Accessing Forcepoint Remote Browser Isolation application
Forcepoint Remote Browser Isolation (Forcepoint RBI) neutralizes security threats by isolating web traffic and any web threats from endpoint before they occur. By fully isolating web browser traffic, Forcepoint RBI creates a zero-trust environment that delivers a seamless user experience and eliminates most infections and compromises.
Internet browsing is a major threat carrier that can send unchecked active malicious codes to a user's endpoint machine. Forcepoint RBI prevents these threats by transferring user requests from the local browser to a disposable browser that performs fetch, execute, and render functions remotely. With Forcepoint RBI, active code is never sent to the protected endpoint machines. All web-based instructions are run in an isolated, purposely built virtual machine that removes computer code that could attack the protected endpoint machines.
You can access the Forcepoint RBI application only from the waffle switcher of Forcepoint Data Security Cloud | SSE only if your tenant is assigned and licensed for the Forcepoint RBI application.
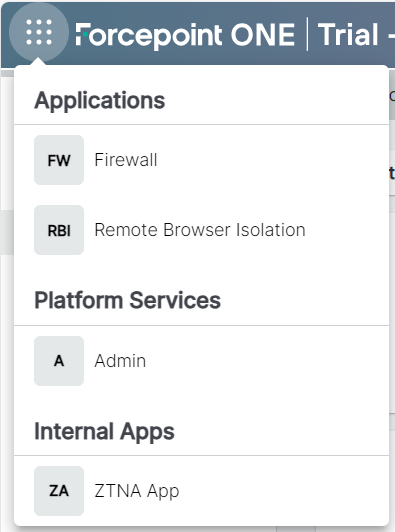
Upon clicking on the Remote Browser Isolation option, you will be taken to the System Dashboard page in the Forcepoint RBI application.
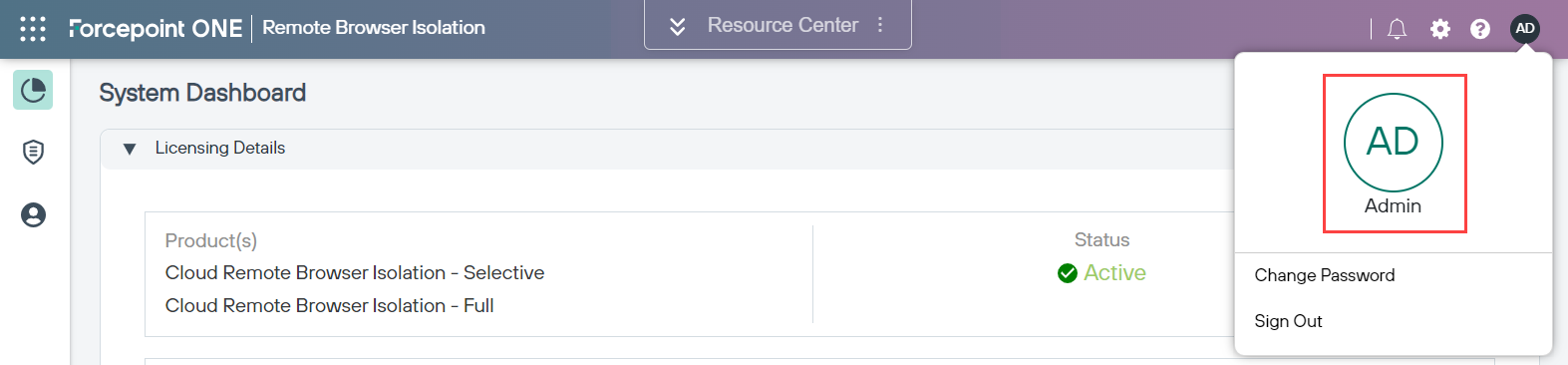
You can verify that the user logged in on Forcepoint RBI application is the same user as the one who clicks the Remote Browser Isolation option. This can be verified by checking the user logged in on the top right of the Forcepoint RBI application.
To know about the Forcepoint RBI application, refer to Forcepoint Remote Browser Isolation Online Help.