Appendix A: Manually creating the MDM profile
You can manually create the MDM profile if you have issues importing the MDM profile provided by Forcepoint.
Steps
-
On the Computers tab, select Configuration Profiles, then click New.
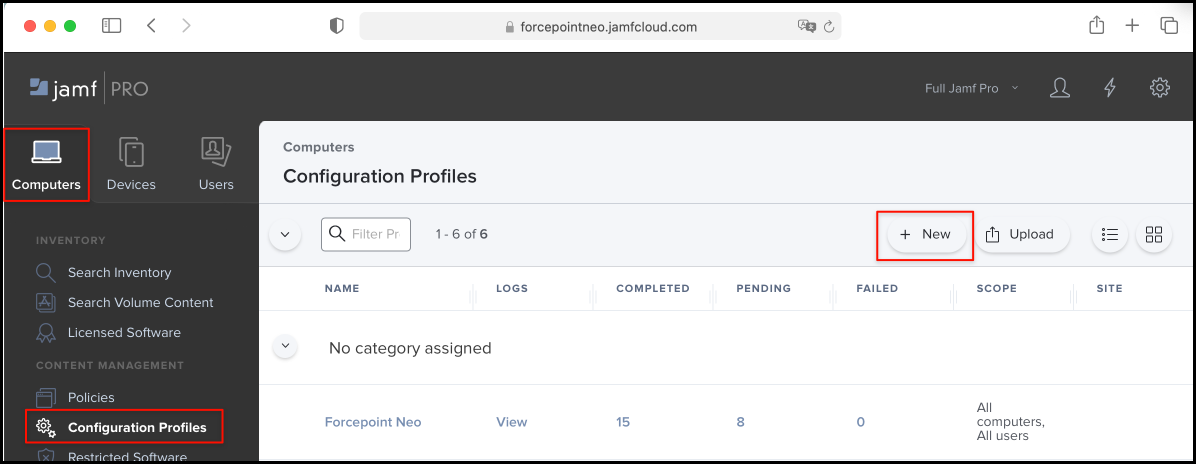
-
On the General tab, enter
Forcepoint Neoin the Name field. -
On the VPN tab, enter the following:
-
Connection Name:
Forcepoint Neo -
VPN Type:
VPN -
Connection type:
Custom SSL -
Identifier:
com.forcepoint.neo.ne-app -
Server:
Forcepoint Neo -
Provider Bundle Identifier:
com.forcepoint.neo.ne -
Provider Type:
App-proxy - Select the check box Prohibit users from disabling on-demand VPN settings
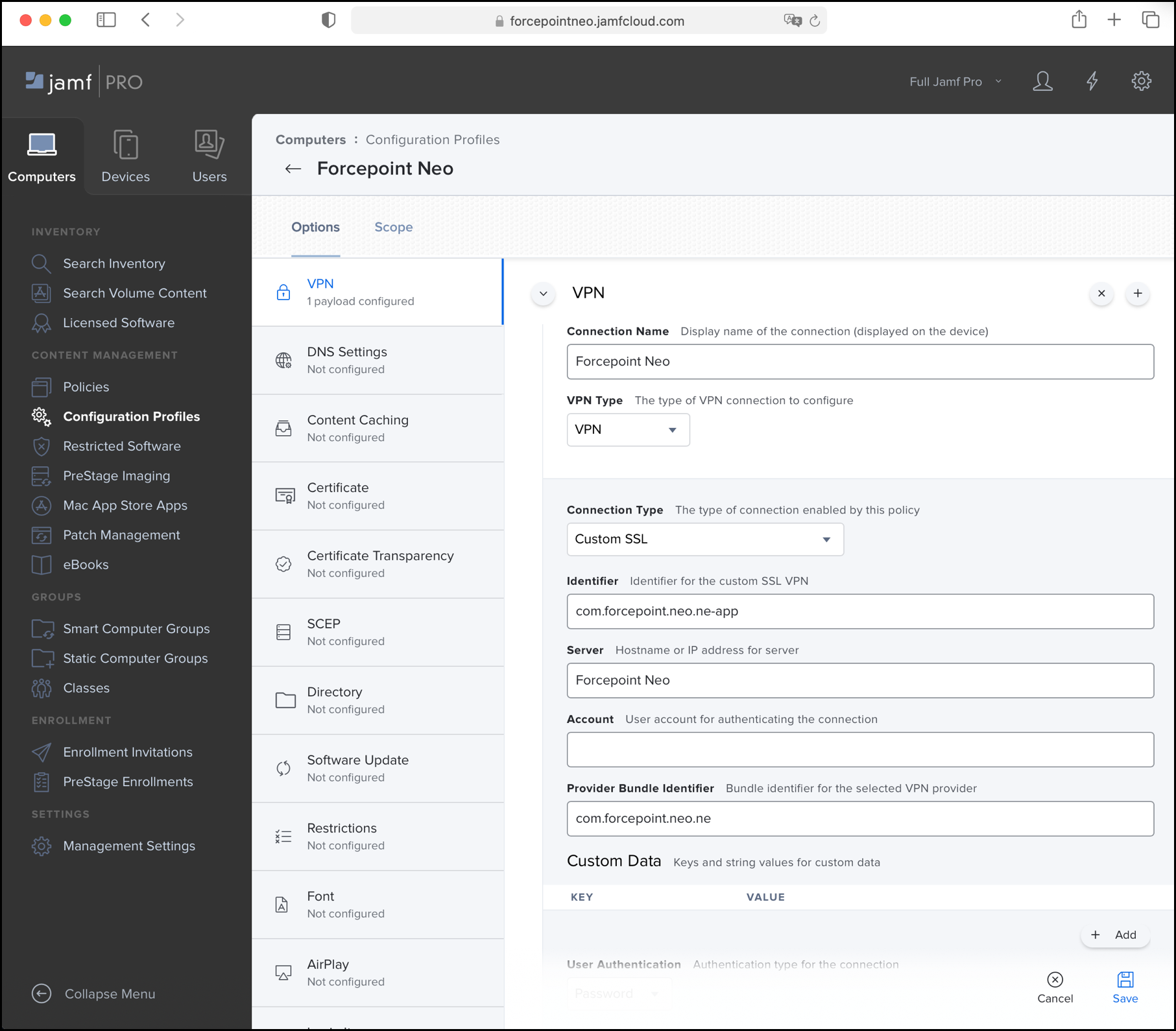
-
Connection Name:
-
On the Privacy Preferences Policy Control tab, define the following components:
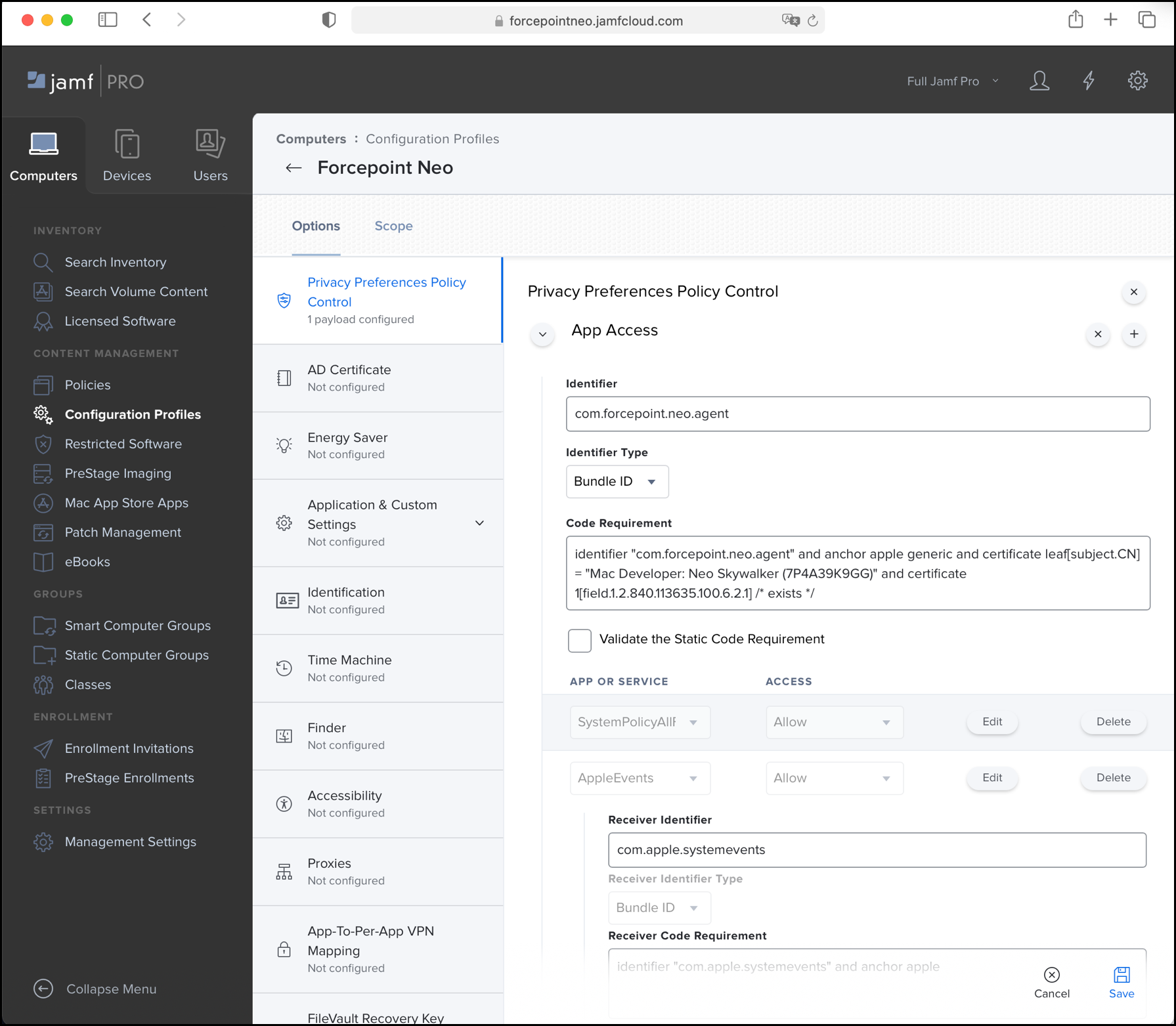
-
Enter the information for the first component.
- Identifier:
