Configuring proxy bypass destinations with firewall redirect
You can configure the cloud service to allow users to access some domains without policy enforcement. These are called proxy bypass destinations. Define proxy bypass destinations
in any of the following ways. (For more detailed instructions, see the Forcepoint Web Security Cloud Help).
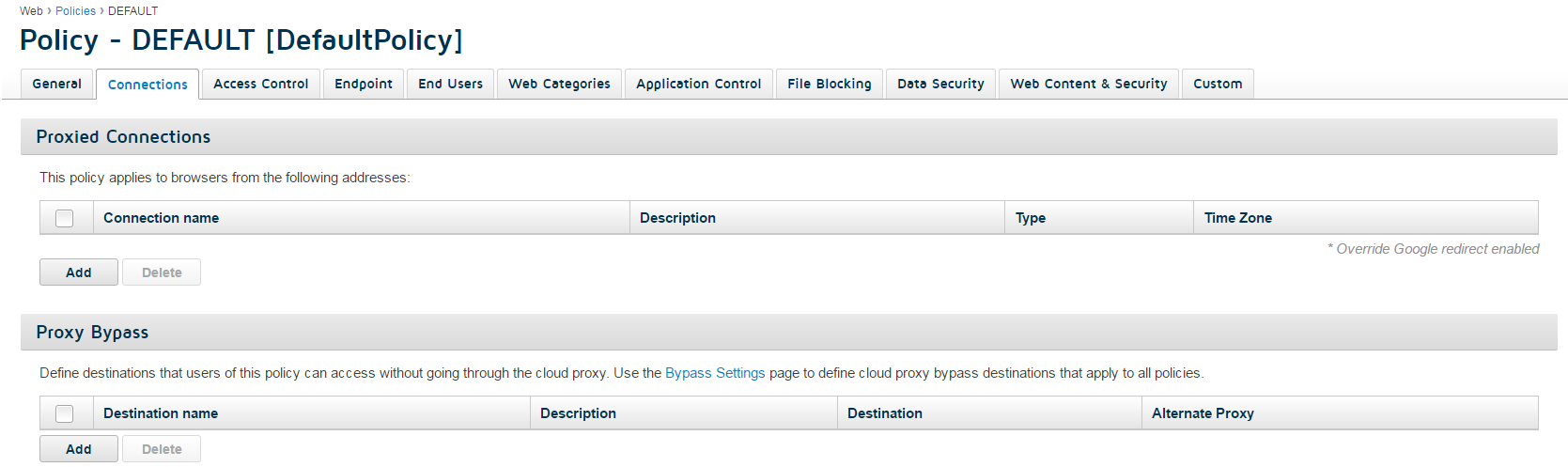
- To configure bypass destinations within individual policies:
- Navigate to and select a policy.
- Click the Connections tab.
- In the Proxy Bypass section, click Add.
These bypass destinations affect only users assigned to the specified policy.
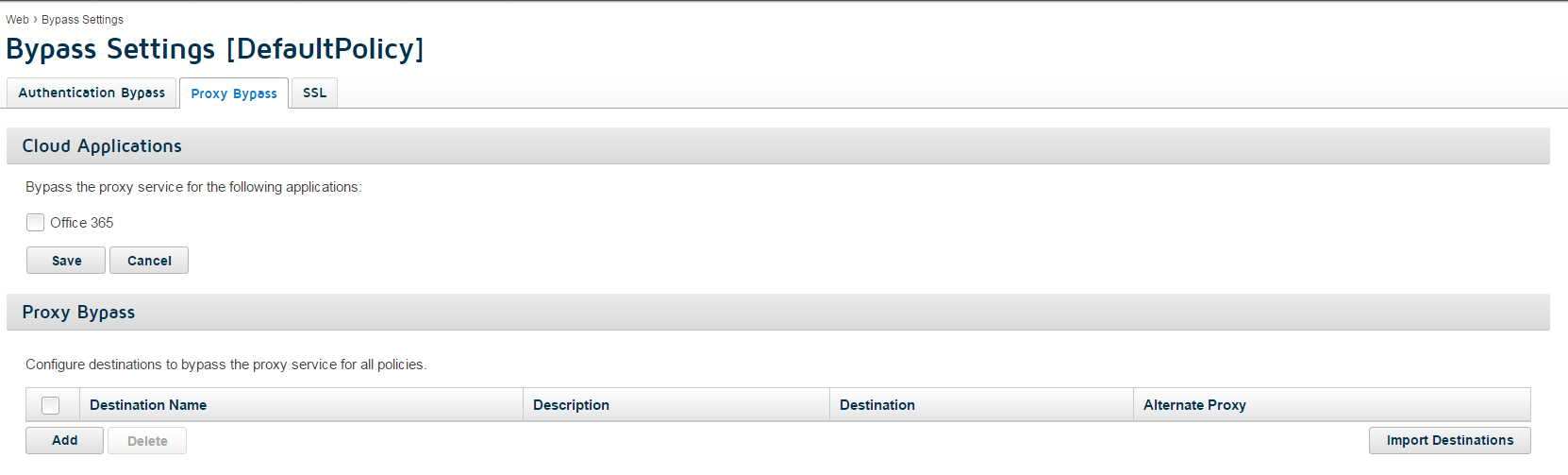
- To configure domains that will be bypassed at the account level:
- Navigate to .
