Forwarding traffic configuration overview
Use Access rules or NAT rules to forward FTP, SMTP, HTTP, and HTTPS traffic to a proxy service, such as Forcepoint Web Security Cloud.
Figure: Elements in the configuration
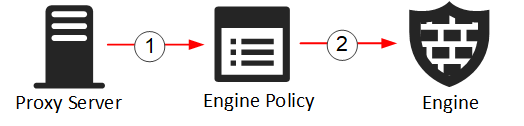
- 1
- The Proxy Server element is referenced in the Engine Policy.
- 2
- The Engine Policy is installed on the Secure SD-WAN Engine.
Follow these general steps to configure forwarding traffic:
- Create the Proxy Server element that represents the proxy service.
- Define the Access rules or NAT rules that select traffic for forwarding.
NAT considerations when using Access rules
We recommend that you use Access rules to forward traffic. However, if you have a more complex environment and existing NAT rules, forward traffic using the NAT rules method instead. When you use Access rules to forward traffic, all existing NAT rules in the policy are ignored, but element-based NAT is taken into account. All destination NAT definitions are ignored. If element-based source NAT definitions have been defined and if default NAT has been enabled in the properties of the Secure SD-WAN Engine, those NAT definitions are processed.
Element-based NAT is sufficient in most cases, but if you need to use NAT rules to have greater flexibility, you must forward traffic using the NAT rules method. Use NAT rules if you want to, for example, forward traffic while using Outbound Multi-Link elements to select the network link for the traffic.