com.forcepoint.neo.agent - Identifier Type: Bundle ID
- Code Requirement:
identifier "com.forcepoint.neo.agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "4388XWHPGW" - From App or Service, select SystemPolicyAllFiles and from Access, select Allow
- From App or Service, select AppleEvents and from Access, select Allow
- Receiver Identifier:
com.apple.systemevents - Receiver Identifier Type: Bundle ID
- Receiver Code Requirement:
identifier "com.apple.systemevents" and anchor apple - From App or Service, select Accessibility, and from Access, select Allow
- Identifier:
-
Press the + button to add a new component, then enter the following information:
- Identifier:
com.forcepoint.neo.es - Identifier Type: Bundle ID
- Code Requirement:
identifier "com.forcepoint.neo.es" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "4388XWHPGW" - From App or Service, select SystemPolicyAllFiles, and from Access, select Allow
- Identifier:
-
Press the + button to add a new component, then enter the following information:
- Identifier:
/Library/Application Support/Forcepoint/Neo/EP/bin/fpneoprotectiond - Identifier Type: Path
- Code Requirement:
identifier "com.forcepoint.neo.protectiond" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "4388XWHPGW" - From App or Service, select SystemPolicyAllFiles, and from Access, select Allow
- Identifier:
-
Press the + button to add a new component, then enter the following information:
- Identifier:
/Library/PrivilegedHelperTools/com.forcepoint.neo.privilege-helper - Identifier Type: Path
- Code Requirement:
identifier "com.forcepoint.neo.privilege-helper" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "4388XWHPGW" - From App or Service, select SystemPolicyAllFiles, and from Access, select Allow
- Identifier:
-
Enter the information for the first component.
