Keycloak User Federation Configuration (LDAP/AD)
How to configure a User Federation in Keycloak.
Steps
-
To authorize users for the Forcepoint DSPM dashboard (not Keycloak itself), ensure that the gv realm selected in the top left, not master
(unless the aim is to authorize LDAP users to use Keycloak):
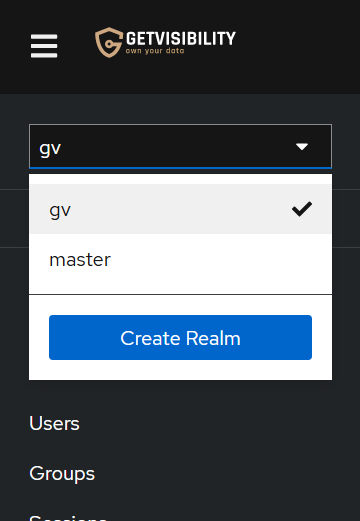
-
Click on the User Federation menu item on the left pane. This should load a list of configured user federations (none at first).
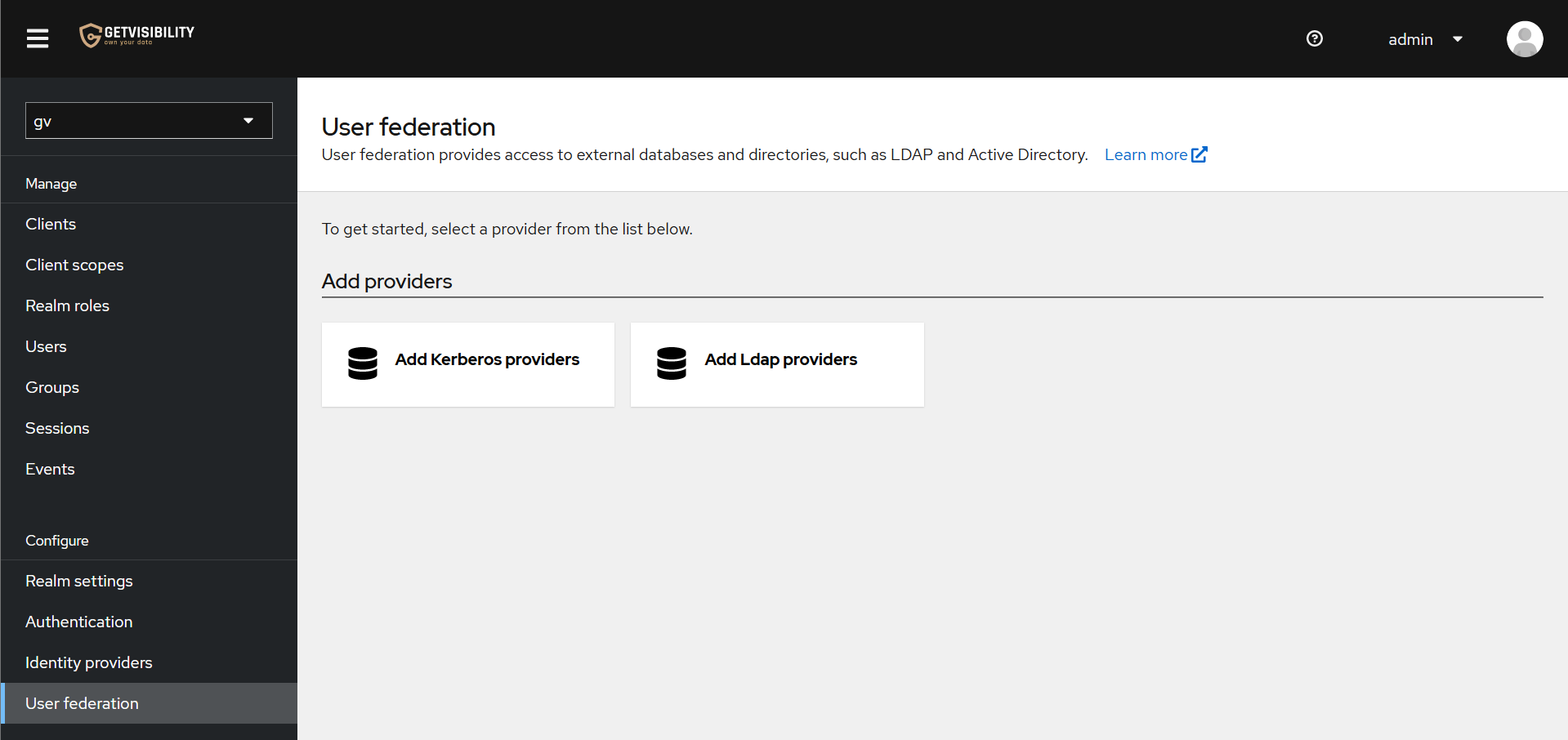
-
Click on Add Ldap providers to load the LDAP (Lightweight Directory Access Protocol) configuration.
-
Update the Connection URL field to reflect the LDAP server address where the Active Directory is hosted.

-
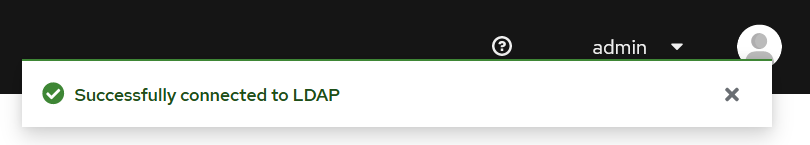
Click on the button Test connection to test the connection from the Keycloak instance to the LDAP server address.
