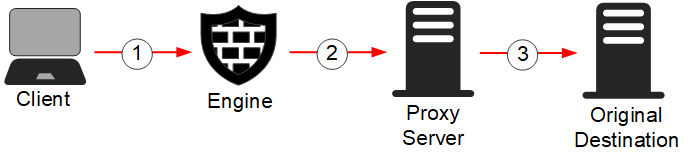
- 1
- Traffic from the client arrives at the Secure SD-WAN Engine.
- 2
- Access rules or NAT rules in the Engine policy determine which connections are forwarded to the proxy service for inspection.
- 3
- The traffic is inspected and forwarded to the original destination. Reply packets are received with the IP address of the proxy service, so they are also forwarded to the proxy service.