Create Custom Profile
The Create Profile editor can be used to create custom profiles. If the administrator wants, then they can select the Inherit default profile option provided with each widget to apply the values from the default profile.
Profile details
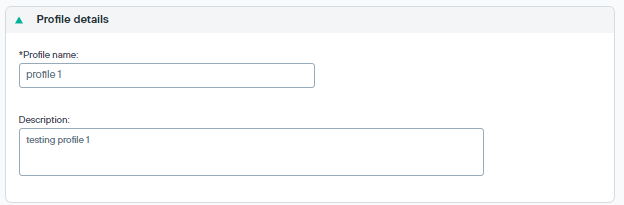
Profile name: Each profile is stored using the provided name.
Description: Brief description of the profile.
Applies to:
Use this section to define the scope to exclude or include in the profile. The scope defines the endpoints or organizational units which should be subjected to this profile.
The selection list is limited to 100 entries. Use search to find additional endpoints or OUs.
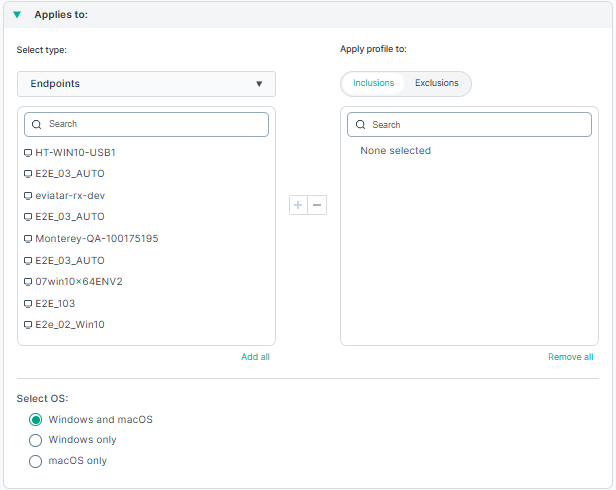
In the Search option, enter the resource name, then click  to add to the list
for either inclusion or exclusion. You can also use the Add all or Remove all options to remove or add multiple entries. Similarly, you can use
the
to add to the list
for either inclusion or exclusion. You can also use the Add all or Remove all options to remove or add multiple entries. Similarly, you can use
the  to remove entries that were added earlier for either exclusion or inclusion.
to remove entries that were added earlier for either exclusion or inclusion.
Also, from the Select OS: option select the operating system running on the endpoint machine.
When including an OU or endpoint in the "Include" list all other OUs and endpoints are excluded. The "Exclude" list overrides the "Include" list. It is used, for example, to select an OU but exclude specific endpoints that belong to this OU.
General
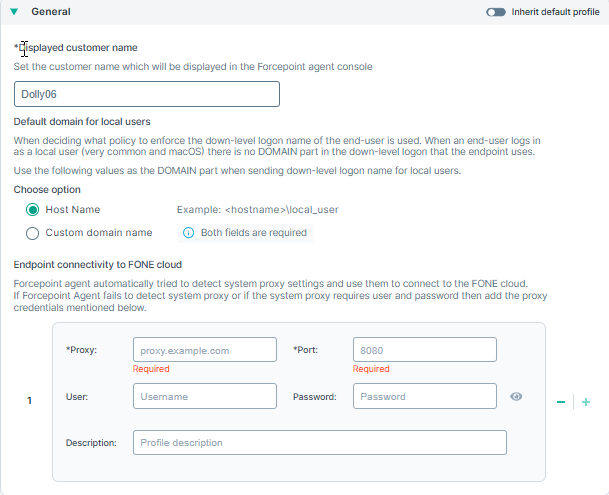
- Displayed customer name: Set the customer name that is displayed on the Forcepoint agent console.
- Default domain for local users: The endpoint uses the down-level logon name of the end user when determining which policy to enforce on web requests. When the
end-user logs in as a local user (common in macOS), there is no domain part in the down-level logon that the endpoint uses. You must enter following:
- Host name
- Custom domain name
- Endpoint connectivity to FONE cloud: Control the endpoint connectivity to the Forcepoint Data Security Cloud | DLP cloud platform. Allows manual configuration of proxy settings for proxies that require authentication.