-
On the Certificate tab, define the following components:
- Under Certificate Name, enter Forcepoint Cloud CA.
- Upload the Forcepoint Cloud CA.cer file.
- Select Allow all apps access.
- Make sure Allow export from keychain is not selected.
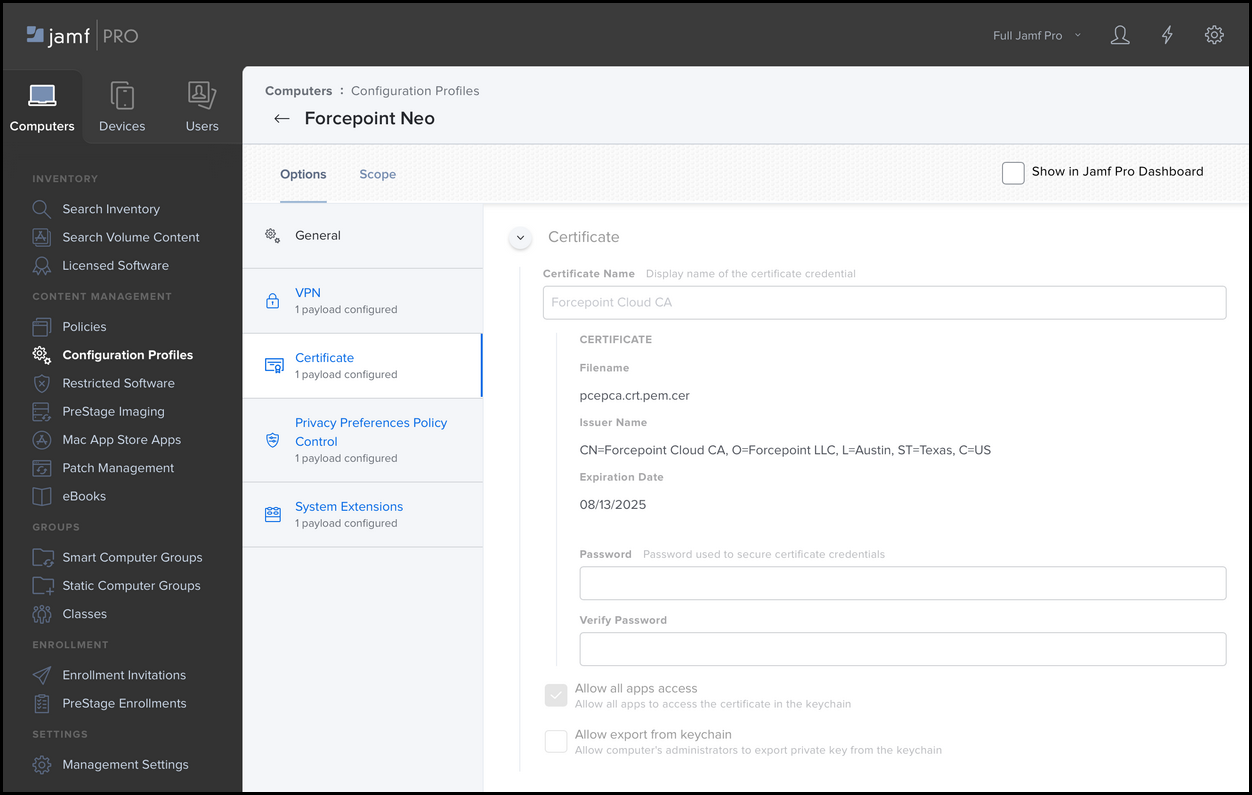
- Click Save.