- In the Proxy Bypass section, click Add.
These bypass destinations affect all end users in the account, regardless of which policy they are assigned.
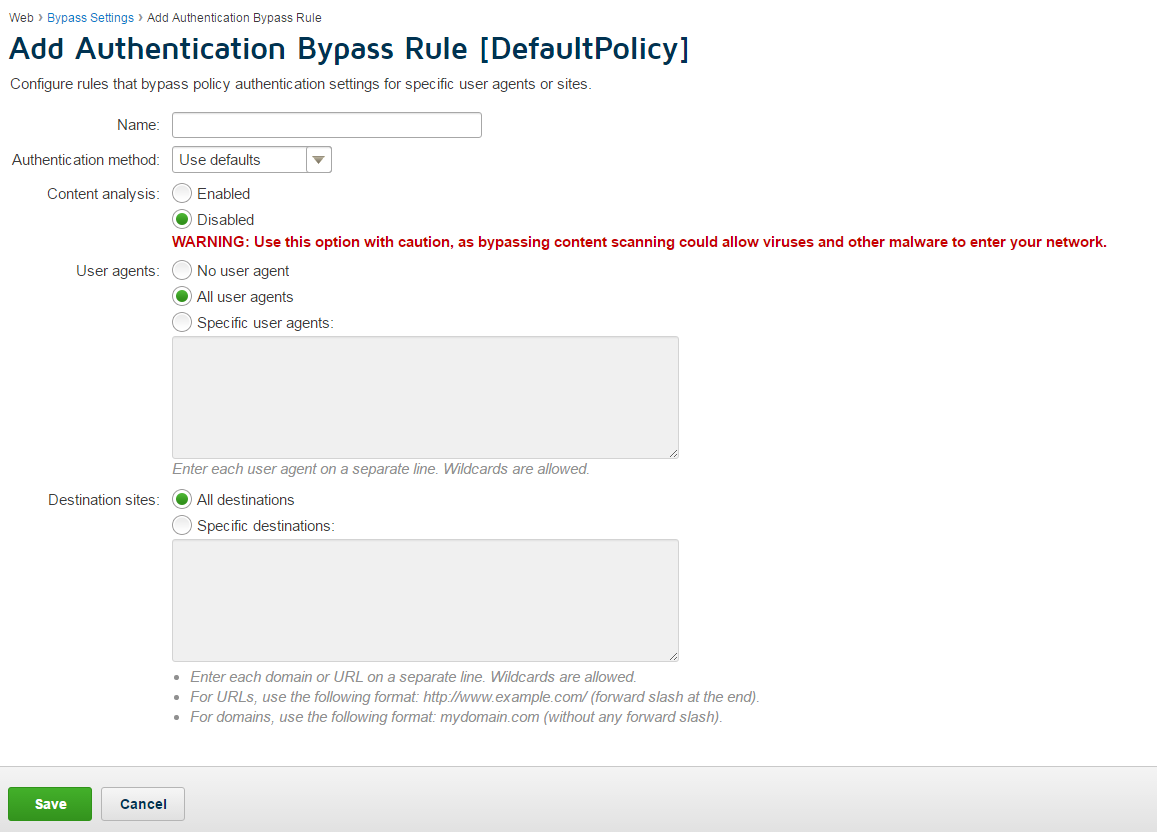
- To configure the domains via the “User Agent & Destinations” bypass list with content analysis disabled:
- Navigate to .
- In the section, click Add.Note: If you are using PAC files to direct traffic to the service, use this method if you do not want to add the bypassed domains to the policy PAC file.
In all of these cases, traffic is forwarded to the cloud service, but no policy enforcement occurs. The cloud service transparently forwards the traffic upstream. These transactions are
logged in reporting with a bypass action.
Note: Forcepoint Cloud Operations may block some domains at their discretion, if traffic to those domains is known to cause problems. If this
occurs, all traffic to these domains is blocked, and it is not possible to send this traffic through the cloud service, regardless of your bypass settings.