How route-based VPNs work
In route-based VPNs, any traffic that is routed to a tunnel interface and allowed by Access rules is automatically sent through the tunnel to the peer endpoint.
Devices that provide VPN access are called VPN gateways. With route-based VPNs, you can create only site-to-site VPN tunnels between gateway devices. It is not possible to create a mobile VPN tunnel using Route-based Tunnels.
Due to the various authentication and encryption methods that the IPsec protocol supports, the number of settings is rather high. To reduce configuration work, you can use reusable profiles for storing different types of settings. These and other elements related to Route-based Tunnels configurations are pictured in this illustration.
Figure: Route-based Tunnels configuration example
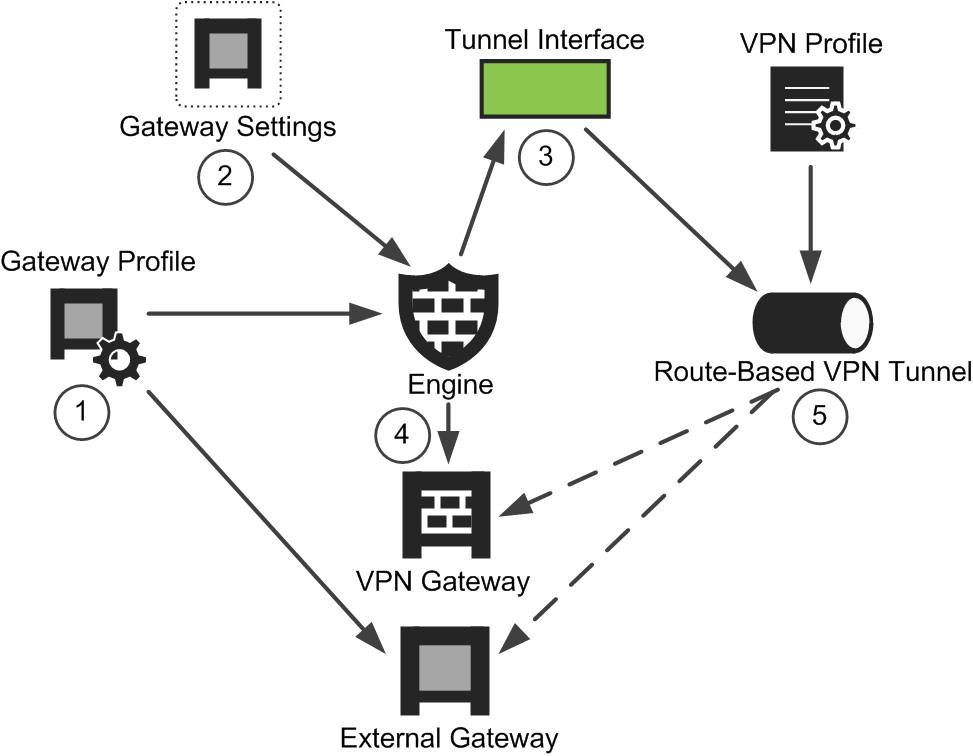
- 1
- The Security Engine and External Gateway refer to a Gateway Profile element that contains information about the capabilities of different types of gateways.
- 2
- The Security Engine optionally refers to a Gateway Settings element that defines settings for advanced VPN performance tuning.
- 3
- The Security Engine has a Tunnel Interface element defined.
- 4
- The Security Engine has a VPN Gateway element defined.
- 5
- The Route-based Tunnels element refers to both ends of the VPN tunnel: the VPN Gateway and External Gateway.