View reports
Before you begin
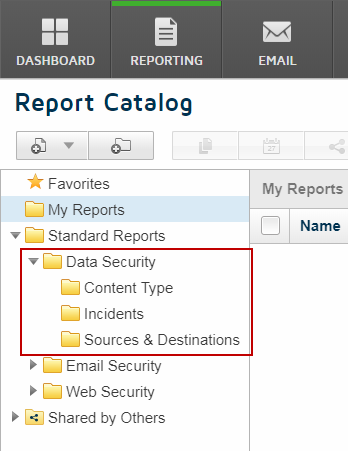
For a more granular view, access the data security reports.
Steps
| Report | Description |
|---|---|
| Content Type | |
| Compliance Summary | Details the compliance rules are most often violated in your organization, and provides a breakdown of the incident count for each policy or rule. |
| Custom Classifier Summary | Shows which custom classifiers triggered the most incidents during the designated period. |
| Data Theft Summary | A list of data theft classifiers that triggered the most incidents during the designated period. |
| Incidents | |
| Incident List | A list or chart of all data loss incidents that were detected during the designated period, along with incident details such as the destination, severity, and transaction size. |
| Sources & Destinations | |
| Destination Summary | The destination URLs or IP addresses involved with the most violations, broken down by severity. |
| Users Summary | The users, machines, or IP addresses most frequently violating data security policies and the severity of their breaches. |
 .
.