Configuring Admin portal policy
The Forcepoint Data Security Cloud | SSE Admin Portal tile allows you to manage user or group access to the Forcepoint Data Security Cloud | SSE Admin Portal itself. You can access the Admin Portal tile under the page.
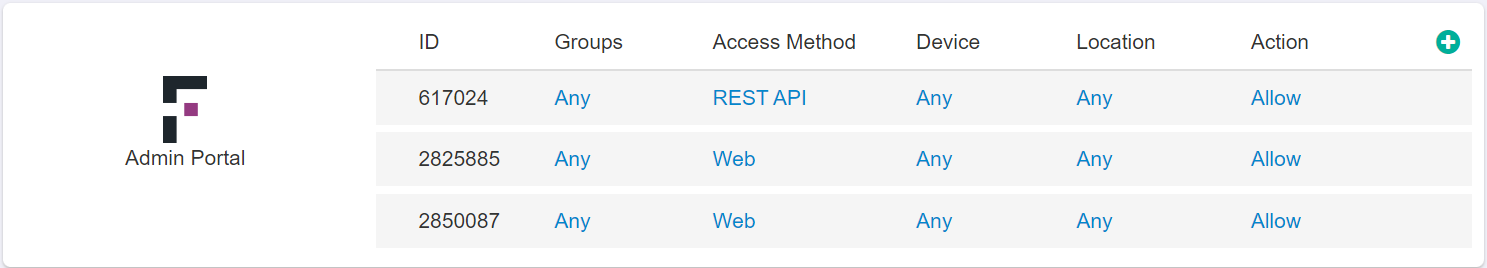
The Forcepoint Data Security Cloud | SSE Admin Portal tile is treated and handled in a similar manner to all other cloud apps. It is broken down into five columns.
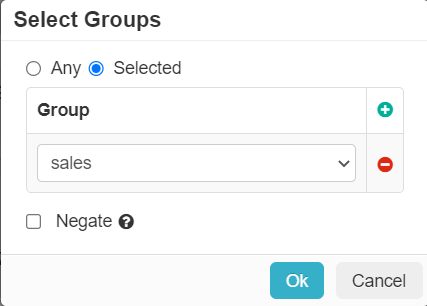
Groups
Locally defined groups or security groups and OUs pulled from active directory. You can add as many groups as are needed for the policy. You can also negate the group so that policy line applies to everyone except the group you selected.
- Specific User groups are not supported in the SWG Connection Policy currently when the Site Type is set to Explicit Proxy together with the Agent Override set to Chain to Explicit Proxy in the Agent Overrides tab. In such a case, the user Group must be set to ANY in the SWG Connection Policy.
- This restriction does not apply to Agentless Explicit Proxy use case and to other agent override options when the Site Type is set to Explicit Proxy, that is Do Not Override and Do Not Set PAC.
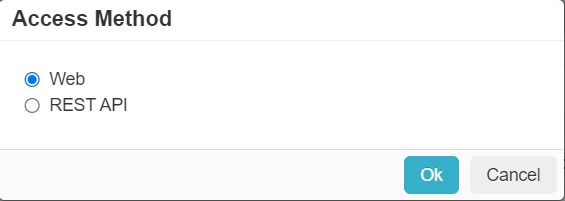
Access Method
There are only two ways to access the Forcepoint Data Security Cloud | SSE Admin Portal directly. Through the Web or through a REST API.
Device
The Device column allows you to set contextual access controls based on the users device (OS/user agent, managed vs unmanaged, and so on).
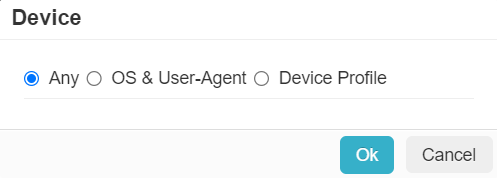
- OS & User-Agent: Allows you to match from a predefined set of common operating systems and/or User-Agent Strings.
- Device Profile: Allows you to match on Device Profiles which are managed under .
Location
The Location column allows you to restrict or control where a user is accessing the cloud application from (either geographic location or IP).
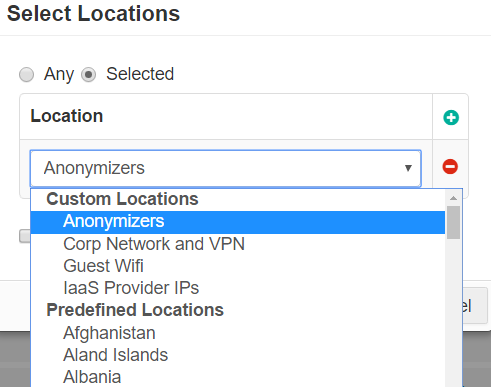
To use a location based policy for managed applications, the location object must contain the IP address of the Cloud-SWG datacenter. When the device is in the office, since traffic is tunneled to the Cloud-SWG, the Reverse Proxy sees the Cloud-SWG IP address and uses it to match the location configured in the managed app policy. Additionally, the location object should also contain other remote office locations that are also permitted.
- Custom Locations can be configured under . Custom locations also include predefined locations that are not based on countries (for example, Anonymizers and IaaS Provider IPs). These locations are managed and updated by Forcepoint Data Security Cloud | SSE.
- Predefined locations include a list of countries. Country match is done using a geo-IP lookup to match source IP address to country.
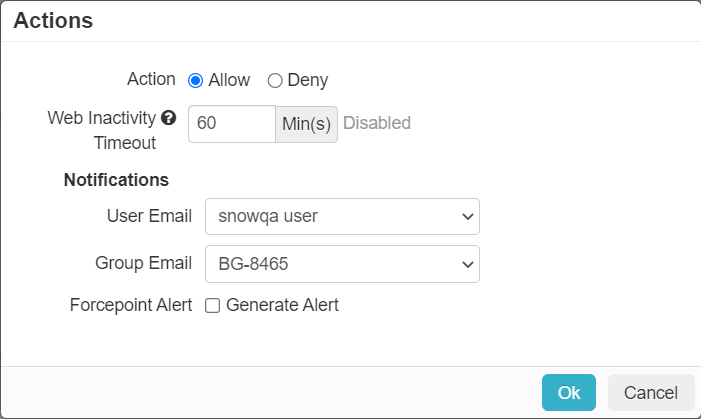
Action
There are no DLP policies to configure as there is no data being uploaded/downloaded or stored on the portal. Instead the Action column simply provides an option to Allow or Deny access, alert/notify groups/users, and a web inactivity timeout (option only available when Allow is selected).