Use the provided Forcepoint Data Security Cloud | SSE Python script which calls the Okta API to
setup the ACS Proxy.
Before you begin
This setup will assume you already have Okta configured and integrated with the protected app you are trying to protect with
Forcepoint Data Security Cloud | SSE. Okta has created
a guide page to cover all of the steps and fields that need to be
configured to configure the ACS proxy. However, there is one setting configuration that must be changed that cannot be done directly via API calls (setting the Sign On setting to manual). The only
field you directly need to update is the ACS URL (ssoAcsUrlOverride). Step 3 below will cover the exact items you will need to manually change in the Python script provided. The below Python script
that
Forcepoint Data Security Cloud | SSE has created will call the Okta API to set the ACS Proxy URL while also changing the Sign On Setting automatically.
Note:
- The bitglass_continue in the ACS proxy URL is optional. It is only required and used when the SAML response does not contain the
SubjectConfirmationData section. Otherwise, Forcepoint Data Security Cloud | SSE will take the URL to send the response from the Recipient.
- Forcepoint Data Security Cloud | SSE supports UTF-8 characters. However, the SAML assertion only supports low-ASCII characters as attribute values. If an attribute value contains
characters that are not low-ASCII, then SAML sign-in failures occur.
This is helpful for customers who have Okta currently deployed (set up as the IdP) with protected applications and do not want to remove/change that integration to deploy Forcepoint Data Security Cloud | SSE in our normal SSO workflow (app points to Forcepoint Data Security Cloud | SSE as IdP and then Forcepoint Data Security Cloud | SSE
points to Okta as IdP for source of authentication).
In ACS Proxy mode, Okta is set as the IdP for the protected cloud app and then Forcepoint Data Security Cloud | SSE is set as the IdP for Okta. A user attempting to login to the
protected cloud app will be redirected to Okta for authentication like they are used to. After authenticating, Okta will send the SAML request with approved authentication to Forcepoint Data Security Cloud | SSE where Forcepoint Data Security Cloud | SSE can then assess the user's authentication and apply policy (that is check for context of access such
as managed or unmanaged device, apply MFA, provide inline policy action, etc).
Note:
- Okta only supports setting the ACS proxy via API for predefined apps. This will not work on a custom app you have created in Okta.
- For M365, if the IdP does not send back the emailAddress attribute (Okta has no way of doing that currently), you should lookup the user based on UPN. In this mode, users cannot be auto
provisioned.
Steps
-
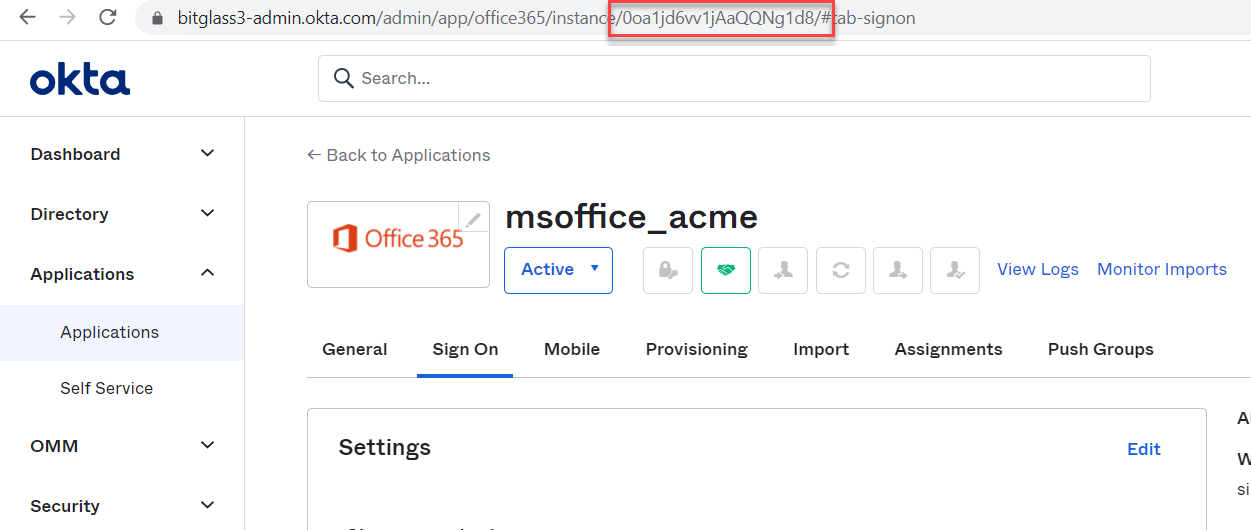
Make sure you know the application's Okta ID before you start.
