A Site represents a corporate location from which traffic will originate.
To create a new corporate Site with explicit proxy, follow the steps below:
Steps
-
Navigate to .
-
On the Sites page, click the green plus icon.
-
On the General tab:
-
Enter a unique Name of the Site.
-
Select the appropriate TimeZone of the corporate IP location.
-
Enter Description for the Site.
-
Select the Explicit Proxy option as the Type of the site.
Note:
- The Type cannot be changed once a Site is created. You can delete and create new site with correct Type.
- Based on the Type selected, available options under the Agent Overrides tab vary.
-
Enter the Public IP address of the site.
Forcepoint Data Security Cloud | SSE validates the IP address to make sure that the value is actually an IP address and is not a duplicate
of another site with same IP address that is already created.
-
Set the Identify Coordinates to Automatic to identify the location of the site based on entered IP address when you click
Detect Location.
The Location field displays the location name of the entered IP address to which your web content will be localized.
-
If Forcepoint Data Security Cloud | SSE is unable to identify the correct location or did not display the location of the entered IP address, then:
- Set the Identify Coordinates to Manual.
- Select the applicable Localization Country to which your web content should be localized.
Cloud SWG uses an egress IP address corresponding
to the Localization Country selected to send proxied traffic to its destination. If the selected localization country is not available,
the country of the Cloud SWG datacenter processing the traffic will be used instead. To know about the supported localization countries list, refer to Cloud SWG vPoP IP
addresses.
Note: For existing Sites, where the Localization Country was not available for selection,
is set so that you can select Localization Country later.
-
Ignore the Subnets tab as there is no visibility into internal subnets. All traffic is received from the Site’s Public IP entered on
the General tab and the user is tracked using cookies.
When creating SWG policies, you must set Traffic Type to Any.
-
On the Agent Overrides tab, define what should the SmartEdge agent do when it arrives at a site (office location) that has explicit proxy configured.
Note: If Set PAC is unchecked on the page or on the page, then the user device with the SmartEdge agent will ignore the Agent Override setting and will not set the system proxy.
From the Agent Override drop-down, select the desired behavior of the SmartEdge agent 2.1.0 or latest version when it is at the
site:
- Do not override (default) - Selecting the Do not override option enables the SmartEdge agent to operate as
it does at remote location. To make sure the SmartEdge agent filters the web traffic correctly, you should enable access to port 80 and 443 to the entire internet.
- Do not set PAC - Selecting the Do not set PAC option disables the SmartEdge agent from setting the PAC
when at the site so that the Admin can setup their own PAC file using other mechanisms.
-
Chain to Explicit Proxy - Selecting the Chain to Explicit Proxy option enables the SmartEdge agent to enforce SWG policies
for filtering and to forward traffic to the Cloud SWG Explicit Proxy. The Cloud SWG Explicit Proxy recognizes that the traffic is from the agent and lets the traffic
pass through without enforcing the SWG Content policy for second time. Note that the SWG connection policy is still applied.
You should select this option when you want to interoperate the SmartEdge agent with the Cloud SWG Explicit Proxy and do not want to open up port 80 and 443 to the
entire internet
When access to outbound IPs on port 80 and 443 is prohibited (that is you want to only allow access to specific IPs, not the entire internet), access to the following
needs to be allowed through the firewall:
Note:
- For the older versions of SmartEdge agent (previous to 2.1.0), the SmartEdge agent will behave as if Agent Override is set to Do not
override irrespective of what behavior you have selected.
- Available options vary based on the Type selected on the General tab.
Attention: When installing the SmartEdge agent at an explicit proxy site with Agent Override set to
Chain to Explicit Proxy, ensure that IaaS Provider IPs is not blocked in the login policy. Otherwise, the end-user
will not be able to log into the SmartEdge agent.
-
To configure a site with selected information, click OK.
As soon as the Site is created, the status of Site will be Configuring. After some time, the status of the Site gets changes to
Provisioned or Failed.
