Configuring inline DLP for custom applications
For custom applications added to Forcepoint Data Security Cloud | SSE, there are some additional configuration steps inside of Forcepoint Data Security Cloud | SSE that might be required in order to ensure inline DLP will be applied correctly.
Follow the steps below to add the additional configuration steps as needed:
Download DLP configuration
For download DLP, Forcepoint Data Security Cloud | SSE inspects the Content-Disposition header for URLs that are related to file downloads which allows us to inspect the file and then apply DLP. Most applications set or provide this Content-Disposition header and no additional configuration is required. However, if you have added an application (whether an existing SaaS app or a custom app) and download DLP is not working it is likely because this Content-Disposition header is not being provided and you will need to input the search patterns designating which URLs are related to file-downloads.
The best way to figure out what these patters are is to open up your network diagnostics in your browser, record the traffic and then click in the application to initiate a download. Review the network traffic and input the URL calls used for the download. Doing this in Google Drive will result in a network capture that looks like this:
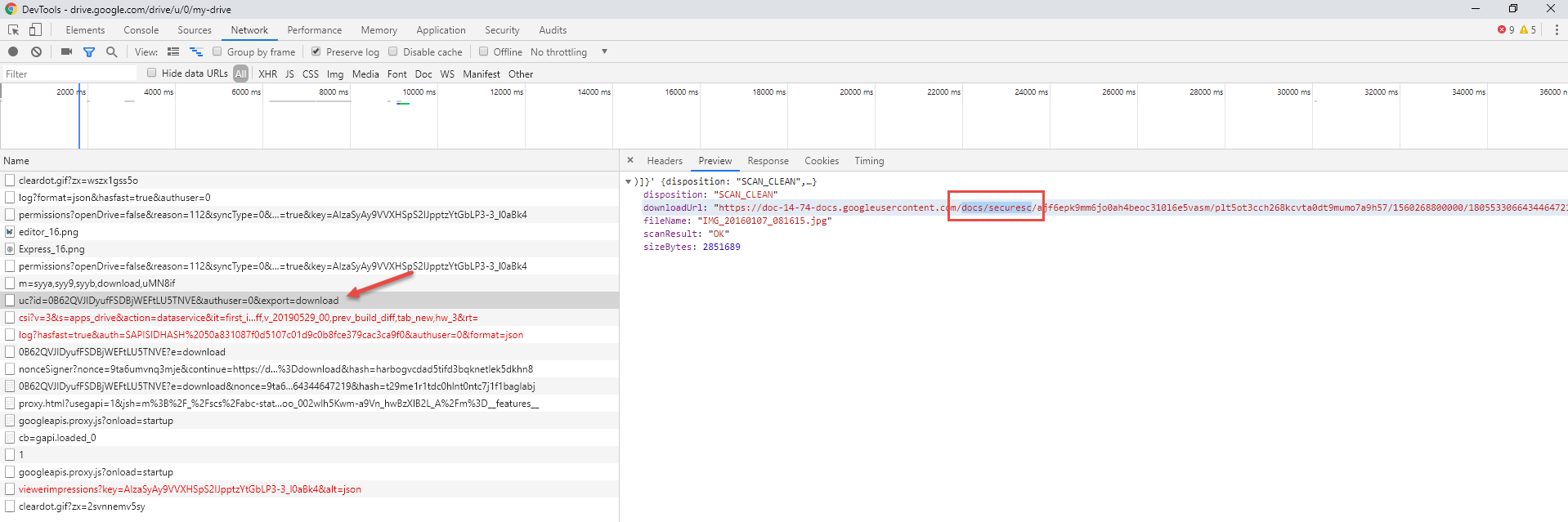
Click on the name of the URL call that specifies the download action and then view the downloadurl on the right side. We only need the specific URL pattern being used, in this case docs/securesc/. Once you have figured out which patterns you need you can add them to the Download DLP URLs box inputting each pattern on a separate line.
- /wp/downloads/
- /wp/\d+/files
- http://custom.com/wp/downloads/2013/image.png
- http://custom.co.uk/daily/wp/99123457/files/news.pdf
Upload DLP Configuration
While there is no specific area that requires configuration options for supporting upload DLP, admins must consider where the data is being stored and if that domain has been added under the additional app domains field in the app configuration dialog.