This should succeed quickly. If it hangs, the LDAP server (i.e. a domain controller) may be blocking connections from the Keycloak server address (i.e. the IP of the server running the Forcepoint DSPM). The Public IP address of the LDAP server may need to be used.
-
Update the Bind DN field to reflect the user used to access the LDAP server. In this case, the user with username “admin” from the domain “domain.com”.
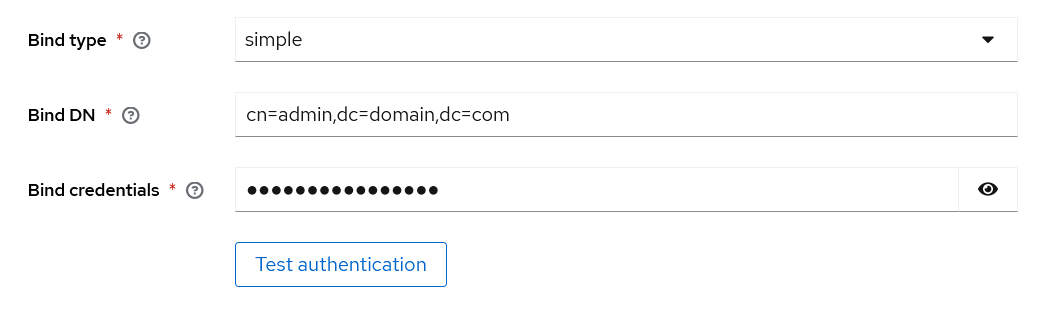
For Active Directory, the value for the Bind DN field could be
serviceaccount@MY-AD-DC.LOCAL. - Update the Bind credentials field (see the above image) to contain the password used to access the LDAP server.
-
Click Test authentication to confirm that the provided credentials work as expected:

-
Update the Users DN field to contain the Full DN of the LDAP tree where your users are.
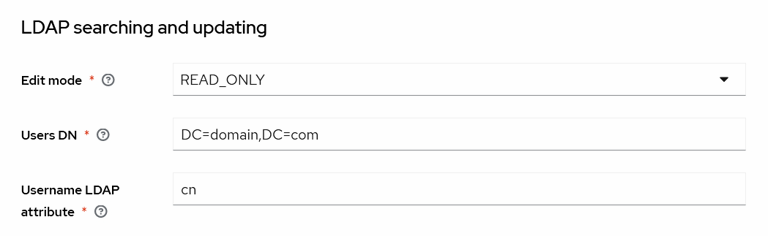 Note:
Note:- The above value for the “Users DN” field will import all users to the gv realm. All users within the “domain.com” domain will get full administrative access for the Forcepoint DSPM dashboard.
- If this is not desired, make restrictions to which users are imported, e.g.
CN=MyGroup,OU=Users,DC=MyDomain,DC=com - For AD Server federation, some may prefer to configure the Username LDAP attribute as sAMAccountName or userPrincipalName. See User Naming Attributes - Win32 apps and Active Directory LDAP Field Mappings.
-
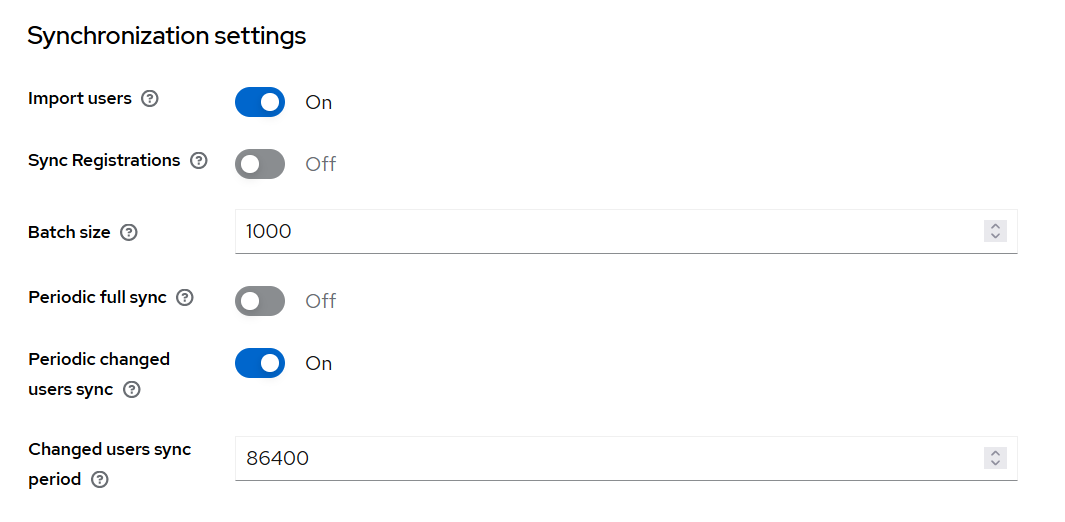
(Optional) Within Synchronization settings, set up automatic synchronization of users from the LDAP Active Directory to Keycloak.
Here the auto-synchronization settings can be configured.
-
Click the Save button at the bottom of the screen.
