What’s in a policy?
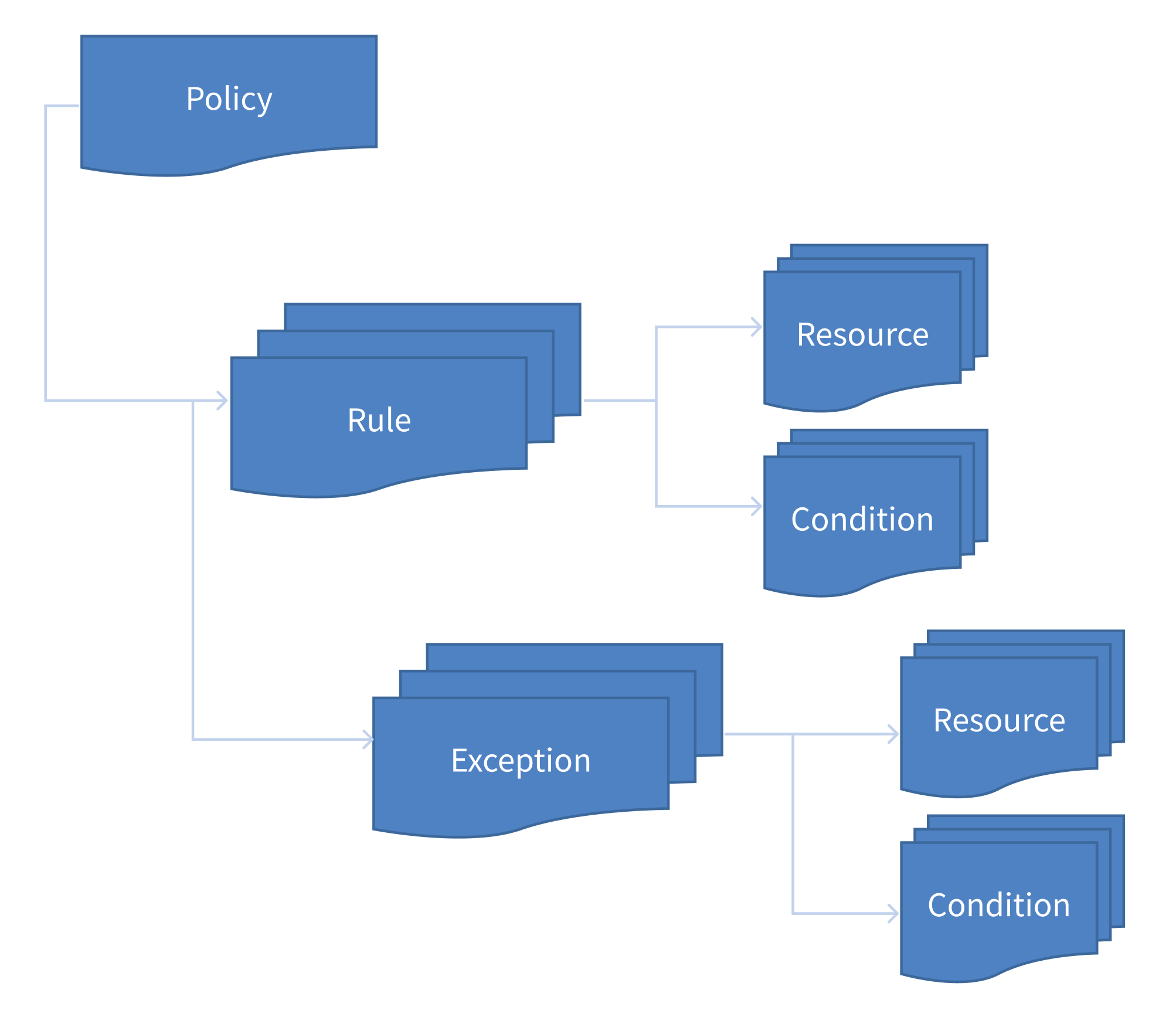
In Forcepoint DLP, policies contain rules, exceptions, conditions (defined by content classifiers), and resources. This is true of predefined and custom policies.
| Element | Description |
|---|---|
| Rules |
Provide the logic for the policy. They are the conditions that govern the behavior of the policy. When should something be blocked? When should managers be notified? Rules can apply to a single breach or to the accumulation of breaches over a period of time. Standard rules create incidents every time a rule is matched. Cumulative rules accumulate matches over time and create incidents when a threshold is met. This is known as drip DLP. |
| Exceptions |
Define the conditions that should be exempt from the rules. An exception is part of a rule and checked only when its rule is triggered. You cannot add exceptions to cumulative rules, and exceptions themselves cannot be cumulative. |
| Content classifiers | Describe the data to be governed. You can classify data by file properties, key phrases, dictionaries, scripts, database fingerprints, directory fingerprints, file fingerprints, regex patterns, or by providing positive examples for machine learning. |
| Resources | Describe the source and destination of the data you want to protect, the endpoint device or application that may be in use, and the remediation or action to take when a violation is discovered (such as block or notify). |
These components are the building blocks of a policy. When you create a policy from a policy template, it includes all rules, classifiers, sources, destinations, and actions. When you create a policy from scratch, wizards prompt you for such information.
Discovery policies also contain discovery tasks. These describe where to perform the discovery. On networks, this may include a file system, SharePoint directory, IBM Domino server, Box directory, database, Exchange server, or Outlook PST files. If you’re performing endpoint discovery, it includes the exact computers to scan.