Understanding the reporting databases
Applies to:
- Forcepoint Web Security and Forcepoint URL Filtering, v8.5.x
- Forcepoint DLP, v8.5.1, v8.6.x, v8.7.x, v8.8.x, v8.9.x, v9.0, v10.x
- Forcepoint Email Security, v8.5.x
- Forcepoint appliances, v8.5.x
Each reporting database stores the logging data collected by a specific Forcepoint security solution: Forcepoint Web Security, Forcepoint URL Filtering, Forcepoint DLP, or Forcepoint Email Security.
- The web protection Log Database stores Internet and cloud application request data collected by Log Server, such as the source, destination, time, category, risk class, action (also
called disposition), bytes sent and received, and so on for use by web protection reporting tools.
Log Server receives information about Internet activity from Filtering Service and initially stores it locally:
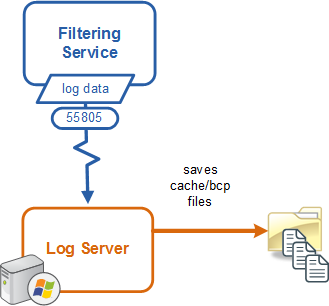
Whenever it is able, Log Server forwards the cache files to the Log Database, where the ETL job processes them into log records in a database partition:
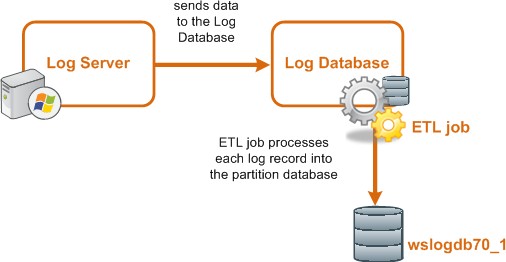
An end user who uses the Filtering Service has no direct or indirect influence over the database. Thus, although the log entry is stored in the Microsoft SQL Server database, the user did not direct its storage and cannot retrieve it.
Prior to v8.3, the only interface to the database itself is the Log Server, reporting services, and Forcepoint Security Manager. But from v8.3 onwards, the cloud app service also can insert the cloud app data to log database. Filtering Service and Content Gateway do not access the database, but instead send information via the Log Server.
- The Email Log Database stores records of email traffic and the associated analysis and disposition of that traffic. Forcepoint Email Security reporting uses this information to generate
dashboard status charts and email activity reports showing, for example, the size and volume of messages processed, message analysis results, and email source and destination.
Log and quarantine data are recorded as follows:
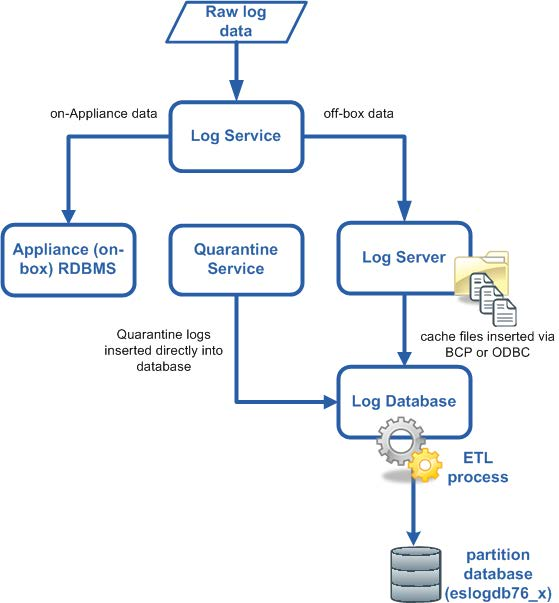
- Data Incident and Configuration Database stores information about email, web, and other traffic that resulted in data loss prevention (DLP) policy breaches, such as the source, destination, time, status, and severity of each breach. It also stores Forcepoint DLP policy configuration and system settings.
The reporting databases are all hosted by Microsoft SQL Server. They may be hosted by the same installation and instance, or by different installations or instances.
Although Microsoft SQL Server Express may be packaged with your software, most organizations should purchase Microsoft SQL Server Standard or Enterprise. (See Can I use SQL Server Express?, for guidance.)
As a best practice, during installation, connect Forcepoint software to a SQL Server instance on another machine. For testing purposes, or in very small networks, it is possible to install SQL Server Express on the Forcepoint management server. For more information, see Microsoft SQL Server deployment options.