Customer Logo (Applies to Default Profile Only)
You can add a custom company logo using this widget.
Uploading the Logo
- Click on Select logo to choose and upload the image file.
- After the file explorer opens, browse and select the image you want to upload. Only PNG images of dimensions of 300 x 50 pixels and a maximum size of 50 KB are supported.
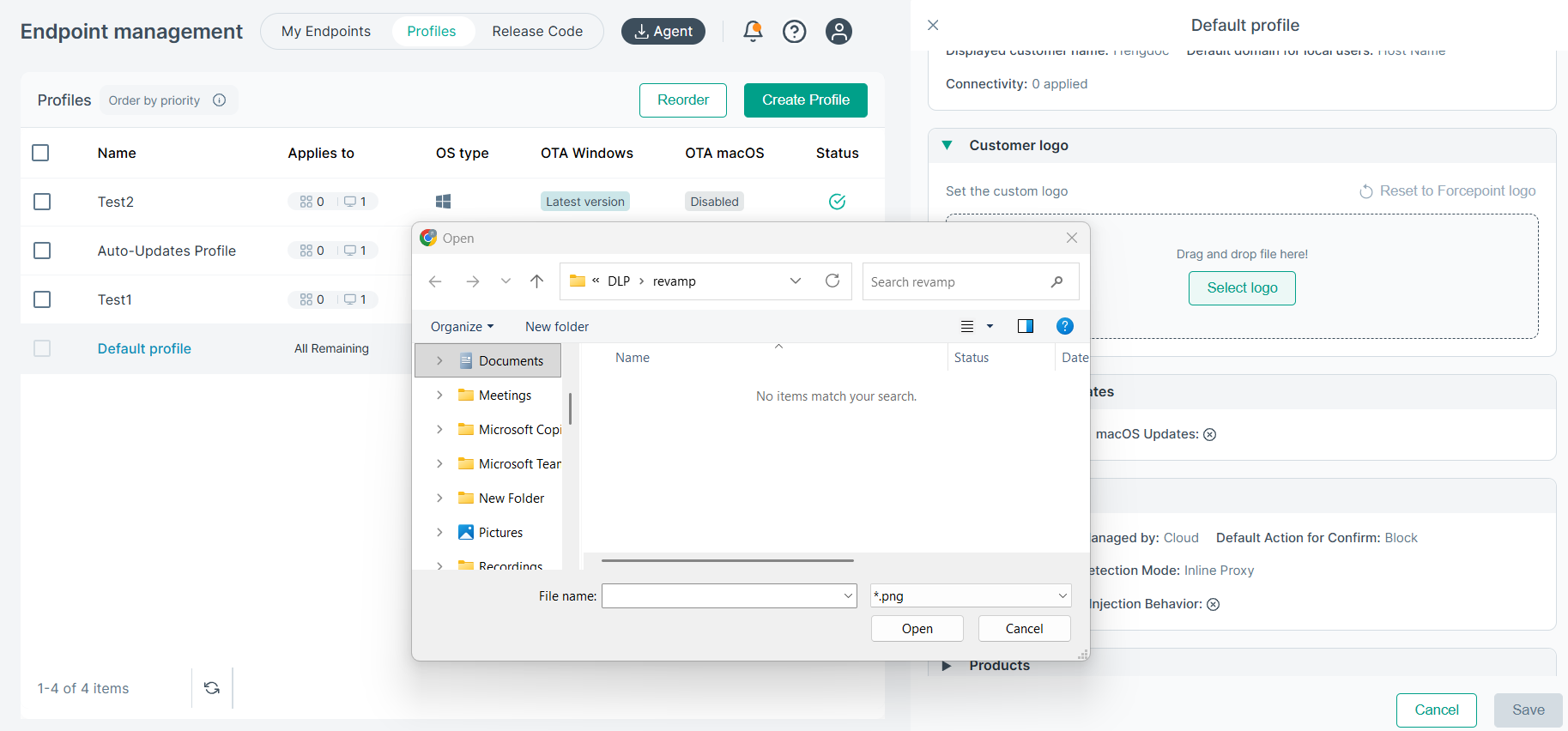
Only one logo is allowed per tenant. Uploading a new logo replaces the previous one.
