How Forcepoint Web Security Cloud works
Web Security operates as a proxy server for HTTP and HTTPS traffic, as well as FTP over HTTP. When users request a web resource, their browsers do not connect directly to Internet web servers (shown in the following diagram as origin servers), but instead connect to the cloud proxy, which in turn relays requests to the origin server. This allows the cloud service to apply filtering rules and perform content scanning, providing protection against security threats, data loss, and inappropriate content.
The service can use various methods to identify and authenticate users: a Forcepoint Endpoint client, a third-party single sign-on identity provider, NTLM transparent identification, or manual authentication with a user name and password. Roaming users (those connecting from an unknown IP address) can be identified via the Forcepoint Endpoint client, via a single sign-on provider, or they are required to authenticate.
Optional SSL decryption allows the content of HTTPS sessions to be scanned, and allows the service to show the correct notification page to users (for example, a block page if the SSL site is in a category that is blocked). Content is re-encrypted after inspection. The following diagram shows a basic overview of web traffic protected by Forcepoint Web Security Cloud.
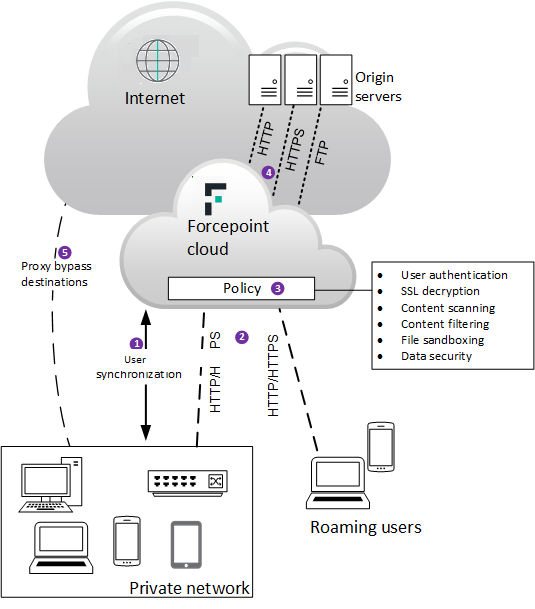
- Identity management allows user details to be synchronized with the cloud, enabling users to be identified and authenticated. This allows user- and group-level policy settings to be applied, as well as providing detailed user-level reporting.
- Web traffic is directed to the cloud service from a private network, and from roaming users connecting from outside their LAN. There are various methods to redirect traffic (see in Key concepts).
- Authentication, filtering and enforcement settings are applied by a policy, which determines which requests to allow or block, performs real-time content scanning, and applies data security filtering, helping to prevent inadvertent or malicious data loss.
- When policy decisions have been applied, web requests are then forwarded to the origin server, and content is served to the user’s browser. If content is blocked, or security threats are detected, configurable notification pages are shown, informing the user of the reason why access to the resource is not allowed.
- Some web requests can go directly to the origin server, if the address is defined as a proxy bypass destination.
Secure (HTTPS) sessions are forwarded over a tunneled connection. If you enable SSL decryption, the content of these sessions can be scanned and policy settings applied, before the traffic is re-encrypted. This feature requires you to install a root certificate on end-users’ machines, allowing clients to connect securely to the cloud proxy. (See Enabling SSL decryption in the Forcepoint Web Security Cloud help for more information.)