You can find this information by logging into the Okta admin portal and navigating to your app and locating the App ID in the URL:
-
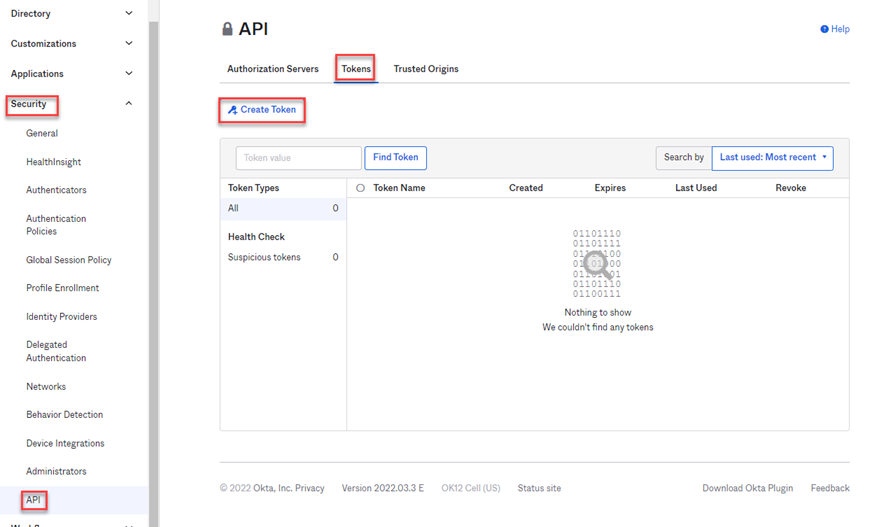
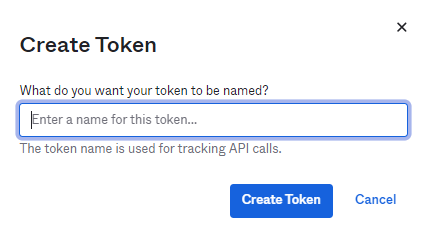
Create an OAuth Token in Okta and save the token to be used in the Python script below. In Okta, navigate to , click Create Token. Provide a recognizable name.
-
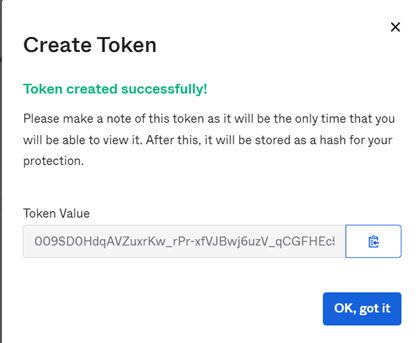
Enter the name of the token and click Create Token. Copy the token value and save it somewhere.
-
Once you have the App ID, you can now run the below Python script from any Linux based machine to automatically set the ACS Proxy field for your app. As mentioned
above, this Python script will also correctly set the Sign On settings of the app to manual:
import requests
url = "<Okta App URL>"
headers = {'Authorization': 'SSWS <Your Oauth Token>'}
r = requests.get(url, headers=headers)
resp = r.json()
print(resp['settings']['signOn'])
resp['settings']['signOn']['ssoAcsUrlOverride'] = 'https://portal.bitglass.com'
#resp['settings']['signOn']['ssoAcsUrlOverride'] = 'null'
p = requests.put(url, json=resp, headers=headers)
print(r)
r = requests.get(url, headers=headers)
resp = r.json()
print(resp['settings']['signOn'])
For Example, you should take the Python script above and set this up for our Office 365 instance. You would get the following output:
import requests
url = "https://bitglass3.okta.com/api/v1/apps/0oa1jd6vv1jAaQQNg1d8"
headers = {'Authorization': 'SSWS 00vHkuHU25weVQAZK9ENeZEnfNZYEqlji1Rdf6Dt5N'}
r = requests.get(url, headers=headers)
resp = r.json()
print(resp['settings']['signOn'])
resp['settings']['signOn']['ssoAcsUrlOverride'] = 'https://portal.bitglass.com/sso/acsproxy/?bitglass_continue=https://login.microsoftonline.com/login.srf'
#resp['settings']['signOn']['ssoAcsUrlOverride'] = 'null'
p = requests.put(url, json=resp, headers=headers)
print(r)
r = requests.get(url, headers=headers)
resp = r.json()
print(resp['settings']['signOn'])
You should replace three distinct things:
- Replace
url = "<Okta App URL>" with url = "https://bitglass3.okta.com/api/v1/apps/0oa1jd6vv1jAaQQNg1d8"
- Replace
headers = {'Authorization': ' SSWS <Your Oauth Token>'} with headers = {'Authorization': 'SSWS 00vHkuHU25weVQAZK9ENeZEnfNZYEqlji1Rdf6Dt5N'}
- The ACS proxy URL remains the same. You will just need to insert your particular apps login URL after the
?bitglass_continue= part. So, you get:
resp['settings']['signOn']['ssoAcsUrlOverride'] = 'https://portal.bitglass.com/sso/acsproxy/?bitglass_continue=https://login.microsoftonline.com/login.srf'
-
After you have run the Python script, the ACS proxy field should be set. The final thing you will need to do is copy the Okta app cert over into the Forcepoint Data Security Cloud | SSE IdP setup and then set the app instance auth to Okta. If you have not
created Okta as an IdP object in Forcepoint Data Security Cloud | SSE, you can follow Okta:
Configuring Forcepoint Data Security Cloud | SSE as a SAML SP to add it. This will ensure that
Okta is associated with the application and that you send the proper cert (for example Okta sends a different cert than M365).