-
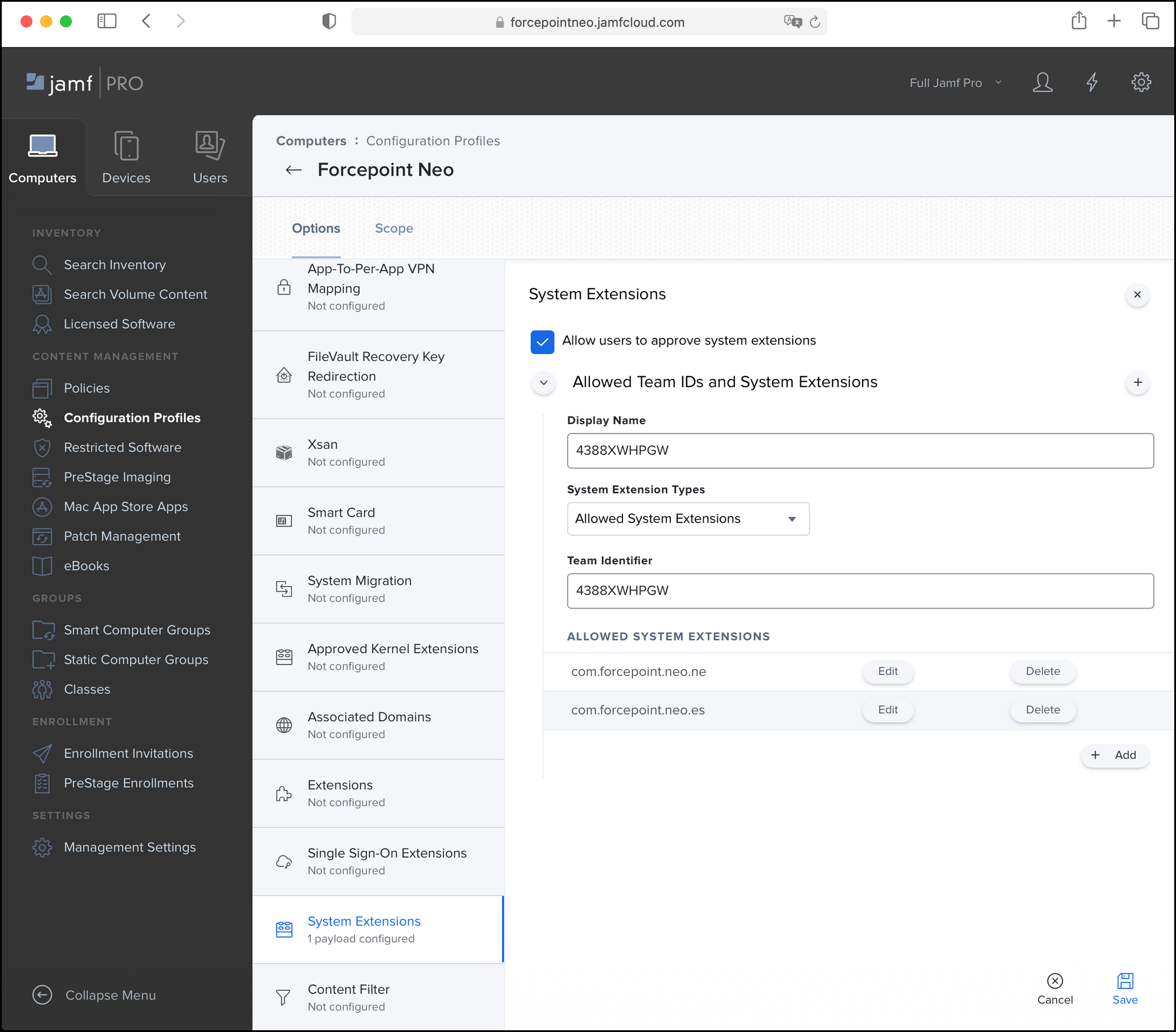
On the System Extensions tab, enter the following:
- Select the check box Allow users to approve system extensions
-
Display Name:
4388XWHPGW - From System Extension Types, select Allowed System Extensions
-
Team Identifier:
4388XWHPGW -
Allowed System Extensions:
com.forcepoint.neo.ne,com.forcepoint.neo.es
-
On the Computers tab, select Configuration Profiles, then click New.

-
On the General tab, enter
Forcepoint Neo NC Root CAin the Name field. -
On the Certificate tab, define the following components:
- Under Certificate Name, enter Forcepoint Neo NC Root CA.
- Upload the Forcepoint Neo NC Root CA.cer file.
- Select Allow all apps access.
- Make sure Allow export from keychain is not selected.
