Introduction
Forcepoint Mobile facilitates productivity by delivering secure web access to corporate resources while effectively protecting mobile devices from web threats. This solution enables organizations to implement the same robust security measures on mobile devices as they do on laptops and desktops. It is compatible with both iOS and iPadOS devices.
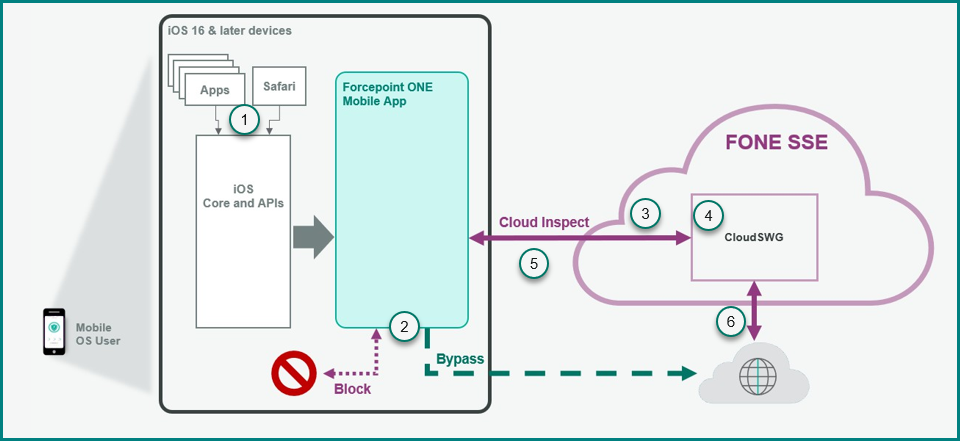
The diagram above depicts a typical data flow when a user accesses web content from a mobile device with the Forcepoint Mobile solution running.
- After successfully logging into the Forcepoint Mobile solution, users can access applications or browse the internet normally.
- Depending on the configuration set by the administrator, the Forcepoint Mobile solution may bypass or block specific traffic on the device.
- The Forcepoint Mobile solution redirects application or URL traffic to the Forcepoint ONE service hosted in the cloud.
- The Forcepoint Cloud SWG service analyzes web traffic and enforces the same security policies configured for all other endpoints based on the
identity of the user. Note: The Forcepoint Mobile solution uses the same policy for traffic as other endpoints configured on the Forcepoint ONE SSE portal. However, the location parameter on these policies does not apply to mobile traffic. You can create or modify policies by navigating to the . For more details about the policies, see the Configuring SWG policies section from Forcepoint ONE SSE Deployment Guide.
- If traffic is blocked, the cloud service displays a block page to the user.
- If the request is allowed, the solution then directs the request to the destination web server.