-
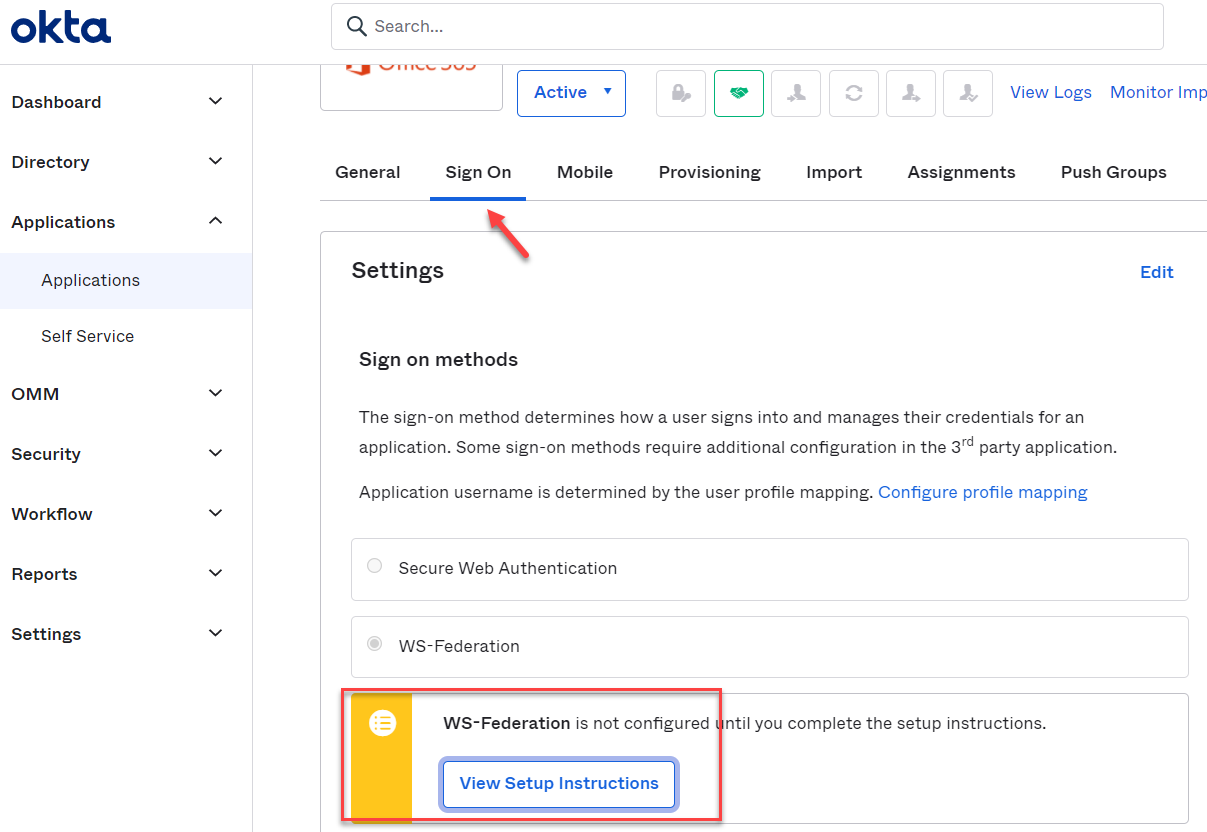
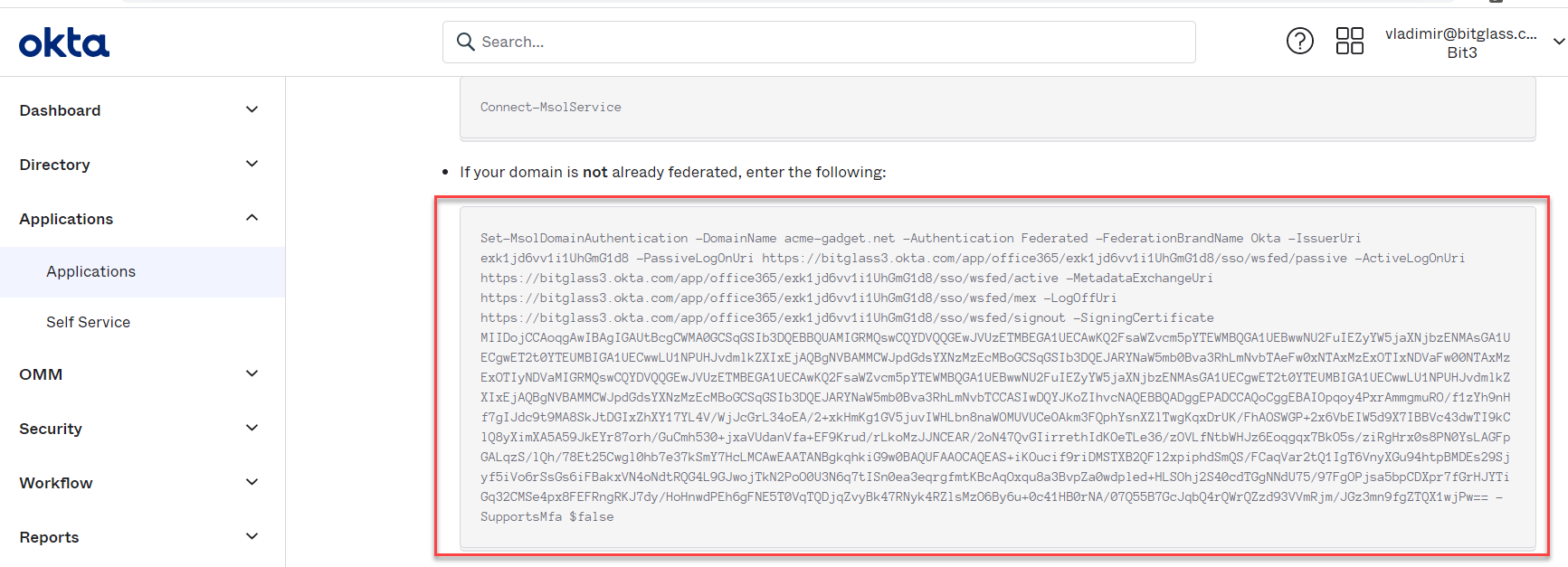
In your Okta admin portal, select the app and click on Sign On tab. Click Setup Instructions under the WS-Federation
card.
-
Copy the text from the not federated domain section and create a certificate.
