Configure spoofed email filter analysis
Steps
-
From the section Filter Properties, mark the check box Sender address comparison.
Selection is enabled by default.
-
Mark the check box for one or more sender address conditions:
- Verify that the From: address matches the envelope sender address
This setting is enabled by default.
- Verify that the From: address matches the Reply-To: address
- Verify that the envelope sender address matches the Reply-To: address
This setting is enabled by default.
Note:When an envelope sender has been changed as a result of an address rewriting rule (Settings > Inbound/ Outbound > Address Rewriting), the spoofed email filter uses the original envelope sender address rather than the rewritten address for SPF analysis.
For other checks like header comparison and bypass conditions, the rewritten envelope sender is used.
- Verify that the From: address matches the envelope sender address
-
From the bottom of the section Filter Properties, click Advanced.
The Advanced settings display. Advanced options for sender authentication analysis allow the configuration of filter conditions using combinations of SPF, DKIM, and SIDF analysis results.
-
Mark the check box Sender authentication analysis.
Selection enables the use of one or more filter conditions.
-
Mark the check boxes for one or more conditions: Default Condition 1 or Default Condition 2.
Default condition sets include the following (operator between SPF and SKIM results is AND):
Condition Name SPF Result DKIM Result Sender ID Validation Default Condition 1 Fail or SoftFail Fail or Invalid or
TempError
Enabled Default Condition 2 PermError or TempError or None or Neutral Fail Enabled For Default Condition 1, the filter is triggered if:
- The SPF result is either Fail or SoftFail AND the DKIM result is Fail, Invalid, or TempError. The operator between SPF results and sender ID validation is OR.
For Default Condition 2, the filter is triggered if:
- The SPF result is PermError, TempError, None, or Neutral AND the DKIM result is Fail. The operator between SPF results and sender ID validation is
OR.
The SPF results are defined as follows:
- Fail: The domain owner’s SPF record does not authorize the sender host machine to send email for the domain.
- SoftFail: The domain owner’s SPF record allows the sender host machine to send email for this domain, even though the host is not explicitly authorized to do so.
- Neutral: The domain owner’s SPF record makes no statement as to whether the sender host machine is authorized to send email for the domain.
- None: The lack of definitive SPF information prevents an SPF check (e.g., an SPF record does not exist).
- PermError: A permanent error occurs (e.g., the SPF record has an invalid format).
- TempError: A transient error occurs (e.g., a DNS timeout).
The following graphic summarizes the relationships among the spoofed email filter options:
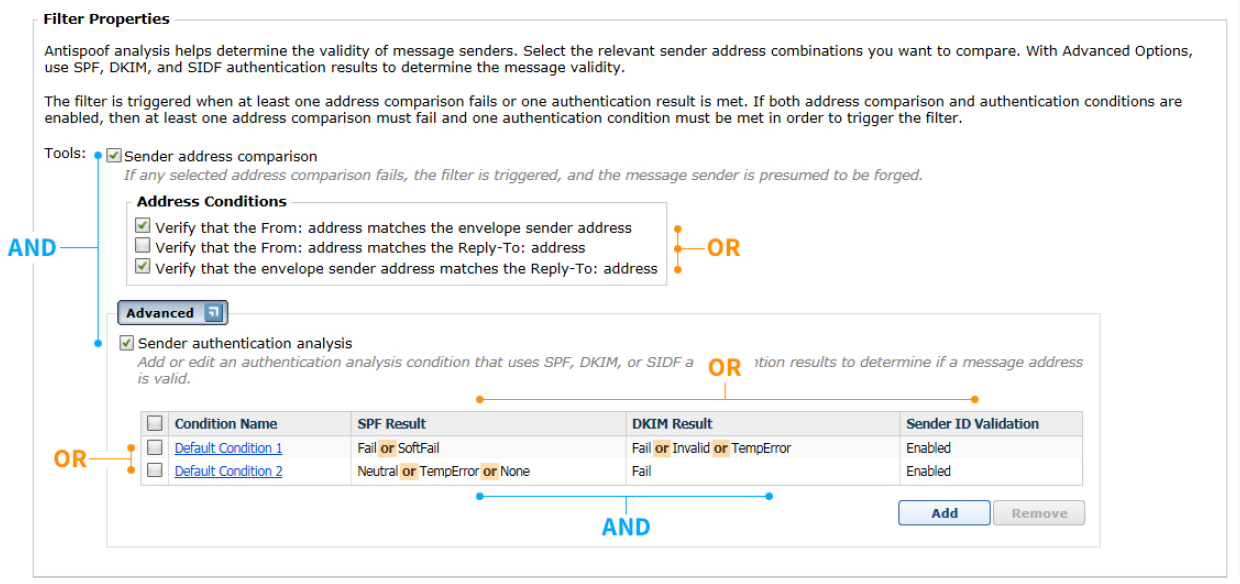
If both sender address comparison and sender authentication condition tools are enabled, then at least one address comparison must fail and one authentication condition must be met to trigger the filter.
- (Optional) Select a condition name to edit an existing condition, or select Add to create a new set of conditions.
-
Configure additional filter settings and click OK.
The spoofed email filter settings are saved.