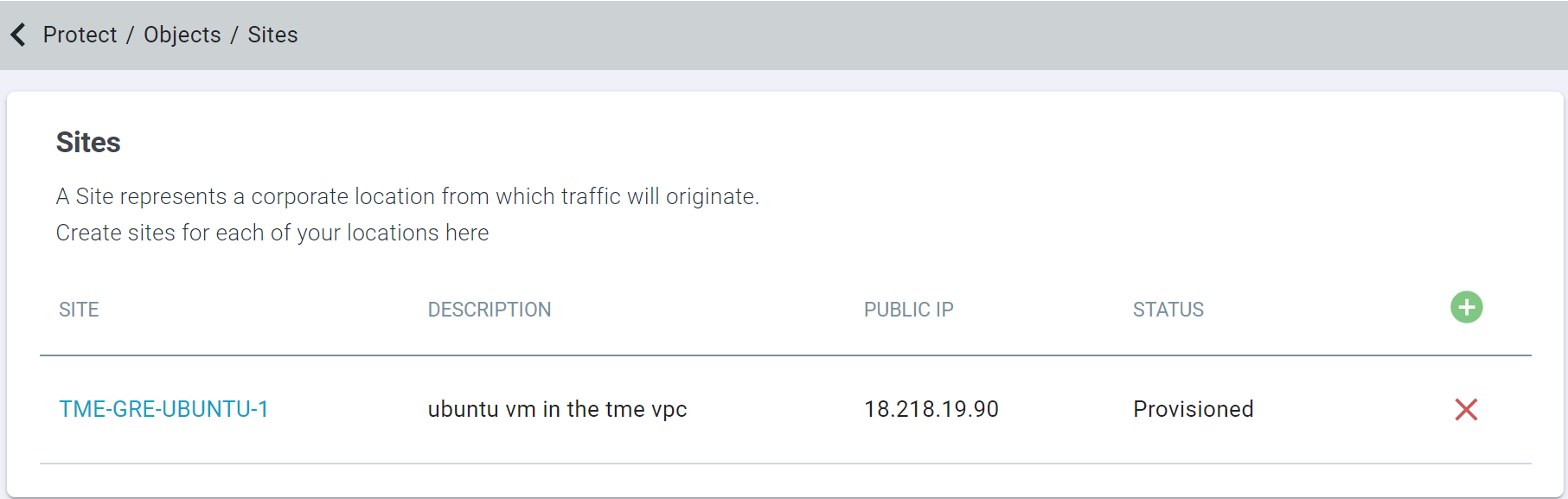
Result
Note:
- The first site on your tenant will be available in all regions after 10 minutes for the agent's Chain to Explicit Proxy feature to work.
- If you uninstall the SmartEdge Agent from a user device of the first tenant and install to a user device of a new tenant, then the agent's Chain to Explicit
Proxy feature will be available only after 40 minutes. To reduce this waiting period, follow the recommended steps:
- Uninstall the SmartEdge Agent from a user device of Company A.
- Remove the SmartEdge Agent associated with Company A's Forcepoint Data Security Cloud | SSE.
- Wait at least 11 minutes.
- Install the SmartEdge Agent on a user device of Company B.
When a user access website from the branch office where Cloud SWG Explicit proxy is configured, then web traffic is forwarded to Cloud SWG Explicit Proxy. The Cloud SWG Explicit Proxy
filters the web traffic as per the SWG policies configured by their Admin. If website is not blocked by SWG policies, then the Cloud SWG Explicit Proxy sends the request to internet on
behalf of end user device.
The
Web and
Web DLP logs are generated whenever web traffic from branch office is received to Cloud SWG. The
Connection field under the
Source section of the
Web and
Web DLP logs displays
connection type on which the transaction was received over:
- For Cloud SWG Explicit Proxy traffic - Explicit Proxy
- For Cloud SWG Transparent Proxy traffic - IPsec or GRE