-
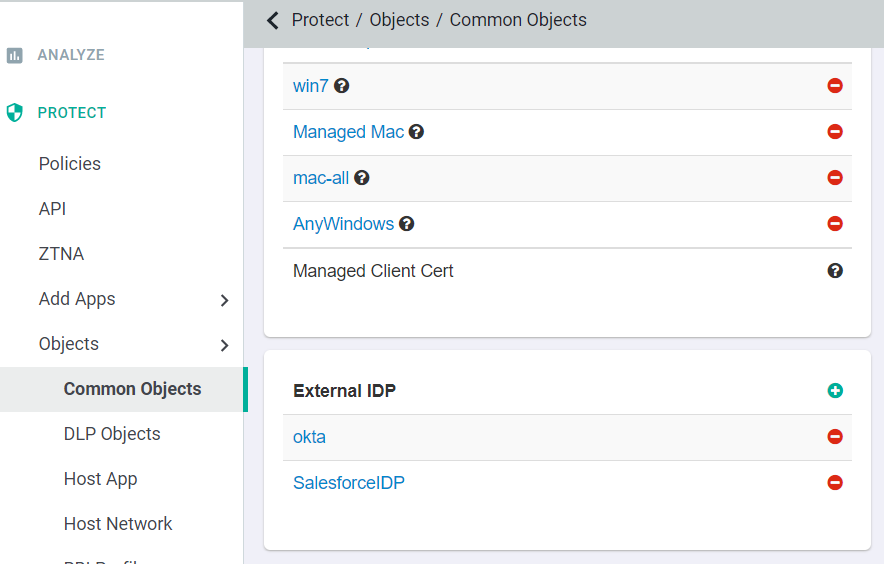
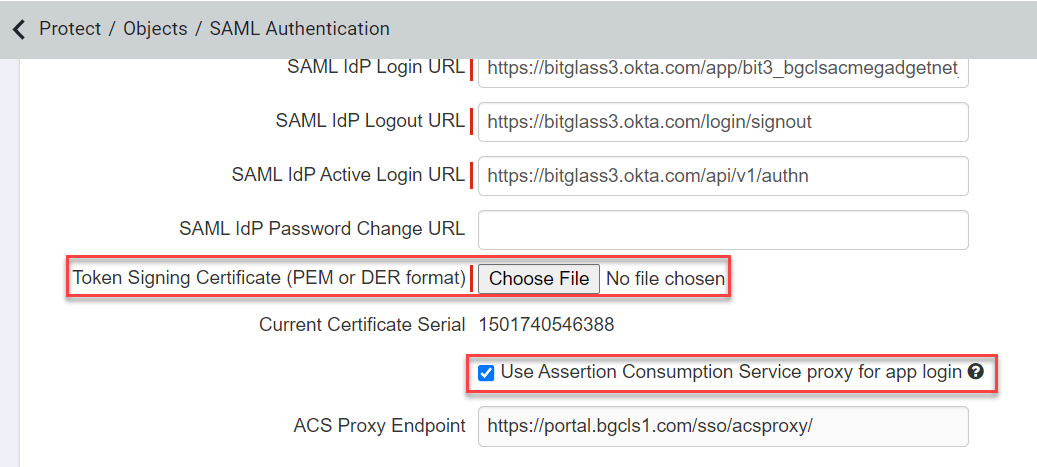
In a new window, login to the Forcepoint Data Security Cloud | SSE admin portal and navigate to and select the Okta IdP object you have already created. Upload the certificate that you just created in Token Signing Certificate (PEM or DER format).
Also, make sure you enable the checkbox for Use Assertion Consumption Service proxy for app login. Finally, click Save at the top to save your
changes.
-
Once done, you will also need to make sure that the authentication within the Forcepoint Data Security Cloud | SSE app instance setting is set to Okta. You can do this by navigating to the page and select the application in question you are setting up to ACS proxy. Once on the app settings page, click on the domain instance to open up the instance dialog window and
on the Authentication field, click the drop-down to select Okta.

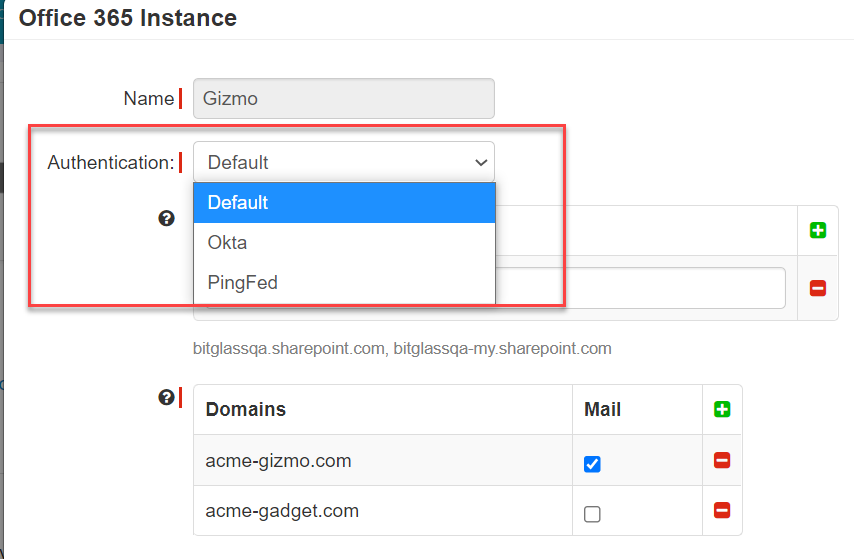
Note: This step helps in case the IdP sends different certs for different apps. For example, Okta sends a different cert for M365 (wsfed). This way it ensure that the IdP object is directly
associated with the app and will send the proper cert.