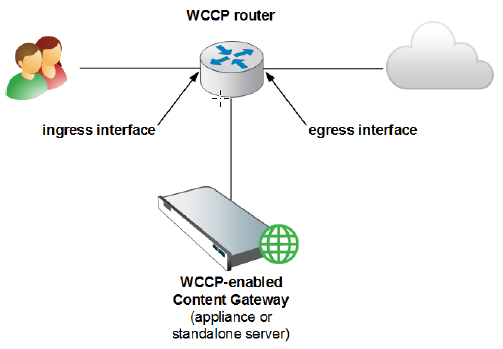
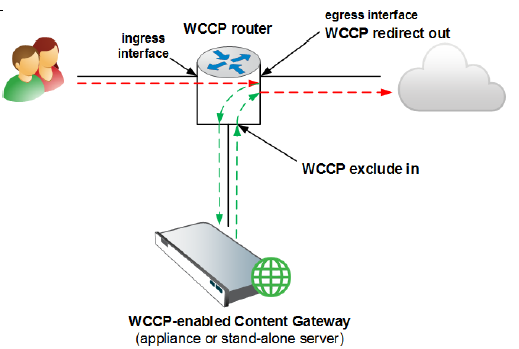
Note: Where your hardware and network topology support it, it is recommended that redirection be performed on the ingress interface (using the “redirect in” commands).
The following are examples. Be sure to substitute the service group IDs that you have established on your router(s).
First, select the interface to configure:
interface <type> <number>
Second, establish your redirection rules:
ip wccp <service group ID> redirect in
Examples for inbound redirection:
Run these commands for each protocol that you want to support, but only on the interfaces dedicated to inbound (ingress) traffic.
For example, to turn on redirection of HTTP destination port traffic, enter:
ip wccp 0 redirect in
To turn on redirection of HTTPS destination port traffic:
ip wccp 70 redirect in
To turn on redirection of FTP destination port traffic enter:
ip wccp 5 redirect in
To turn on redirection of HTTP source port traffic, which is required for IP spoofing, enter:
ip wccp 20 redirect in
Examples for outbound redirection:
Run these commands for each protocol that you want to support, but only on the interfaces dedicated to outbound (egress) traffic.
First, select the interface to configure:
interface <type> <number>
Second, establish your redirection rules:
ip wccp <service group ID> redirect out
For example, to turn on redirection for HTTP, enter:
ip wccp 0 redirect out
To turn on redirection for HTTPS:
ip wccp 70 redirect out
To turn on redirection for FTP enter:
ip wccp 5 redirect out