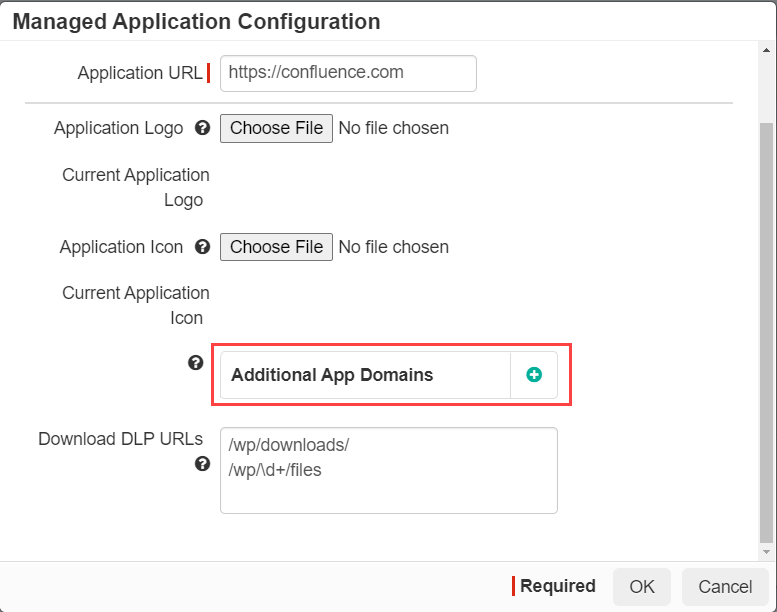
For most known SaaS apps, there isn't anything additional that will need to be added here if you already have all of the domains of that application added. However, for custom applications you have developed internally, the storage location for files might reside somewhere else (for example, S3 or another file storage app like box or dropbox, etc). If this is the case you will need to make sure those other application domains are added here in order for Forcepoint Data Security Cloud | SSE to recognize those domains as part of the custom application's request and support the proxying of that traffic.
If you have configured all of the proper domains but upload DLP is still not working it is likely because the data you are attempting to upload is not a supported content type.
- application/vnd.openxmlformats-officedocument
- multipart/form-data
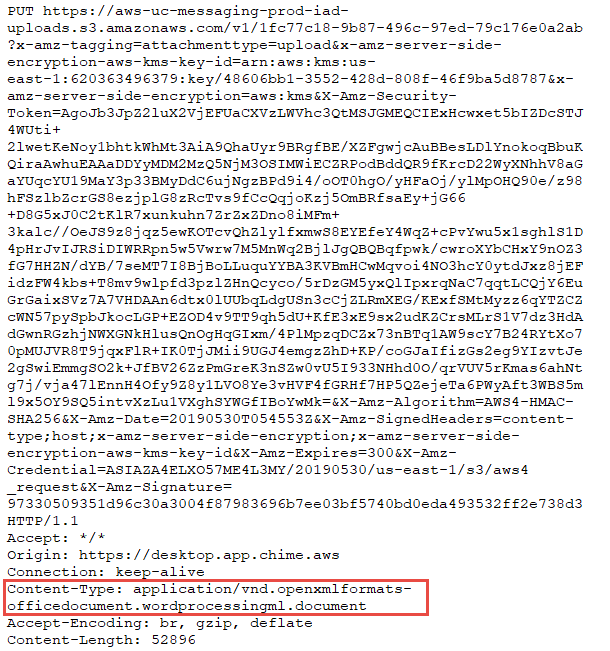
To learn what the content-type of your data is, do a network capture and attempt to upload data. Review the upload request and look for Content-type to see what it is.
DLP Actions
For applications added via the Any Licensed Application option, you will be able to apply inline DLP actions on both download and upload.
- Download Actions: Download actions are the same as other apps that are part of Forcepoint Data Security Cloud | SSE predefined list.
- Allow: Will allow the file to be downloaded and log the event for visibility purposes.
- Encrypt: Results in the downloaded file being encrypted with a user specific password. This password is defined on a per user basis and can be changed in their account profile.
- DRM-Readonly: Converts the file to a DRM'd html file that is readonly and cannot be edited.
- Block: Blocks the file from being downloaded, a block file message is downloaded instead.
- Deny: Will deny the download action outright instead of attempting to download a block message. This is useful for situations where you are trying to control things such as malware.
- Upload Actions: Upload actions can support the standard allow/block as well as encryption when possible.
- Allow: Will allow the file be uploaded and log the event for visibility purposes.
- Encrypt: This feature is available for custom applications that can support encryption. Files uploaded will be encrypted by Forcepoint Data Security Cloud | SSE during upload. If the application cannot handle/support a file being encrypted on upload, the encryption process will fail and the file will be uploaded without modification. In order to view/work on the file, the file must be downloaded through the Forcepoint Data Security Cloud | SSE proxy to be decrypted.
- Block: Will block the file from being uploaded, a block message is uploaded instead.
- Deny: Will deny the upload action outright instead of attempting to convert the file to a block message. This is useful for situations where you are trying to control things such as malware.