The uploaded logo will appear both in the agent coaching dialog and in alert email notifications.
- To update or remove the previously uploaded logo, click the Change logo button and upload the new logo.

Over the air updates
Displays which agent software versions are pushed to the endpoints. Values are inherited from default profile settings. Over the air updates can be enabled or disabled from the Default profile. Also, administrators can either opt for automatic updates or select specific agent versions to update from the Default profile. If Update to a specific version is selected, then the drop-down can be used to select the exact agent version of the agent to update to.
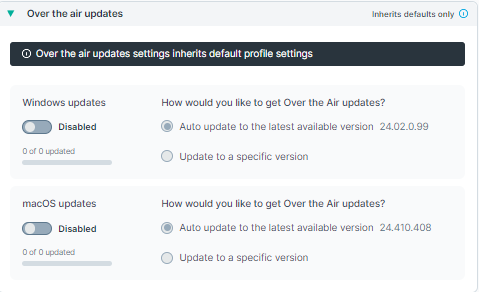
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
Data Protection
The Data Protection widget enables users that have Data Protection license to disable or enable it.
Managed by: The data protection license applies both to On-Prem and SaaS DLP licenses. Those users who have only one of the licenses will see only the respective option (On-Premise or Cloud) under Managed by field. Users that have both the licenses will be able to select whether the profile is managed by On-Premise or Cloud.
Default Action to Confirm: In case, the user does not respond to a confirmation pop up, what action should be taken.
Enforce batch block (Applies to Default Profile Only): When enabled, files are processed as a batch. If one file is blocked, the entire batch is canceled. When disabled, files are processed individually, reducing incident impact but losing full batch context.
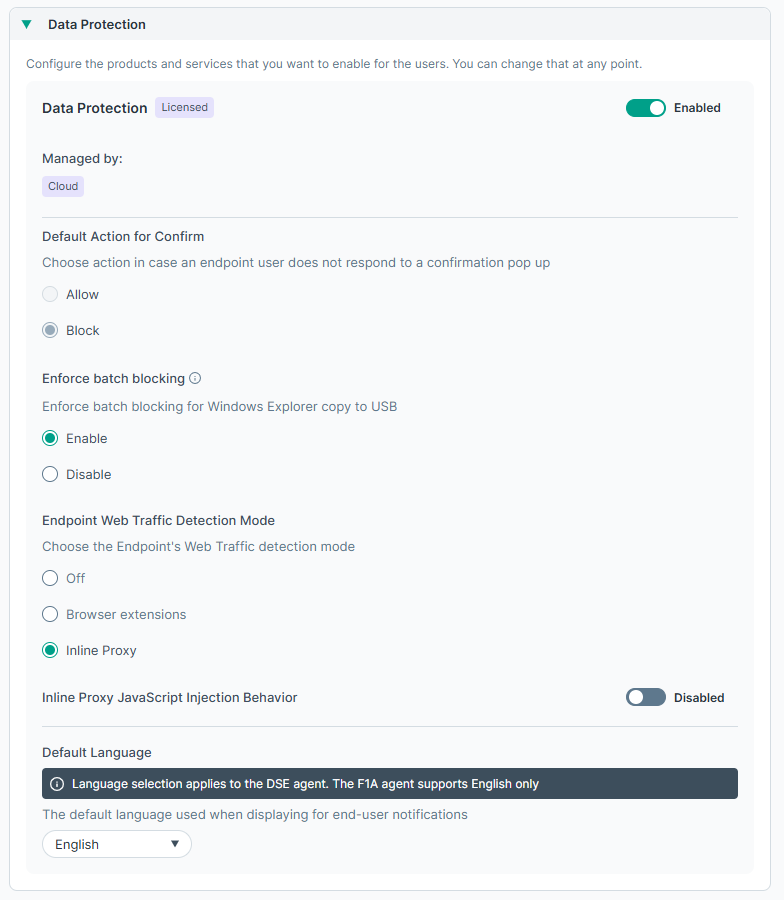
The Endpoint Web Traffic Detection Mode sets whether to use Inline Proxy or Browser Extension. Since the Forcepoint agent currently supports only the Inline Proxy mode, the mode cannot be changed. When support for the Browser Extension mode is enabled for the agent, it will be possible to set the mode.
