How can I make best use of the Incident List?
Steps
- Review the section in this paper titled The SSL Incident List. Follow the link to Managing Web HTTPS site access to review information for administrators in the Content Gateway Help system.
- The number of incidents automatically created by certificate verification failures depends on the CVE options enabled and peculiarities of the sites your users visit. For more about CVE options, see Validating certificates.
-
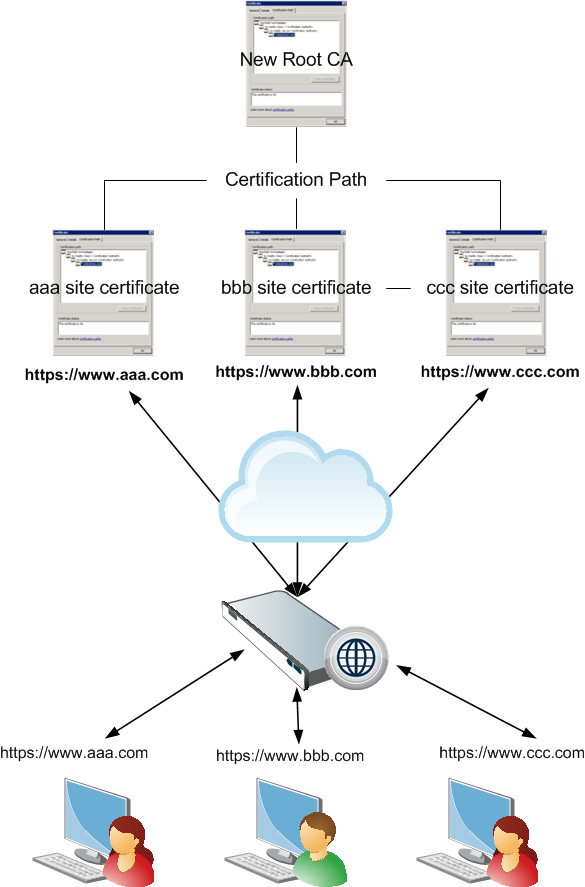
If you have several individual sites on the Incident List and some of those sites have certificates signed by the same new root CA, you could trust the CA that they have in common
and delete the individual site entries, thus keeping the Incident List as small as possible.
- Do not add “*.*” as “Action:Tunnel”. This has the effect of tunneling all HTTPS traffic, which subverts the purpose of SSL support and creates a lot of unnecessary overhead.