Cloud Security Gateway bypass settings direct traffic for specific domains to an alternative service using an entry in the PAC file used by endpoint for
traffic steering. Private Access uses this capability to recognize traffic for your internal applications and to direct it to the appropriate Private Access service edge.
For each internal application that your
Cloud Security Gateway users will need to access remotely, create a bypass destination that forwards traffic
destined for the application's external FQDN to the appropriate Private Access service edge, using the alternate proxy setting.
Note: You can add bypass settings at the account or the
policy level in the Cloud Security Gateway portal. For ease of management, Forcepoint recommends using
account-level bypasses, as described below.
Steps
-
Sign in to the Cloud Security Gateway portal.
-
Go to .
-
Click the Proxy Bypass tab.
-
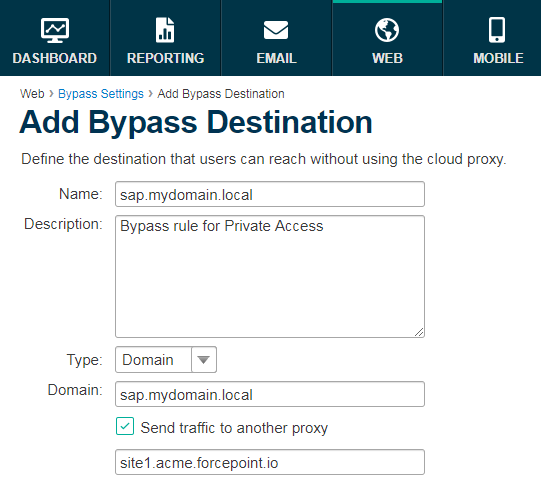
In the Proxy Bypass list, click Add.
-
Give the entry a name and an optional description, for example the name of the internal application. We recommend you use the name of the private application, as defined in the
Private Access management portal.
-
Set the Type drop-down menu to Domain.
-
In the Domain box, add the external FQDN for the private application, as defined in the Private Access management portal.
The External FQDN is found in the Private Access management portal, under . Click the name of the private application in the list to view its details.
-
Check Send traffic to another proxy.
-
In the box that appears, enter the service edge address for the private application, as given in the Private Access management portal.
The Service edge address is found in the Private Access management portal, under . Click the name of the private application in the list to view its details.
-
Click Submit.
Next steps
Repeat this process for each private application defined in the Private Access management portal, which Cloud Security Gateway users will need to access remotely.
Important:
You must add a bypass rule for each application using its FQDN, even if multiple applications share the same parent domain.
If you are using SAML authentication, add a bypass destination for your SAML authentication private application.
Note: Bypass destinations can take up to 10 minutes to be reflected in the PAC file.
For more information, see Adding and importing sites that bypass the proxy in the Forcepoint Web Security Cloud Help.