When the mode is set to Inline Proxy, the Inline Proxy JavaScript Injection Behavior attribute is displayed. Enable it to set the Javascript injection behavior.
You can also learn more about the Inline Proxy capability, from the Inline Proxy FAQ.
When the Inline Proxy JavaScript Injection Behavior attribute is ON, you can set a list of domains in which JavaScript inspection is applied, and a list of domains in which JavaScript inspection is bypassed. The options are:
- If both lists are disabled, no JavaScript Inspection is applied (same behavior as when JavaScript Injection Behavior is OFF).
- If only the Apply JS Injection only to the sites listed list is enabled, JavaScript inspection is applied only to the domains in the list.
- If only the Apply JS Injection on all sites excluding those listed list is enabled, JavaScript inspection is applied to all domains except the domains in the list.
- If both lists are enabled, JavaScript Injection is applied only to domains that are included in the Apply JS Injection only to the sites listed list and not included in the Apply JS Injection to all sites excluding those listed list.
In the following field, enter the domains that should be detecting file uploads by JavaScript injection or should not be detecting file uploads by JavaScript injection.
You can also import the domains via a comma separated .csv file. The format of the domains file should be like the following example:
domain1.com, domain2.com, domain3.com, domain4.com
domain5.com, domain6.co.il
Products
Lists the features available and the license requirements.
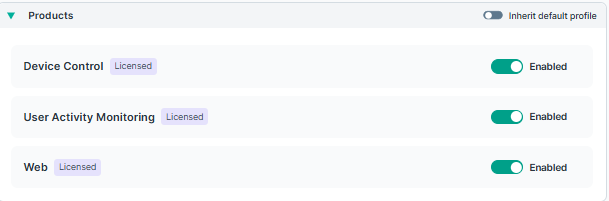
- Device Control
- User activity monitoring
- Neo web
If the customer does not have a license for one of the above products, the respective enable/disable toggle will be disabled.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
Application Monitoring
Administrators can select applications whose traffic should be monitored for Windows or macOS endpoints. Currently, only the Forcepoint Data Security Cloud agent is supported.
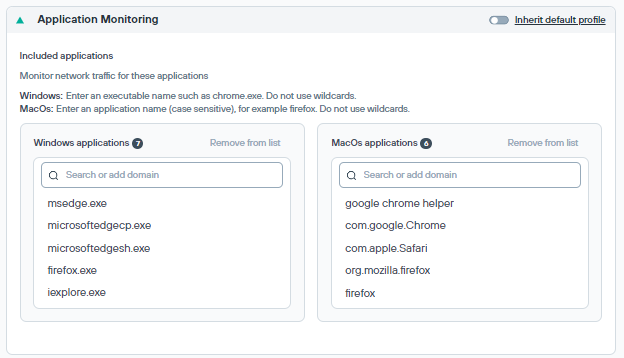
- For Windows, enter an executable name such as chrome.exe.
- For macOS, enter an application name, for example Firefox.
- Do not use wildcards.
Select the application name from the list and click Remove from list to remove the application.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
Application Bypass
Administrators can exclude applications whose traffic should not be monitored for endpoints running Windows or macOS. Currently, supported only with Forcepoint Data Security Cloud agent.
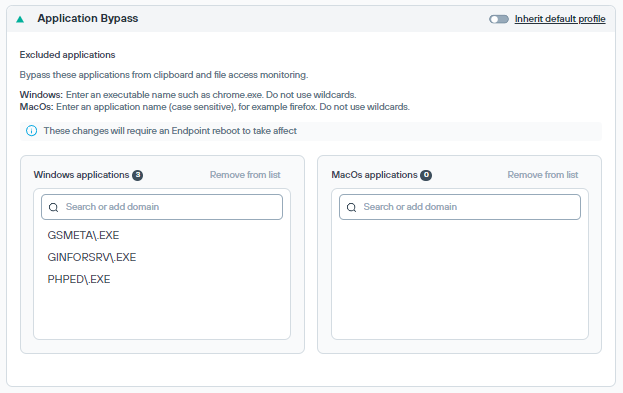
In the Search option, enter the application name, then click Add <app> to list to add applications to the list.
