Private access policy overview
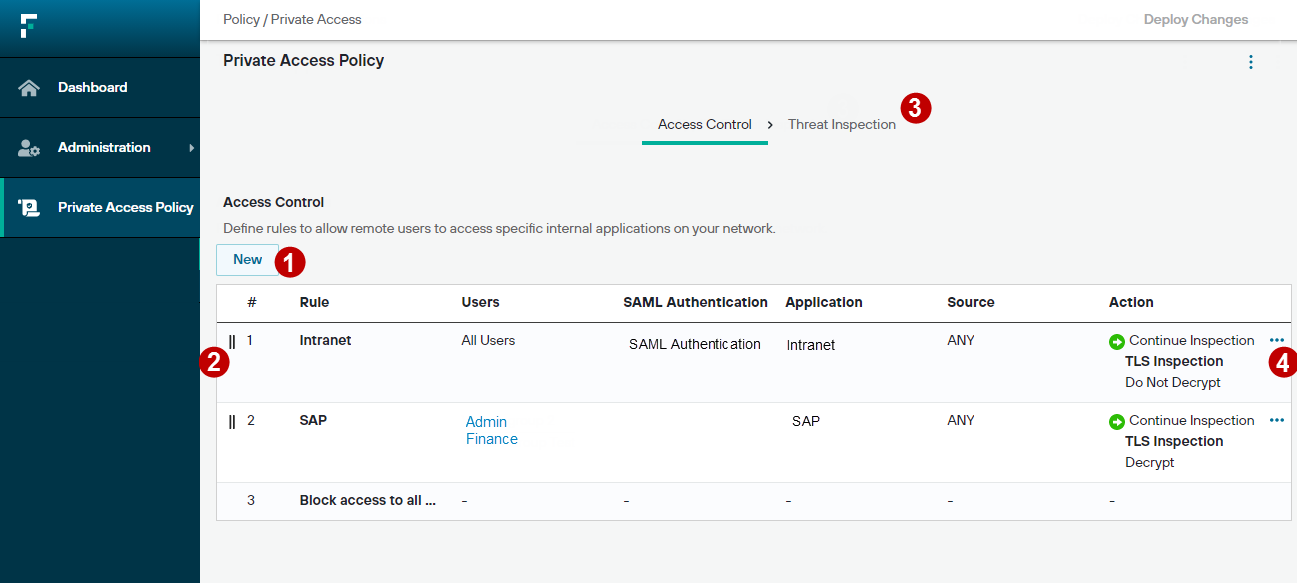
Private access policy rules identify and authenticate the users that are permitted to access your private applications, and filter incoming traffic based on its source IP address. Traffic decryption and threat inspection can be used to identify potential threat signatures in private application traffic.
- 1
- New: create a new rule.
- 2
- Drag to move: use the
 handle to re-order rules in the list. Rules are processed in priority order. The first match found is
applied, and no further rules are checked.
handle to re-order rules in the list. Rules are processed in priority order. The first match found is
applied, and no further rules are checked. - 3
- Threat inspection tab: define the threat category rules and threat exceptions used for deep packet inspection of private application traffic.
- 4
- Rule menu: used to delete rules, or to add new rules before or after the selected rule.