- For Windows, enter an executable name such as chrome.exe.
- For macOS, enter an application name, for example Firefox.
- Do not use wildcards.
Select the application name from the list and click Remove from list to remove the application.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
Traffic Monitoring
Administrators can control all of the following from the Traffic Monitoring widget.
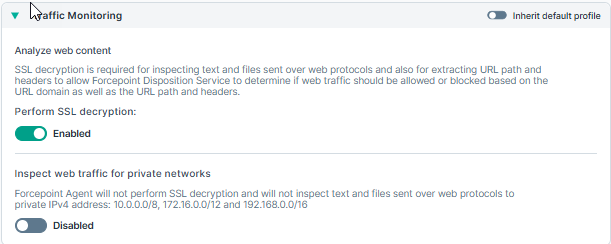
Analyze web content: SSL decryption is required for inspecting text and files sent over web protocols and also for extracting URL path and headers to allow the Forcepoint Disposition Service to determine if web traffic should be allowed or blocked based on the URL domain as well as the URL path and headers.
Perform SSL decryption: The toggle button can be enabled or disabled for SSL decryption of web traffic.
Inspect web traffic for private networks: The endpoint will not perform SSL decryption and will not inspect text and files sent over web protocols to private IPv4 address: 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
SSL Inspection
Administrators can add domains that should not be SSL decrypted when endpoint inline proxy mode is enabled. Currently, supported only with Forcepoint Data Security Cloud agent.
Use the toggle button to enable or disable the SSL Inspection Bypass.
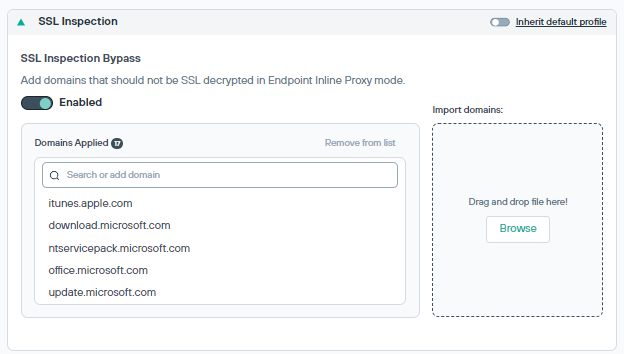
Enter the domain name in the search option and click the search icon and then click Add <domain> to list or you can drag and drop or browse a .txt file with comma-separated domains to add domains to the list.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.
Intercept web traffic
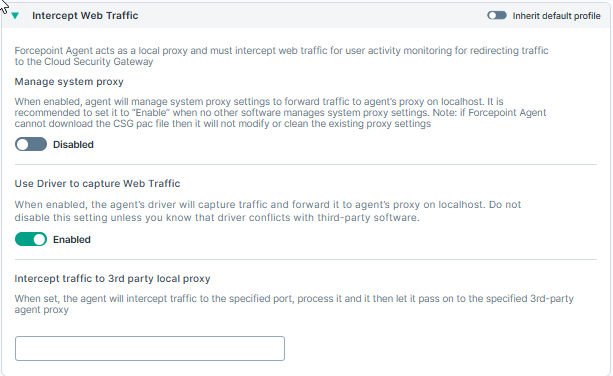
Intercept web traffic : The agent acts as a local proxy and must intercept web traffic for user activity monitoring and for redirecting traffic to the Forcepoint Cloud Security Gateway.
Manage system proxy: When enabled, the agent will manage the system proxy settings to forward traffic to the agent's proxy on localhost. It is recommended to set it to Enable when no other software manages system proxy settings.
Use Driver to capture Web Traffic: When enabled, the agent driver captures web traffic and forwards it to the agent local proxy on localhost. Set the IP or port number if the agent will forward traffic to the third-party agent running on the specified IP or Ports. Currently, supported only with Forcepoint Data Security Cloud agent.
Administrators can choose to enable the option Inherit default profile if they want to inherit the settings from the default profile.